We provide real 156-315.80 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Check-Point 156-315.80 Exam quickly & easily. The 156-315.80 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Check-Point 156-315.80 dumps pdf and vce product and material, you can easily pass the 156-315.80 exam.
Check-Point 156-315.80 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
What has to be taken into consideration when configuring Management HA?
- A. The Database revisions will not be synchronized between the management servers
- B. SmartConsole must be closed prior to synchronized changes in the objects database
- C. If you wanted to use Full Connectivity Upgrade, you must change the Implied Rules to allow FW1_cpredundant to pass before the Firewall Control Connections.
- D. For Management Server synchronization, only External Virtual Switches are supporte
- E. So, if you wanted to employ Virtual Routers instead, you have to reconsider your design.
Answer: A
NEW QUESTION 2
Which command collects diagnostic data for analyzing customer setup remotely?
- A. cpinfo
- B. migrate export
- C. sysinfo
- D. cpview
Answer: A
Explanation:
CPInfo is an auto-updatable utility that collects diagnostics data on a customer's machine at the time of execution and uploads it to Check Point servers (it replaces the standalone cp_uploader utility for uploading files to Check Point servers).
The CPInfo output file allows analyzing customer setups from a remote location. Check Point support engineers can open the CPInfo file in a demo mode, while viewing actual customer Security Policies and Objects. This allows the in-depth analysis of customer's configuration and environment settings.
NEW QUESTION 3
In which VPN community is a satellite VPN gateway not allowed to create a VPN tunnel with another satellite VPN gateway?
- A. Pentagon
- B. Combined
- C. Meshed
- D. Star
Answer: D
NEW QUESTION 4
What processes does CPM control?
- A. Object-Store, Database changes, CPM Process and web-services
- B. web-services, CPMI process, DLEserver, CPM process
- C. DLEServer, Object-Store, CP Process and database changes
- D. web_services, dle_server and object_Store
Answer: D
NEW QUESTION 5
Which utility allows you to configure the DHCP service on Gaia from the command line?
- A. ifconfig
- B. dhcp_ofg
- C. sysconfig
- D. cpconfig
Answer: C
NEW QUESTION 6
Which is NOT a SmartEvent component?
- A. SmartEvent Server
- B. Correlation Unit
- C. Log Consolidator
- D. Log Server
Answer: C
NEW QUESTION 7
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
- A. 18210
- B. 18184
- C. 257
- D. 18191
Answer: B
NEW QUESTION 8
If an administrator wants to add manual NAT for addresses now owned by the Check Point firewall, what else is necessary to be completed for it to function properly?
- A. Nothing - the proxy ARP is automatically handled in the R80 version
- B. Add the proxy ARP configurations in a file called /etc/conf/local.arp
- C. Add the proxy ARP configurations in a file called $FWDIR/conf/local.arp
- D. Add the proxy ARP configurations in a file called $CPDIR/conf/local.arp
Answer: D
NEW QUESTION 9
How many policy layers do Access Control policy support?
- A. 2
- B. 4
- C. 1
- D. 3
Answer: A
Explanation:
Two policy layers:
- Network Policy Layer
- Application Control Policy Layer
NEW QUESTION 10
Which Check Point feature enables application scanning and the detection?
- A. Application Dictionary
- B. AppWiki
- C. Application Library
- D. CPApp
Answer: B
NEW QUESTION 11
To optimize Rule Base efficiency, the most hit rules should be where?
- A. Removed from the Rule Base.
- B. Towards the middle of the Rule Base.
- C. Towards the top of the Rule Base.
- D. Towards the bottom of the Rule Base.
Answer: C
NEW QUESTION 12
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all the following except:
- A. Create new dashboards to manage 3rd party task
- B. Create products that use and enhance 3rd party solutions
- C. Execute automated scripts to perform common tasks
- D. Create products that use and enhance the Check Point Solution
Answer: A
Explanation:
Check Point APIs let system administrators and developers make changes to the security policy with CLI tools and web-services. You can use an API to:
• Use an automated script to perform common tasks
• Integrate Check Point products with 3rd party solutions
• Create products that use and enhance the Check Point solution References:
NEW QUESTION 13
Check Point Management (cpm) is the main management process in that it provides the architecture for a consolidates management console. CPM allows the GUI client and management server to communicate via web services using _______ .
- A. TCP port 19009
- B. TCP Port 18190
- C. TCP Port 18191
- D. TCP Port 18209
Answer: A
NEW QUESTION 14
Fill in the blanks. There are________ types of software containers: ________.
- A. Three; security management, Security Gateway, and endpoint security
- B. Three; Security Gateway, endpoint security, and gateway management
- C. Two; security management and endpoint security
- D. Two; endpoint security and Security Gateway
Answer: A
NEW QUESTION 15
The Event List within the Event tab contains:
- A. a list of options available for running a query.
- B. the top events, destinations, sources, and users of the query results, either as a chart or in a tallied list.
- C. events generated by a query.
- D. the details of a selected event.
Answer: C
NEW QUESTION 16
Office mode means that:
- A. SecurID client assigns a routable MAC addres
- B. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
- C. Users authenticate with an Internet browser and use secure HTTPS connection.
- D. Local ISP (Internet service Provider) assigns a non-routable IP address to the remote user.
