Cause all that matters here is passing the Symantec 250-438 exam. Cause all that you need is a high score of 250-438 Administration of Symantec Data Loss Prevention 15 exam. The only one thing you need to do is downloading Passleader 250-438 exam study guides now. We will not let you down with our money-back guarantee.
Check 250-438 free dumps before getting the full version:
NEW QUESTION 1
A DLP administrator has enabled and successfully tested custom attribute lookups for incident data based on the Active Directory LDAP plugin. The Chief Information Security Officer (CISO) has attempted to generate a User Risk Summary report, but the report is empty. The DLP administrator confirms the Cisco’s role has the “User Reporting” privilege enabled, but User Risk reporting is still not working.
What is the probable reason that the User Risk Summary report is blank?
- A. Only DLP administrators are permitted to access and view data for high risk users.
- B. The Enforce server has insufficient permissions for importing user attributes.
- C. User attribute data must be configured separately from incident data attributes.
- D. User attributes have been incorrectly mapped to Active Directory accounts.
Answer: D
NEW QUESTION 2
Which two factors are common sources of data leakage where the main actor is well-meaning insider? (Choose two.)
- A. An absence of a trained incident response team
- B. A disgruntled employee for a job with a competitor
- C. Merger and Acquisition activities
- D. Lack of training and awareness
- E. Broken business processes
Answer: BD
NEW QUESTION 3
A DLP administrator determines that the SymantecDLPProtectIncidents folder on the Enforce server contains. BAD files dated today, while other. IDC files are flowing in and out of the Incidents directory. Only .IDC files larger than 1MB are turning to .BAD files.
What could be causing only incident data smaller than 1MB to persist while incidents larger than 1MB change to .BAD files?
- A. A corrupted policy was deployed.
- B. The Enforce server’s hard drive is out of space.
- C. A detection server has excessive filereader restarts.
- D. Tablespace is almost full.
Answer: D
NEW QUESTION 4
What is the correct order for data in motion when a customer has integrated their CloudSOC and DLP solutions?
- A. User > CloudSOC Gatelet > DLP Cloud Detection Service > Application
- B. User > Enforce > Application
- C. User > Enforce > CloudSOC > Application
- D. User > CloudSOC Gatelet > Enforce > Application
Answer: C
NEW QUESTION 5
A compliance officer needs to understand how the company is complying with its data security policies over time. Which report should be compliance officer generate to obtain the compliance information?
- A. Policy report, filtered on date and summarized by policy
- B. Policy Trend report, summarized by policy, then quarter
- C. Policy report, filtered on quarter and summarized by policy
- D. Policy Trend report, summarized by policy, then severity
Answer: A
NEW QUESTION 6
Which detection method depends on “training sets”?
- A. Form Recognition
- B. Vector Machine Learning (VML)
- C. Index Document Matching (IDM)
- D. Exact Data Matching (EDM)
Answer: B
Explanation:
Reference: http://eval.symantec.com/mktginfo/enterprise/white_papers/b-dlp_machine_learning.WP_en-us.pdf
NEW QUESTION 7
A DLP administrator is testing Network Prevent for Web functionality. When the administrator posts a small test file to a cloud storage website, no new incidents are reported. What should the administrator do to allow incidents to be generated against this file?
- A. Change the “Ignore requests Smaller Than” value to 1
- B. Add the filename to the Inspect Content Type field
- C. Change the “PacketCapture.DISCARD_HTTP_GET” value to “false”
- D. Uncheck trial mode under the ICAP tab
Answer: A
Explanation:
Reference: https://help.symantec.com/cs/dlp15.0/DLP/id-SF0B0161467_v120691346/Configuring-Network-Prevent-for-Web-Server?locale=EN_US
NEW QUESTION 8
Which product is able to replace a confidential document residing on a file share with a marker file explaining why the document was removed?
- A. Network Discover
- B. Cloud Service for Email
- C. Endpoint Prevent
- D. Network Protect
Answer: D
Explanation:
Reference: https://help.symantec.com/cs/dlp15.1/DLP/v15600645_v125428396/Configuring-Network-Protect-for-file-shares?locale=EN_US
NEW QUESTION 9
Which Network Prevent action takes place when the Network Incident list shows the message is “Modified”?
- A. Remove attachments from an email
- B. Obfuscate text in the body of an email
- C. Add one or more SMTP headers to an email
- D. Modify content from the body of an email
Answer: C
NEW QUESTION 10
A customer needs to integrate information from DLP incidents into external Governance, Risk and Compliance dashboards.
Which feature should a third party component integrate with to provide dynamic reporting, create custom incident remediation processes, or support business processes?
- A. Export incidents using the CSV format
- B. Incident Reporting and Update API
- C. Incident Data Views
- D. A Web incident extraction report
Answer: B
NEW QUESTION 11
Refer to the exhibit.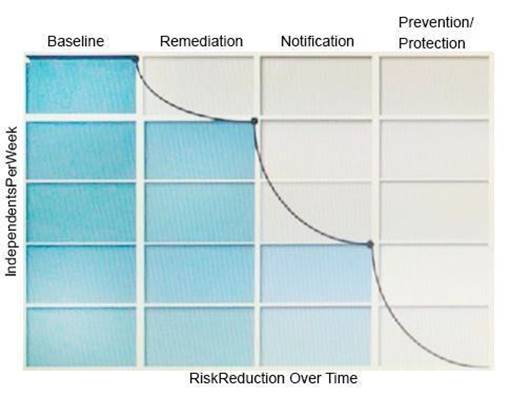
What activity should occur during the baseline phase, according to the risk reduction model?
