Cause all that matters here is passing exam with 156-215.80 Exam Dumps. Cause all that you need is a high score of 156-215.80 Exam Questions. The only one thing you need to do is downloading 156-215.80 Exam Dumps free now. We will not let you down with our money-back guarantee.
Online 156-215.80 free dumps demo Below:
NEW QUESTION 1
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?
- A. Create a new logical-server object to represent your partner's CA
- B. Exchange exported CA keys and use them to create a new server object to represent your partner's Certificate Authority (CA)
- C. Manually import your partner's Certificate Revocation List.
- D. Manually import your partner's Access Control List.
Answer: B
NEW QUESTION 2
What is the purpose of Priority Delta in VRRP?
- A. When a box is up, Effective Priority = Priority + Priority Delta
- B. When an Interface is up, Effective Priority = Priority + Priority Delta
- C. When an Interface fails, Effective Priority = Priority - Priority Delta
- D. When a box fails, Effective Priority = Priority - Priority Delta
Answer: C
NEW QUESTION 3
What is the BEST method to deploy identity Awareness for roaming users?
- A. Use Office Mode
- B. Use identity agents
- C. Share user identities between gateways
- D. Use captive portal
Answer: A
NEW QUESTION 4
WeBControl Layer has been set up using the settings in the following dialogue: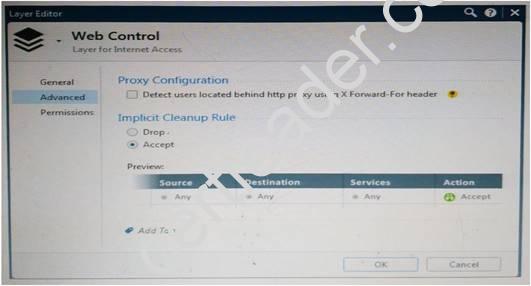
Consider the following policy and select the BEST answer.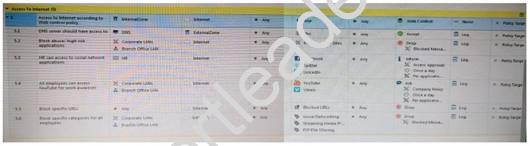
- A. Traffic that does not match any rule in the subpolicy is dropped.
- B. All employees can access only Youtube and Vimeo.
- C. Access to Youtube and Vimeo is allowed only once a day.
- D. Anyone from internal network can access the internet, expect the traffic defined in drop rules 5.2, 5.5 and 5.6.
Answer: D
Explanation: Policy Layers and Sub-Policies
R80 introduces the concept of layers and sub-policies, allowing you to segment your policy according to your network segments or business units/functions. In addition, you can also assign granular privileges by layer or sub-policy to distribute workload and tasks to the most qualified administrators
With layers, the rule base is organized into a set of security rules. These set of rules or layers, are inspected in the order in which they are defined, allowing control over the rule base flow and the security functionalities that take precedence. If an “accept” action is performed across a layer, the inspection will continue to the next layer. For example, a compliance layer can be created to overlay across a cross-section of rules.
Sub-policies are sets of rules that are created for a specific network segment, branch office or business unit, so if a rule is matched, inspection will continue through this subset of rules before it moves on to the next rule.
Sub-policies and layers can be managed by specific administrators, according to their permissions profiles. This facilitates task delegation and workload distribution.
NEW QUESTION 5
Where can administrator edit a list of trusted SmartConsole clients in R80?
- A. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
- B. Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
- C. In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients.
- D. WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients, via cpconfig on a Security Gateway.
Answer: C
NEW QUESTION 6
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
- A. Any size
- B. Less than 20GB
- C. More than 10GB and less than 20 GB
- D. At least 20GB
Answer: D
NEW QUESTION 7
Which command can you use to verify the number of active concurrent connections?
- A. fw conn all
- B. fw ctl pst pstat
- C. show all connections
- D. show connections
Answer: B
NEW QUESTION 8
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
- A. vpn tu
- B. vpn ipsec remove -l
- C. vpn debug ipsec
- D. fw ipsec tu
Answer: A
Explanation: vpn tu
Description Launch the TunnelUtil tool which is used to control VPN tunnels.
Usage vpn tu vpn tunnelutil Example vpn tu Output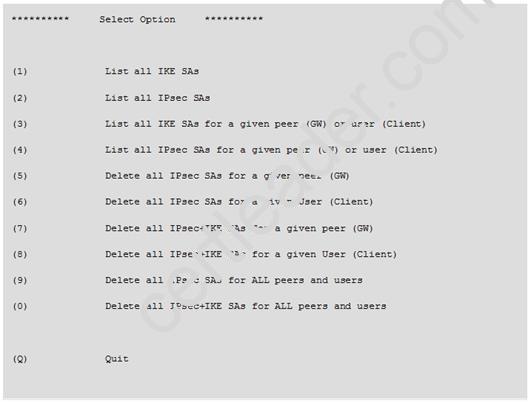
NEW QUESTION 9
Which Threat Prevention Software Blade provides comprehensive against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
- A. Anti-Virus
- B. IPS
- C. Anti-Spam
- D. Anti-bot
Answer: B
Explanation: The IPS Software Blade provides a complete Intrusion Prevention System security solution, providing comprehensive network protection against malicious and unwanted network traffic, including:
Malware attacks
Dos and DDoS attacks
Application and server vulnerabilities
Insider threats
Unwanted application traffic, including IM and P2P
NEW QUESTION 10
Choose what BEST describes a Session.
