Master the 156-215.80 Check Point Certified Security Administrator content and be ready for exam day success quickly with this Passleader 156-215.80 test. We guarantee it!We make it a reality and give you real 156-215.80 questions in our Check-Point 156-215.80 braindumps.Latest 100% VALID Check-Point 156-215.80 Exam Questions Dumps at below page. You can use our Check-Point 156-215.80 braindumps and pass your exam.
Check-Point 156-215.80 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which remote Access Solution is clientless?
- A. Checkpoint Mobile
- B. Endpoint Security Suite
- C. SecuRemote
- D. Mobile Access Portal
Answer: D
NEW QUESTION 2
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
- A. Firewall
- B. Application Control
- C. Anti-spam and Email Security
- D. Antivirus
Answer: D
Explanation:
The enhanced Check Point Antivirus Software Blade uses real-time virus signatures and anomaly-based protections from ThreatCloud™, the first collaborative network to fight cybercrime, to detect and block malware at the gateway before users are affected.
NEW QUESTION 3
What statement is true regarding Visitor Mode?
- A. VPN authentication and encrypted traffic are tunneled through port TCP 443.
- B. Only ESP traffic is tunneled through port TCP 443.
- C. Only Main mode and Quick mode traffic are tunneled on TCP port 443.
- D. All VPN traffic is tunneled through UDP port 4500.
Answer: A
NEW QUESTION 4
Which of the following is NOT an advantage to using multiple LDAP servers?
- A. You achieve a faster access time by placing LDAP servers containing the database at remote sites
- B. Information on a user is hidden, yet distributed across several servers
- C. You achieve compartmentalization by allowing a large number of users to be distributed across several servers
- D. You gain High Availability by replicating the same information on several servers
Answer: B
NEW QUESTION 5
Fill in the blank: Licenses can be added to the License and Contract repository _____.
- A. From the User Center, from a file, or manually
- B. From a file, manually, or from SmartView Monitor
- C. Manually, from SmartView Monitor, or from the User Center
- D. From SmartView Monitor, from the User Center, or from a file
Answer: A
NEW QUESTION 6
Fill in the blanks. There are _____ types of software containers ______
- A. Three; security managemen
- B. Security Gateway and endpoint security.
- C. Three; Security Gateway, endpoint Security, and gateway management.
- D. Two; security management and endpoint security
- E. Two; endpoint security and Security Gateway
Answer: A
NEW QUESTION 7
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
- A. Threat Emulation
- B. Mobile Access
- C. Mail Transfer Agent
- D. Threat Cloud
Answer: C
NEW QUESTION 8
You are unable to login to SmartDashboard. You log into the management server and run #cpwd_admin list with the following output: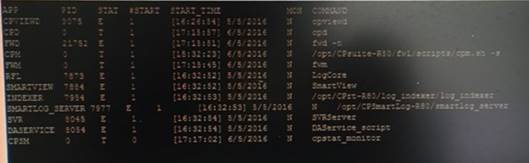
What reason could possibly BEST explain why you are unable to connect to SmartDashboard?
- A. CDP is down
- B. SVR is down
- C. FWM is down
- D. CPSM is down
Answer: C
Explanation:
The correct answer would be FWM (is the process making available communication between SmartConsole applications and Security Management Server.). STATE is T (Terminate = Down)
Symptoms
SmartDashboard fails to connect to the Security Management server.
Verify if the FWM process is running. To do this, run the command:
[Expert@HostName:0]# ps -aux | grep fwm
If the FWM process is not running, then try force-starting the process with the following command: [Expert@HostName:0]# cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm" [Expert@HostName:0]# ps -aux | grep fwm
[Expert@HostName:0]# cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"
NEW QUESTION 9
There are 4 ways to use the Management API for creating host object with R80 Management API. Which one is NOT correct?