- A. Define and build the incident response team
- B. Monitor incidents and tune the policy to reduce false positives
- C. Establish business metrics and begin sending reports to business unit stakeholders
- D. Test policies to ensure that blocking actions minimize business process disruptions
Answer: C
NEW QUESTION 12
Why would an administrator set the Similarity Threshold to zero when testing and tuning a Vector Machine Learning (VML) profile?
- A. To capture the matches to the Positive set
- B. To capture the matches to the Negative set
- C. To see the false negatives only
- D. To see the entire range of potential matches
Answer: D
Explanation:
Reference: https://help.symantec.com/cs/dlp15.0/DLP/v45067125_v120691346/Adjusting-the-Similarity-Threshold?locale=EN_US
NEW QUESTION 13
What detection technology supports partial row matching?
- A. Vector Machine Learning (VML)
- B. Indexed Document Matching (IDM)
- C. Described Content Matching (DCM)
- D. Exact Data Matching (EDM)
Answer: D
Explanation:
Reference: https://www.slideshare.net/iftikhariqbal/technology-overview-symantec-data-loss-prevention-dlp
NEW QUESTION 14
An administrator is unable to log in to the Enforce management console as “sysadmin”. Symantec DLP is configured to use Active Directory authentication. The administrator is a member of two roles: “sysadmin” and “remediator.” How should the administrator log in to the Enforce console with the “sysadmin” role?
- A. sysadminusername
- B. sysadminusername@domain
- C. domainusername
- D. usernamesysadmin
Answer: C
NEW QUESTION 15
How do Cloud Detection Service and the Enforce server communicate with each other?
- A. Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 8100.
- B. Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 443.
- C. Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 1443.
- D. Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 443.
Answer: D
NEW QUESTION 16
A DLP administrator needs to remove an agent its associated events from an Endpoint server.
Which Agent Task should the administrator perform to disable the agent’s visibility in the Enforce management console?
- A. Delete action from the Agent Health dashboard
- B. Delete action from the Agent List page
- C. Disable action from Symantec Management Console
- D. Change Endpoint Server action from the Agent Overview page
Answer: C
NEW QUESTION 17
Which action is available for use in both Smart Response and Automated Response rules?
- A. Log to a Syslog Server
- B. Limit incident data retention
- C. Modify SMTP message
- D. Block email message
Answer: D
NEW QUESTION 18
A divisional executive requests a report of all incidents generated by a particular region, summarized by department. What does the DLP administrator need to configure to generate this report?
- A. Custom attributes
- B. Status attributes
- C. Sender attributes
- D. User attributes
Answer: A
NEW QUESTION 19
What should an incident responder select in the Enforce management console to remediate multiple incidents simultaneously?
- A. Smart Response on the Incident page
- B. Automated Response on the Incident Snapshot page
- C. Smart Response on an Incident List report
- D. Automated Response on an Incident List report
Answer: B
NEW QUESTION 20
DRAG DROP
The Symantec Data Loss risk reduction approach has six stages.
Drag and drop the six correct risk reduction stages in the proper order of Occurrence column.
Select and Place: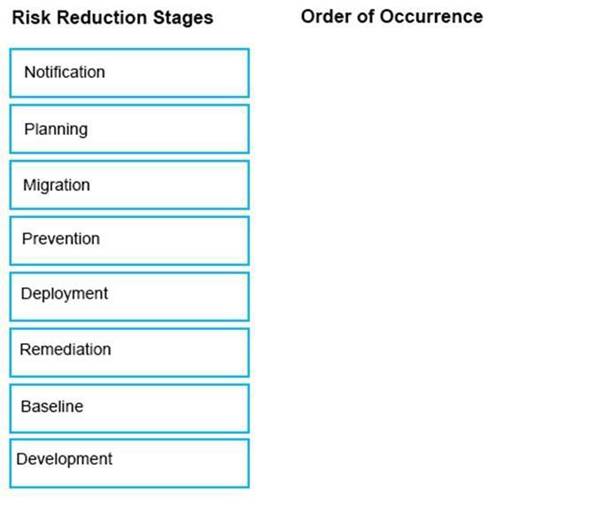
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference: https://www.slideshare.net/iftikhariqbal/symantec-data-loss-prevention-technical-proposal-general
NEW QUESTION 21
Which two detection technology options run on the DLP agent? (Choose two.)
- A. Optical Character Recognition (OCR)
- B. Described Content Matching (DCM)
- C. Directory Group Matching (DGM)
- D. Form Recognition
- E. Indexed Document Matching (IDM)
Answer: BE
NEW QUESTION 22
......
100% Valid and Newest Version 250-438 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/250-438/ (New 70 Q&As)
