Our pass rate is high to 98.9% and the similarity percentage between our 156-215.80 Exam Questions and Answers and real exam is 90% based on our seven-year educating experience. Do you want achievements in the 156-215.80 exam in just one try? I am currently studying for the 156-215.80 Exam Dumps. Latest 156-215.80 Dumps, Try 156-215.80 Brain Dumps First.
Online 156-215.80 free questions and answers of New Version:
NEW QUESTION 1
The Gaia operating system supports which routing protocols?
- A. BGP, OSPF, RIP
- B. BGP, OSPF, EIGRP, PIM, IGMP
- C. BGP, OSPF, RIP, PIM, IGMP
- D. BGP, OSPF, RIP, EIGRP
Answer: A
Explanation: The Advanced Routing Suite
The Advanced Routing Suite CLI is available as part of the Advanced Networking Software Blade.
For organizations looking to implement scalable, fault-tolerant, secure networks, the Advanced Networking blade enables them to run industry-standard dynamic routing protocols including BGP, OSPF, RIPv1, and RIPv2 on security gateways. OSPF, RIPv1, and RIPv2 enable dynamic routing over a single autonomous system—like a single department, company, or service provider—to avoid network failures. BGP provides dynamic routing support across more complex networks involving multiple autonomous systems—such as when a company uses two service providers or divides a network into multiple areas with different administrators responsible for the performance of each.
NEW QUESTION 2
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
- A. SmartDashboard
- B. SmartUpdate
- C. SmartView Status
- D. SmartView Tracker
Answer: D
NEW QUESTION 3
What command would show the API server status?
- A. cpm status
- B. api restart
- C. api status
- D. show api status
Answer: D
NEW QUESTION 4
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
- A. Only the objects being modified in the Management Database and other administrators can connect to make changes using a special session as long as they all connect from the same LAN network.
- B. The entire Management Database and other administrators can connect to make changes only if the first administrator switches to Read-only.
- C. The entire Management Database and all sessions and other administrators can connect only as Read-only.
- D. Only the objects being modified in his session of the Management Database and other administrators can connect to make changes using different sessions.
Answer: D
NEW QUESTION 5
The IT Management team is interested in the new features of the Check Point R80 Management and wants to upgrade but they are concerned that the existing R77.30 Gaia Gateways cannot be managed by R80 because it is so different. As the administrator responsible for the Firewalls, how can you answer or confirm these concerns?
- A. R80 Management contains compatibility packages for managing earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
- B. R80 Management requires the separate installation of compatibility hotfix packages for managing the earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
- C. R80 Management was designed as a completely different Management system and so can only monitor Check Point Gateways prior to R80.
- D. R80 Management cannot manage earlier versions of Check Point Gateways prior to R80. Only R80 and above Gateways can be manage
- E. Consult the R80 Release Notes for more information.
Answer: A
NEW QUESTION 6
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
- A. Firewall
- B. Application Control
- C. Anti-spam and Email Security
- D. Antivirus
Answer: D
Explanation: The enhanced Check Point Antivirus Software Blade uses real-time virus signatures and anomaly-based protections from ThreatCloud™, the first collaborative network to fight cybercrime, to detect and block malware at the gateway before users are affected.
NEW QUESTION 7
Fill in the blanks: VPN gateways authenticate using _____ and ______.
- A. Passwords; tokens
- B. Certificates; pre-shared secrets
- C. Certificates; passwords
- D. Tokens; pre-shared secrets
Answer: B
Explanation: VPN gateways authenticate using Digital Certificates and Pre-shared secrets.
NEW QUESTION 8
Fill in the blanks: A High Availability deployment is referred to as a ____ cluster and a Load Sharing deployment is referred to as a _____ cluster.
- A. Standby/standby; active/active
- B. Active/active; standby/standby
- C. Active/active; active/standby;
- D. Active/standby; active/active
Answer: D
Explanation: In a High Availability cluster, only one member is active (Active/Standby operation).
ClusterXL Load Sharing distributes traffic within a cluster so that the total throughput of multiple members is increased. In Load Sharing configurations, all functioning members in the cluster are active, and handle network traffic (Active/Active operation).
NEW QUESTION 9
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
- A. backup
- B. Database Revision
- C. snapshot
- D. migrate export
Answer: C
Explanation: 2. Snapshot Management
The snapshot creates a binary image of the entire root (lv_current) disk partition. This includes Check Point products, configuration, and operating system.
Starting in R77.10, exporting an image from one machine and importing that image on another machine of the same type is supported.
The log partition is not included in the snapshot. Therefore, any locally stored FireWall logs will not be save
NEW QUESTION 10
Fill in the blank; The position of an Implied rule is manipulated in the _____ window
- A. NAT
- B. Firewall
- C. Global Properties
- D. Object Explorer
Answer: C
NEW QUESTION 11
Which command is used to obtain the configuration lock in Gaia?
- A. Lock database override
- B. Unlock database override
- C. Unlock database lock
- D. Lock database user
Answer: A
Explanation: Obtaining a Configuration Lock
lock database override
unlock database
NEW QUESTION 12
Tina is a new administrator who is currently reviewing the new Check Point R80 Management console interface. In the Gateways view, she is reviewing the Summary screen as in the screenshot below. What as an 'Open Server'?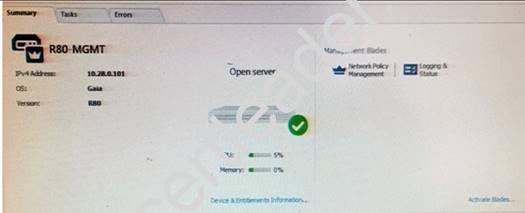
- A. Check Point software deployed on a non-Check Point appliance.
- B. The Open Server Consortium approved Server Hardware used for the purpose of Security and Availability.
- C. A check Point Management Server deployed using the Open Systems Interconnection (OSI) Server andSecurity deployment model.
- D. A check Point Management Server software using the Open SSL.
Answer: A
Explanation: 
Topic 2, Exam Pool B
NEW QUESTION 13
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _______
- A. User data base corruption
- B. LDAP conflicts
- C. Traffic issues
- D. Phase two key negotiation
Answer: C
Explanation: Check Point's FW Monitor is a powerful built-in tool for capturing network traffic at the packet level. The Monitor utility captures network packets at multiple capture points along the FireWall inspection chains. These captured packets can be inspected later using the WireShark
NEW QUESTION 14
Which of the following is NOT a tracking option?
- A. Partial log
- B. Log
- C. Network log
- D. Full log
Answer: A
NEW QUESTION 15
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
- A. Six times per day
- B. Seven times per day
- C. Every two hours
- D. Every three hours
Answer: D
NEW QUESTION 16
Which GUI tool can be used to view and apply Check Point licenses?
- A. cpconfig
- B. Management Command Line
- C. SmartConsole
- D. SmartUpdate
Answer: D
Explanation: SmartUpdate GUI is the recommended way of managing licenses. References:
NEW QUESTION 17
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
- A. John should install the identity Awareness Agent
- B. The firewall admin should install the Security Policy
- C. John should lock and unlock the computer
- D. Investigate this as a network connectivity issue
Answer: C
100% Valid and Newest Version 156-215.80 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/156-215.80/ (New 440 Q&As)
