Proper study guides for 156-215.80 Check Point Certified Security Administrator certified begins with 156-215.80 Exam Questions and Answers preparation products which designed to deliver the 156-215.80 Exam Dumps by making you pass the 156-215.80 test at your first time. Try the free 156-215.80 Study Guides right now.
Check 156-215.80 free dumps before getting the full version:
NEW QUESTION 1
What does ExternalZone represent in the presented rule?
- A. The Internet.
- B. Interfaces that administrator has defined to be part of External Security Zone.
- C. External interfaces on all security gateways.
- D. External interfaces of specific gateways.
Answer: B
Explanation: Configuring Interfaces
Configure the Security Gateway 80 interfaces in the Interfaces tab in the Security Gateway window. To configure the interfaces:
From the Devices window, double-click the Security Gateway 80.
The Security Gateway
window opens.
Select the Interfaces tab.
Select Use the following settings. The interface settings open.
Select the interface and click Edit.
The Edit window opens.
From the IP Assignment section, configure the IP address of the interface:
Select Static IP.
Enter the IP address and subnet mask for the interface.
In Security Zone, select Wireless, DMS, External, or Internal. Security zone is a type of zone, created by a bridge to easily create segments, while maintaining IP addresses and router configurations. Security zones let you choose if to enable or not the firewall between segments.
References:
NEW QUESTION 2
How many packets does the IKE exchange use for Phase 1 Main Mode?
- A. 12
- B. 1
- C. 3
- D. 6
Answer: D
NEW QUESTION 3
Which of the following is TRUE about the Check Point Host object?
- A. Check Point Host has no routing ability even if it has more than one interface installed.
- B. When you upgrade to R80 from R77.30 or earlier versions, Check Point Host objects are converted to gateway objects.
- C. Check Point Host is capable of having an IP forwarding mechanism.
- D. Check Point Host can act as a firewall.
Answer: A
Explanation: A Check Point host is a host with only one interface, on which Check Point software has been installed, and which is managed by the Security Management server. It is not a routing mechanism and is not capable of IP forwarding.
NEW QUESTION 4
In which deployment is the security management server and Security Gateway installed on the same appliance?
- A. Bridge Mode
- B. Remote
- C. Standalone
- D. Distributed
Answer: C
Explanation: Installing Standalone
Standalone Deployment - The Security Management Server and the Security Gateway are installed on the same computer or appliance.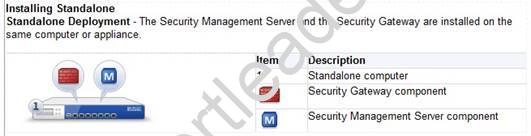
NEW QUESTION 5
NAT can NOT be configured on which of the following objects?
- A. HTTP Logical Server
- B. Gateway
- C. Address Range
- D. Host
Answer: A
NEW QUESTION 6
What is also referred to as Dynamic NAT?
- A. Automatic NAT
- B. Static NAT
- C. Manual NAT
- D. Hide NAT
Answer: D
NEW QUESTION 7
R80.10 management server can manage gateways with which versions installed?
- A. Versions R77 and higher
- B. Versions R76 and higher
- C. Versions R75.20 and higher
- D. Version R75 and higher
Answer: B
NEW QUESTION 8
SmartEvent does NOT use which of the following procedures to identity events:
- A. Matching a log against each event definition
- B. Create an event candidate
- C. Matching a log against local exclusions
- D. Matching a log against global exclusions
Answer: C
NEW QUESTION 9
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John request when he cannot access the web server from his laptop?
- A. John should lock and unlock his computer
- B. Investigate this as a network connectivity issue
- C. The access should be changed to authenticate the user instead of the PC
- D. John should install the Identity Awareness Agent
Answer: C
NEW QUESTION 10
When a packet arrives at the gateway, the gateway checks it against the rules in the top Policy Layer, sequentially from top to bottom, and enforces the first rule that matches a packet. Which of the following statements about the order of rule enforcement is true?
- A. If the Action is Accept, the gateway allows the packet to pass through the gateway.
- B. If the Action is Drop, the gateway continues to check rules in the next Policy Layer down.
- C. If the Action is Accept, the gateway continues to check rules in the next Policy Layer down.
- D. If the Action is Drop, the gateway applies the Implicit Clean-up Rule for that Policy Layer.
Answer: C
NEW QUESTION 11
Which Threat Prevention Profile is not included by default in R80 Management?
- A. Basic – Provides reliable protection on a range of non-HTTP protocols for servers, with minimal impact on network performance
- B. Optimized – Provides excellent protection for common network products and protocols against recent or popular attacks
- C. Strict – Provides a wide coverage for all products and protocols, with impact on network performance
- D. Recommended – Provides all protection for all common network products and servers, with impact on network performance
Answer: D
NEW QUESTION 12
Which of the following uses the same key to decrypt as it does to encrypt?
- A. Asymmetric encryption
- B. Dynamic encryption
- C. Certificate-based encryption
- D. Symmetric encryption
Answer: D
NEW QUESTION 13
Which utility allows you to configure the DHCP service on GAIA from the command line?
- A. ifconfig
- B. dhcp_cfg
- C. sysconfig
- D. cpconfig
Answer: C
Explanation: Sysconfig Configuration Options
NEW QUESTION 14
What are the three authentication methods for SIC?
- A. Passwords, Users, and standards-based SSL for the creation of security channels
- B. Certificates, standards-based SSL for the creation of secure channels, and 3DES or AES128 for encryption
- C. Packet Filtering, certificates, and 3DES or AES128 for encryption
- D. Certificates, Passwords, and Tokens
Answer: B
Explanation: Secure Internal Communication (SIC)
Secure Internal Communication (SIC) lets Check Point platforms and products authenticate with each other. The SIC procedure creates a trusted status between gateways, management servers and other Check Point components. SIC is required to install polices on gateways and to send logs between gateways and management servers.
These security measures make sure of the safety of SIC:
Certificates for authentication
Standards-based SSL for the creation of the secure channel
3DES for encryption
References:
NEW QUESTION 15
Anti-Spoofing is typically set up on which object type?
- A. Security Gateway
- B. Host
- C. Security Management object
- D. Network
Answer: A
NEW QUESTION 16
Katie has been asked to do a backup on the Blue Security Gateway. Which command would accomplish this in the Gaia CLI?
- A. Blue > add local backup
- B. Expert&Blue#add local backing
- C. Blue > set backup local
- D. Blue > add backup local
Answer: D
NEW QUESTION 17
What is the benefit of Manual NAT over Automatic NAT?
- A. If you create a new Security Policy, the Manual NAT rules will be transferred to this new policy
- B. There is no benefit since Automatic NAT has in any case higher priority over Manual NAT
- C. You have the full control about the priority of the NAT rules
- D. On IPSO and GAIA Gateways, it is handled in a Stateful manner
Answer: C
Thanks for reading the newest 156-215.80 exam dumps! We recommend you to try the PREMIUM Certleader 156-215.80 dumps in VCE and PDF here: https://www.certleader.com/156-215.80-dumps.html (440 Q&As Dumps)