- A. Starts when an Administrator publishes all the changes made on SmartConsole.
- B. Starts when an Administrator logs in to the Security Management Server through SmartConsole and ends when it is published.
- C. Sessions ends when policy is pushed to the Security Gateway.
- D. Sessions locks the policy package for editing.
Answer: B
Explanation: Administrator Collaboration
More than one administrator can connect to the Security Management Server at the same time. Every administrator has their own username, and works in a session that is independent of the other administrators.
When an administrator logs in to the Security Management Server through SmartConsole, a new editing session starts. The changes that the administrator makes during the session are only available to that administrator. Other administrators see a lock icon on object and rules that are being edited.
To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
NEW QUESTION 11
What is the difference between an event and a log?
- A. Events are generated at gateway according to Event Policy
- B. A log entry becomes an event when it matches any rule defined in Event Policy
- C. Events are collected with SmartWorkflow from Trouble Ticket systems
- D. Logs and Events are synonyms
Answer: B
NEW QUESTION 12
Fill in the blank: The R80 SmartConsole, SmartEvent GUI client, and _____ consolidate billions of logs and shows them as prioritized security events.
- A. SmartMonitor
- B. SmartView Web Application
- C. SmartReporter
- D. SmartTracker
Answer: B
Explanation: Event Analysis with SmartEvent
The SmartEvent Software Blade is a unified security event management and analysis solution that delivers real-time, graphical threat management information. SmartConsole, SmartView Web Application, and the SmartEvent GUI client consolidate billions of logs and show them as prioritized security events so you can immediately respond to security incidents, and do the necessary actions to prevent more attacks. You can customize the views to monitor the events that are most important to you. You can move from a high level view to detailed forensic analysis in a few clicks. With the free-text search and suggestions, you can quickly run data analysis and identify critical security events.
NEW QUESTION 13
Which back up utility captures the most information and tends to create the largest archives?
- A. backup
- B. snapshot
- C. Database Revision
- D. migrate export
Answer: B
NEW QUESTION 14
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the most likely reason that the traffic is not accelerated?
- A. There is a virus foun
- B. Traffic is still allowed but not accelerated
- C. The connection required a Security server
- D. Acceleration is not enabled
- E. The traffic is originating from the gateway itself
Answer: D
NEW QUESTION 15
Which of the following statements is TRUE about R80 management plug-ins?
- A. The plug-in is a package installed on the Security Gateway.
- B. Installing a management plug-in requires a Snapshot, just like any upgrade process.
- C. A management plug-in interacts with a Security Management Server to provide new features and support for new products.
- D. Using a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
Answer: C
NEW QUESTION 16
You can see the following graphic: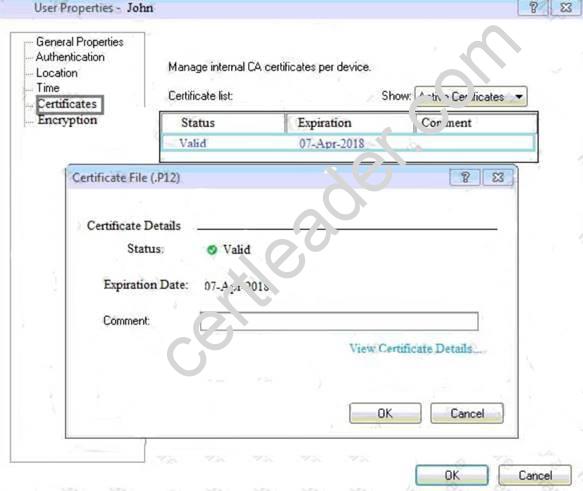
What is presented on it?
- A. Properties of personal .p12 certificate file issued for user John.
- B. Shared secret properties of John’s password.
- C. VPN certificate properties of the John’s gateway.
- D. Expired .p12 certificate properties for user John.
Answer: A
NEW QUESTION 17
You want to reset SIC between smberlin and sgosaka.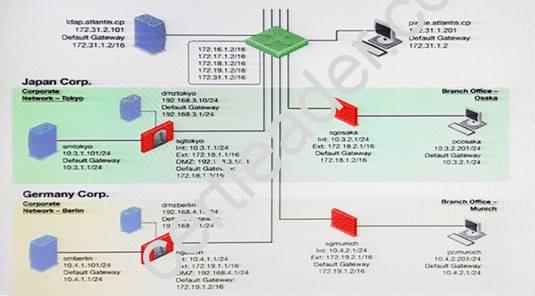
In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message:
What is the reason for this behavior?
- A. The Gateway was not rebooted, which is necessary to change the SIC key.
- B. You must first initialize the Gateway object in SmartDashboard (i.e., right-click on the object, choose Basic Setup > Initialize).
- C. The check Point services on the Gateway were not restarted because you are still in the cpconfig utility.
- D. The activation key contains letters that are on different keys on localized keyboard
- E. Therefore, the activation can not be typed in a matching fashion.
Answer: C
Recommend!! Get the Full 156-215.80 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/156-215.80/ (New 440 Q&As Version)