- E. Allows a security gateway to assign a remote client an IP addres
- F. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
Answer: D
NEW QUESTION 17
Which of the following is NOT an option to calculate the traffic direction?
- A. Incoming
- B. Internal
- C. External
- D. Outgoing
Answer: D
NEW QUESTION 18
Which command is used to obtain the configuration lock in Gaia?
- A. Lock database override
- B. Unlock database override
- C. Unlock database lock
- D. Lock database user
Answer: A
Explanation:
Obtaining a Configuration Lock
NEW QUESTION 19
When using the Mail Transfer Agent, where are the debug logs stored?
- A. $FWDIR/bin/emaild.mt
- B. elg
- C. $FWDIR/log/mtad elg
- D. /var/log/mail.mta elg
- E. $CPDIR/log/emaild elg
Answer: A
NEW QUESTION 20
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
- A. Accounting
- B. Suppression
- C. Accounting/Suppression
- D. Accounting/Extended
Answer: C
NEW QUESTION 21
Where you can see and search records of action done by R80 SmartConsole administrators?
- A. In SmartView Tracker, open active log
- B. In the Logs & Monitor view, select “Open Audit Log View”
- C. In SmartAuditLog View
- D. In Smartlog, all logs
Answer: B
NEW QUESTION 22
What are the methods of SandBlast Threat Emulation deployment?
- A. Cloud, Appliance and Private
- B. Cloud, Appliance and Hybrid
- C. Cloud, Smart-1 and Hybrid
- D. Cloud, OpenServer and Vmware
Answer: A
NEW QUESTION 23
What is the Implicit Clean-up Rule?
- A. A setting is defined in the Global Properties for all policies.
- B. A setting that is configured per Policy Layer.
- C. Another name for the Clean-up Rule.
- D. Automatically created when the Clean-up Rule is defined.
Answer: C
NEW QUESTION 24
View the rule below. What does the lock-symbol in the left column mean? (Choose the BEST answer.)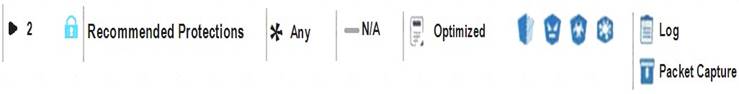
- A. The current administrator has read-only permissions to Threat Prevention Policy.
- B. Another user has locked the rule for editing.
- C. Configuration lock is presen
- D. Click the lock symbol to gain read-write access.
- E. The current administrator is logged in as read-only because someone else is editing the policy.
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_
NEW QUESTION 25
Fill in the blank: The R80 feature _______ permits blocking specific IP addresses for a specified time period.
- A. Block Port Overflow
- B. Local Interface Spoofing
- C. Suspicious Activity Monitoring
- D. Adaptive Threat Prevention
Answer: C
Explanation:
Suspicious Activity Rules Solution
Suspicious Activity Rules is a utility integrated into SmartView Monitor that is used to modify access privileges upon detection of any suspicious network activity (for example, several attempts to gain unauthorized access).
The detection of suspicious activity is based on the creation of Suspicious Activity rules. Suspicious Activity rules are Firewall rules that enable the system administrator to instantly block suspicious connections that are not restricted by the currently enforced security policy. These rules, once set (usually with an expiration date), can be applied immediately without the need to perform an Install Policy operation.
References:
NEW QUESTION 26
GAIA greatly increases operational efficiency by offering an advanced and intuitive software update agent, commonly referred to as the:
- A. Check Point Update Service Engine
- B. Check Point Software Update Agent
- C. Check Point Remote Installation Daemon (CPRID)
- D. Check Point Software Update Daemon
Answer: A
NEW QUESTION 27
Check Point ClusterXL Active/Active deployment is used when:
- A. Only when there is Multicast solution set up.
- B. There is Load Sharing solution set up.
- C. Only when there is Unicast solution set up.
- D. There is High Availability solution set up.
Answer: D
NEW QUESTION 28
Which directory below contains log files?
- A. /opt/CPSmartlog-R80/log
- B. /opt/CPshrd-R80/log
- C. /opt/CPsuite-R80/fw1/log
- D. /opt/CPsuite-R80/log
Answer: C
NEW QUESTION 29
Fill in the blank. Once a certificate is revoked from the Security Gateway by the Security Management Server, the certificate information is ______ .
- A. Sent to the Internal Certificate Authority.
- B. Sent to the Security Administrator.
- C. Stored on the Security Management Server.
- D. Stored on the Certificate Revocation List.
Answer: D
NEW QUESTION 30
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
- A. UDP port 265
- B. TCP port 265
- C. UDP port 256
- D. TCP port 256
Answer: D
Explanation:
Synchronization works in two modes:
Full Sync transfers all Security Gateway kernel table information from one cluster member to another. It is handled by the fwd daemon using an encrypted TCP connection on port 256.
Delta Sync transfers changes in the kernel tables between cluster members. Delta sync is handled by the Security Gateway kernel using UDP connections on port 8116.
NEW QUESTION 31
......
P.S. Easily pass 156-315.80 Exam with 285 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 156-315.80 Dumps: https://www.surepassexam.com/156-315.80-exam-dumps.html (285 New Questions)
