Cause all that matters here is passing the Cisco 200-201 exam. Cause all that you need is a high score of 200-201 Understanding Cisco Cybersecurity Operations Fundamentals exam. The only one thing you need to do is downloading Ucertify 200-201 exam study guides now. We will not let you down with our money-back guarantee.
Free demo questions for Cisco 200-201 Exam Dumps Below:
NEW QUESTION 1
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
- A. known-plaintext
- B. replay
- C. dictionary
- D. man-in-the-middle
Answer: D
NEW QUESTION 2
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
- A. examination
- B. investigation
- C. collection
- D. reporting
Answer: C
NEW QUESTION 3
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
- A. best evidence
- B. corroborative evidence
- C. indirect evidence
- D. forensic evidence
Answer: B
NEW QUESTION 4
What are two social engineering techniques? (Choose two.)
- A. privilege escalation
- B. DDoS attack
- C. phishing
- D. man-in-the-middle
- E. pharming
Answer: CE
NEW QUESTION 5
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
- A. MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
- B. MAC is the strictest of all levels of control and DAC is object-based access
- C. DAC is controlled by the operating system and MAC is controlled by an administrator
- D. DAC is the strictest of all levels of control and MAC is object-based access
Answer: B
NEW QUESTION 6
What is the difference between deep packet inspection and stateful inspection?
- A. Deep packet inspection is more secure than stateful inspection on Layer 4
- B. Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
- C. Stateful inspection is more secure than deep packet inspection on Layer 7
- D. Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Answer: D
NEW QUESTION 7
Refer to the exhibit.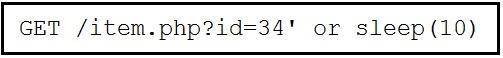
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
- A. parameter manipulation
- B. heap memory corruption
- C. command injection
- D. blind SQL injection
Answer: D
NEW QUESTION 8
Which security principle is violated by running all processes as root or administrator?
- A. principle of least privilege
- B. role-based access control
- C. separation of duties
- D. trusted computing base
Answer: A
NEW QUESTION 9
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
- A. detection and analysis
- B. post-incident activity
- C. vulnerability management
- D. risk assessment
- E. vulnerability scoring
Answer: AB
NEW QUESTION 10
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
- A. reconnaissance
- B. action on objectives
- C. installation
- D. exploitation
Answer: C
NEW QUESTION 11
Refer to the exhibit.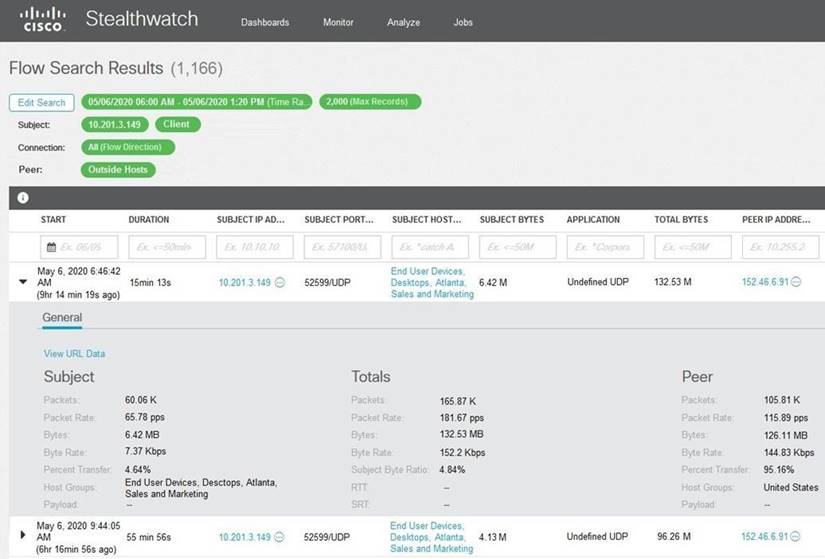
What is the potential threat identified in this Stealthwatch dashboard?
- A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
- B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
- C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
- D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Answer: D
NEW QUESTION 12
Refer to the exhibit.
In which Linux log file is this output found?
- A. /var/log/authorization.log
- B. /var/log/dmesg
- C. var/log/var.log
- D. /var/log/auth.log
Answer: D
NEW QUESTION 13
What is a difference between inline traffic interrogation and traffic mirroring?
- A. Inline inspection acts on the original traffic data flow
- B. Traffic mirroring passes live traffic to a tool for blocking
- C. Traffic mirroring inspects live traffic for analysis and mitigation
- D. Inline traffic copies packets for analysis and security
Answer: B
NEW QUESTION 14
Refer to the exhibit.
Which type of log is displayed?
- A. IDS
- B. proxy
- C. NetFlow
- D. sys
Answer: D
NEW QUESTION 15
What specific type of analysis is assigning values to the scenario to see expected outcomes?
- A. deterministic
- B. exploratory
- C. probabilistic
- D. descriptive
Answer: A
NEW QUESTION 16
Which two components reduce the attack surface on an endpoint? (Choose two.)
- A. secure boot
- B. load balancing
- C. increased audit log levels
- D. restricting USB ports
- E. full packet captures at the endpoint
Answer: AD
NEW QUESTION 17
Which signature impacts network traffic by causing legitimate traffic to be blocked?
- A. false negative
- B. true positive
- C. true negative
- D. false positive
Answer: D
NEW QUESTION 18
Which step in the incident response process researches an attacking host through logs in a SIEM?
- A. detection and analysis
- B. preparation
- C. eradication
- D. containment
Answer: A
NEW QUESTION 19
Refer to the exhibit.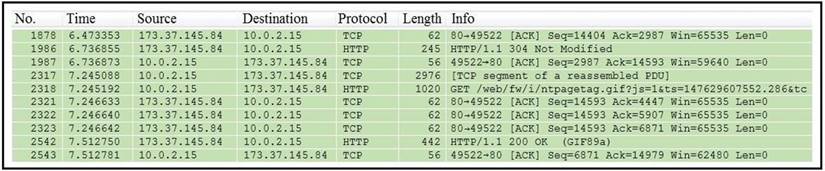
Which packet contains a file that is extractable within Wireshark?
- A. 2317
- B. 1986
- C. 2318
- D. 2542
Answer: D
NEW QUESTION 20
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
- A. least privilege
- B. need to know
- C. integrity validation
- D. due diligence
Answer: A
NEW QUESTION 21
......
100% Valid and Newest Version 200-201 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/200-201-dumps.html (New 98 Q&As)