- A. Using Web Services
- B. Using Mgmt_cli tool
- C. Using CLISH
- D. Using SmartConsole GUI console
Answer: C
NEW QUESTION 10
Fill in the blank: Once a license is activated, a ____ should be installed.
- A. License Management file
- B. Security Gateway Contract file
- C. Service Contract file
- D. License Contract file
Answer: C
Explanation:
Service Contract File
Following the activation of the license, a Service Contract File should be installed. This file contains important information about all subscriptions purchased for a specific device and is installed via SmartUpdate. A detailed Explanation: of the Service Contract File can be found in sk33089.
NEW QUESTION 11
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
- A. fwd
- B. fwm
- C. cpd
- D. cpwd
Answer: B
NEW QUESTION 12
Which of the following are available SmartConsole clients which can be installed from the R77 Windows CD? Read all answers and select the most complete and valid list.
- A. SmartView Tracker, SmartDashboard, CPINFO, SmartUpdate, SmartView Status
- B. SmartView Tracker, SmartDashboard, SmartLSM, SmartView Monitor
- C. SmartView Tracker, CPINFO, SmartUpdate
- D. Security Policy Editor, Log Viewer, Real Time Monitor GUI
Answer: C
NEW QUESTION 13
Which of the following is NOT an attribute of packer acceleration?
- A. Source address
- B. Protocol
- C. Destination port
- D. Application Awareness
Answer: D
NEW QUESTION 14
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
- A. fw ctl set int fwha vmac global param enabled
- B. fw ctl get int fwha vmac global param enabled; result of command should return value 1
- C. cphaprob –a if
- D. fw ctl get int fwha_vmac_global_param_enabled; result of command should return value 1
Answer: B
NEW QUESTION 15
Which is a suitable command to check whether Drop Templates are activated or not?
- A. fw ctl get int activate_drop_templates
- B. fwaccel stat
- C. fwaccel stats
- D. fw ctl templates –d
Answer: B
NEW QUESTION 16
Office mode means that:
- A. SecureID client assigns a routable MAC addres
- B. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
- C. Users authenticate with an Internet browser and use secure HTTPS connection.
- D. Local ISP (Internet service Provider) assigns a non-routable IP address to the remote user.
- E. Allows a security gateway to assign a remote client an IP addres
- F. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
Answer: D
Explanation:
Office Mode enables a Security Gateway to assign internal IP addresses to SecureClient users. This IP address will not be exposed to the public network, but is encapsulated inside the VPN tunnel between the client and the Gateway. The IP to be used externally should be assigned to the client in the usual way by the Internet Service provider used for the Internet connection. This mode allows a Security Administrator to control which addresses are used by remote clients inside the local network and makes them part of the local network. The mechanism is based on an IKE protocol extension through which the Security Gateway can send an internal IP address to the client.
NEW QUESTION 17
Fill in the blanks: A Check Point software license consists of a _____ and ______.
- A. Software container; software package
- B. Software blade; software container
- C. Software package; signature
- D. Signature; software blade
Answer: B
Explanation:
Check Point's licensing is designed to be scalable and modular. To this end, Check Point offers both predefined packages as well as the ability to custom build a solution tailored to the needs of the Network Administrator. This is accomplished by the use of the following license components:
Software Blades
Container
NEW QUESTION 18
John is using Management HA. Which Smartcenter should be connected to for making changes?
- A. secondary Smartcenter
- B. active Smartcenter
- C. connect virtual IP of Smartcenter HA
- D. primary Smartcenter
Answer: B
NEW QUESTION 19
Fill in the blank; The position of an Implied rule is manipulated in the _____ window
- A. NAT
- B. Firewall
- C. Global Properties
- D. Object Explorer
Answer: C
NEW QUESTION 20
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
- A. A group with generic user
- B. All users
- C. LDAP Account Unit Group
- D. Internal user Group
Answer: A
NEW QUESTION 21
......
P.S. Dumps-files.com now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.dumps-files.com/files/156-215.80/ (485 New Questions)
