Cause all that matters here is passing the CheckPoint 156-915.77 exam. Cause all that you need is a high score of 156-915.77 Check Point Certified Security Expert Update Blade exam. The only one thing you need to do is downloading Testking 156-915.77 exam study guides now. We will not let you down with our money-back guarantee.
Free demo questions for CheckPoint 156-915.77 Exam Dumps Below:
NEW QUESTION 1
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
- A. Login to Smart Dashboard, access Properties of the SMS, and verify whether Paul’s IP address is listed.
- B. Type cpconfig on the Management Server and select the option “GUI client List” to see if Paul’s IP address is listed.
- C. Login in to Smart Dashboard, access Global Properties, and select Security Management, to verify whether Paul’s IP address is listed.
- D. Access the WEBUI on the Security Gateway, and verify whether Paul’s IP address is listed as a GUI client.
Answer: B
NEW QUESTION 2
CORRECT TEXT
Fill in the blank. What is the correct command and syntax used to view a connection table summary on a Check Point Firewall?
Solution:
fw tab -t connections -s
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
4.8.2
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
In the following cluster configuration; if you reboot sglondon_1 which device will be active when sglondon_1 is back up and running? Why?
- A. sglondon_1 because it the first configured object with the lowest IP.
- B. sglondon_2 because sglondon_1 has highest IP.
- C. sglondon_1, because it is up again, sglondon_2 took over during reboot.
- D. sglondon_2 because it has highest priority.
Answer: D
NEW QUESTION 5
Which of the following is NOT defined by an Access Role object?
- A. Source Network
- B. Source Machine
- C. Source User
- D. Source Server
Answer: D
NEW QUESTION 6
Which of the following are authentication methods that Security Gateway R77 uses to validate connection attempts? Select the response below that includes the MOST complete list of valid authentication methods.
- A. Proxied, User, Dynamic, Session
- B. Connection, User, Client
- C. User, Client, Session
- D. User, Proxied, Session
Answer: C
NEW QUESTION 7
You are troubleshooting a HTTP connection problem. You've started fw monitor -o http.pcap. When you open http.pcap with Wireshark there is only one line. What is the most likely reason?
- A. fw monitor was restricted to the wrong interface.
- B. Like SmartView Tracker only the first packet of a connection will be captured by fw monitor.
- C. By default only SYN pakets are captured.
- D. Acceleration was turned on and therefore fw monitor sees only SYN.
Answer: D
NEW QUESTION 8
CORRECT TEXT
Type the command and syntax that you would use to view the virtual cluster interfaces of a ClusterXL environment.
Solution:
cphaprob -a if
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
Update the topology in the cluster object.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
What command syntax would you use to turn on PDP logging in a distributed environment?
- A. pdp track=1
- B. pdp tracker on
- C. pdp logging on
- D. pdp log=1
Answer: B
NEW QUESTION 11
Your organization’s disaster recovery plan needs an update to the backup and restore section to reap the new distributed R77 installation benefits. Your plan must meet the following required and desired objectives:
Required Objective: The Security Policy repository must be backed up no less frequently than every 24 hours.
Desired Objective: The R77 components that enforce the Security Policies should be backed up at least once a week.
Desired Objective: Back up R77 logs at least once a week.
Your disaster recovery plan is as follows:
- Use the cron utility to run the command upgrade_export each night on the Security Management Servers.
- Configure the organization's routine back up software to back up the files created by the command upgrade_export.
- Configure the GAiA back up utility to back up the Security Gateways every Saturday night.
- Use the cron utility to run the command upgrade_export each Saturday night on the log servers.
- Configure an automatic, nightly logswitch.
- Configure the organization's routine back up software to back up the switched logs every night.
Upon evaluation, your plan:
- A. Meets the required objective and only one desired objective.
- B. Meets the required objective but does not meet either desired objective.
- C. Does not meet the required objective.
- D. Meets the required objective and both desired objectives.
Answer: D
NEW QUESTION 12
Peter is your new Security Administrator. On his first working day, he is very nervous and enters the wrong password three times. His account is locked. What can be done to unlock Peter’s account? Give the BEST answer.
- A. You can unlock Peter’s account by using the command fwm lock_admin -u Peter on the Security Management Server.
- B. You can unlock Peter’s account by using the command fwm unlock_admin -u Peter on the Security Management Server
- C. It is not possible to unlock Peter’s accoun
- D. You have to install the firewall once again or abstain from Peter’s help.
- E. You can unlock Peter’s account by using the command fwm unlock_admin -u Peter on the Security Gateway.
Answer: A
NEW QUESTION 13
Access Role objects define users, machines, and network locations as:
- A. Credentialed objects
- B. Linked objects
- C. One object
- D. Separate objects
Answer: C
NEW QUESTION 14
Your company is running Security Management Server R77 on GAiA, which has been migrated through each version starting from Check Point 4.1. How do you add a new administrator account?
- A. Using SmartDashboard, under Users, select Add New Administrator
- B. Using SmartDashboard or cpconfig
- C. Using the Web console on GAiA under Product configuration, select Administrators
- D. Using cpconfig on the Security Management Server, choose Administrators
Answer: A
NEW QUESTION 15
Re-enable "Cluster membership" on the Gateway.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
CORRECT TEXT
Fill in the blank.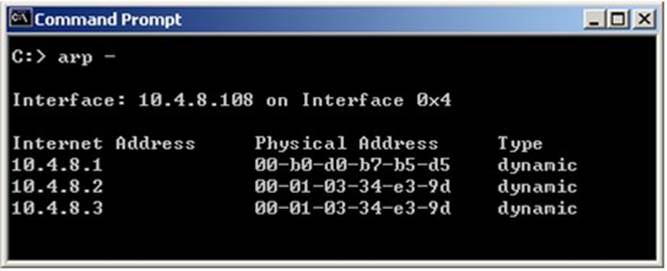
In Load Sharing Unicast mode, the internal cluster IP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2. Internal host 10.4.8.108 Pings 10.4.8.3, and receives replies. The following is the ARP table from the internal Windows host 10.4.8.108. Review the exhibit and type the IP address of the member serving as the pivot machine in the space below.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 17
You enable Hide NAT on the network object, 10.1.1.0 behind the Security Gateway’s external interface. You browse to the Google Website from host, 10.1.1.10 successfully. You enable a log on the rule that allows 10.1.1.0 to exit the network. How many log entries do you see for that connection in SmartView Tracker?
- A. Two, one for outbound, one for inbound
- B. Only one, outbound
- C. Two, both outbound, one for the real IP connection and one for the NAT IP connection
- D. Only one, inbound
Answer: B
NEW QUESTION 18
Users with Identity Awareness Agent installed on their machines login with , so that when the user logs into the domain, that information is also used to meet Identity Awareness credential requests.
- A. Key-logging
- B. ICA Certificates
- C. SecureClient
- D. Single Sign-On
Answer: D
NEW QUESTION 19
How can you check whether IP forwarding is enabled on an IP Security Appliance?
- A. clish -c show routing active enable
- B. cat /proc/sys/net/ipv4/ip_forward
- C. echo 1 > /proc/sys/net/ipv4/ip_forward
- D. ipsofwd list
Answer: D
NEW QUESTION 20
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
- A. John should lock and unlock his computer
- B. Investigate this as a network connectivity issue
- C. The access should be changed to authenticate the user instead of the PC
- D. John should install the Identity Awareness Agent
Answer: C
NEW QUESTION 21
......
100% Valid and Newest Version 156-915.77 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/156-915.77-exam-dumps.html (New 203 Q&As)
