Master the 312-50v11 Certified Ethical Hacker Exam (CEH v11) content and be ready for exam day success quickly with this Testking 312-50v11 exam price. We guarantee it!We make it a reality and give you real 312-50v11 questions in our EC-Council 312-50v11 braindumps.Latest 100% VALID EC-Council 312-50v11 Exam Questions Dumps at below page. You can use our EC-Council 312-50v11 braindumps and pass your exam.
Check 312-50v11 free dumps before getting the full version:
NEW QUESTION 1
What is the purpose of DNS AAAA record?
- A. Authorization, Authentication and Auditing record
- B. Address prefix record
- C. Address database record
- D. IPv6 address resolution record
Answer: D
NEW QUESTION 2
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of communication?
- A. 113
- B. 69
- C. 123
- D. 161
Answer: C
NEW QUESTION 3
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network.
Which of these tools would do the SNMP enumeration he is looking for? Select the best answers.
- A. SNMPUtil
- B. SNScan
- C. SNMPScan
- D. Solarwinds IP Network Browser
- E. NMap
Answer: ABD
NEW QUESTION 4
Identify the correct terminology that defines the above statement.
- A. Vulnerability Scanning
- B. Penetration Testing
- C. Security Policy Implementation
- D. Designing Network Security
Answer: B
NEW QUESTION 5
Bob, a network administrator at BigUniversity, realized that some students are connecting their notebooks in the wired network to have Internet access. In the university campus, there are many Ethernet ports available for professors and authorized visitors but not for students.
He identified this when the IDS alerted for malware activities in the network. What should Bob do to avoid this problem?
- A. Disable unused ports in the switches
- B. Separate students in a different VLAN
- C. Use the 802.1x protocol
- D. Ask students to use the wireless network
Answer: C
NEW QUESTION 6
Which DNS resource record can indicate how long any "DNS poisoning" could last?
- A. MX
- B. SOA
- C. NS
- D. TIMEOUT
Answer: B
NEW QUESTION 7
Which command can be used to show the current TCP/IP connections?
- A. Netsh
- B. Netstat
- C. Net use connection
- D. Net use
Answer: A
NEW QUESTION 8
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!” From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page: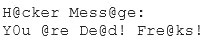
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
- A. ARP spoofing
- B. SQL injection
- C. DNS poisoning
- D. Routing table injection
Answer: C
NEW QUESTION 9
What is GINA?
- A. Gateway Interface Network Application
- B. GUI Installed Network Application CLASS
- C. Global Internet National Authority (G-USA)
- D. Graphical Identification and Authentication DLL
Answer: D
NEW QUESTION 10
What is the minimum number of network connections in a multi homed firewall?
- A. 3
- B. 5
- C. 4
- D. 2
Answer: A
NEW QUESTION 11
What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS?
- A. Supporting both types of algorithms allows less-powerful devices such as mobile phones to use symmetric encryption instead.
- B. Symmetric algorithms such as AES provide a failsafe when asymmetric methods fail.
- C. Symmetric encryption allows the server to security transmit the session keys out-of-band.
- D. Asymmetric cryptography is computationally expensive in compariso
- E. However, it is well-suited to securely negotiate keys for use with symmetric cryptography.
Answer: A
NEW QUESTION 12
Jim’s company regularly performs backups of their critical servers. But the company cannot afford to send backup tapes to an off-site vendor for long-term storage and archiving. Instead, Jim’s company keeps the backup tapes in a safe in the office. Jim’s company is audited each year, and the results from this year’s audit show a risk because backup tapes are not stored off-site. The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
- A. Encrypt the backup tapes and transport them in a lock box.
- B. Degauss the backup tapes and transport them in a lock box.
- C. Hash the backup tapes and transport them in a lock box.
- D. Encrypt the backup tapes and use a courier to transport them.
Answer: A
NEW QUESTION 13
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
- A. He will create a SPAN entry on the spoofed root bridge and redirect traffic to his computer.
- B. He will activate OSPF on the spoofed root bridge.
- C. He will repeat this action so that it escalates to a DoS attack.
- D. He will repeat the same attack against all L2 switches of the network.
Answer: A
NEW QUESTION 14
The establishment of a TCP connection involves a negotiation called three-way handshake. What type of message does the client send to the server in order to begin this negotiation?
- A. ACK
- B. SYN
- C. RST
- D. SYN-ACK
Answer: B
NEW QUESTION 15
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?
- A. The network devices are not all synchronized.
- B. Proper chain of custody was not observed while collecting the logs.
- C. The attacker altered or erased events from the logs.
- D. The security breach was a false positive.
Answer: A
NEW QUESTION 16
To determine if a software program properly handles a wide range of invalid input, a form of automated testing can be used to randomly generate invalid input in an attempt to crash the program.
What term is commonly used when referring to this type of testing?
- A. Randomizing
- B. Bounding
- C. Mutating
- D. Fuzzing
Answer: D
NEW QUESTION 17
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator’s Computer to update the router configuration. What type of an alert is this?
- A. False negative
- B. True negative
- C. True positive
- D. False positive
Answer: D
NEW QUESTION 18
One of your team members has asked you to analyze the following SOA record. What is the version? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.) (Choose four.)
- A. 200303028
- B. 3600
- C. 604800
- D. 2400
- E. 60
- F. 4800
Answer: A
NEW QUESTION 19
Which type of security feature stops vehicles from crashing through the doors of a building?
- A. Bollards
- B. Receptionist
- C. Mantrap
- D. Turnstile
Answer: A
NEW QUESTION 20
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and software as many of the other clients on the network. The client can see the network, but cannot connect. A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to the association requests being sent by the wireless client. What is a possible source of this problem?
- A. The WAP does not recognize the client’s MAC address
- B. The client cannot see the SSID of the wireless network
- C. Client is configured for the wrong channel
- D. The wireless client is not configured to use DHCP
Answer: A
NEW QUESTION 21
Hackers often raise the trust level of a phishing message by modeling the email to look similar to the internal email used by the target company. This includes using logos, formatting, and names of the target company. The phishing message will often use the name of the company CEO, President, or Managers. The time a hacker spends performing research to locate this information about a company is known as?
- A. Exploration
- B. Investigation
- C. Reconnaissance
- D. Enumeration
Answer: C
NEW QUESTION 22
Some clients of TPNQM SA were redirected to a malicious site when they tried to access the TPNQM main site. Bob, a system administrator at TPNQM SA, found that they were victims of DNS Cache Poisoning. What should Bob recommend to deal with such a threat?
- A. The use of security agents in clients’ computers
- B. The use of DNSSEC
- C. The use of double-factor authentication
- D. Client awareness
Answer: B
NEW QUESTION 23
Which of the following is an extremely common IDS evasion technique in the web world?
- A. Spyware
- B. Subnetting
- C. Unicode Characters
- D. Port Knocking
Answer: C
NEW QUESTION 24
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it? Select the best answers.
- A. Use port security on his switches.
- B. Use a tool like ARPwatch to monitor for strange ARP activity.
- C. Use a firewall between all LAN segments.
- D. If you have a small network, use static ARP entries.
- E. Use only static IP addresses on all PC's.
Answer: ABD
NEW QUESTION 25
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, DELETE, PUT, TRACE) using NMAP script engine. What Nmap script will help you with this task?
- A. http-methods
- B. http enum
- C. http-headers
- D. http-git
Answer: A
NEW QUESTION 26
......
P.S. Allfreedumps.com now are offering 100% pass ensure 312-50v11 dumps! All 312-50v11 exam questions have been updated with correct answers: https://www.allfreedumps.com/312-50v11-dumps.html (254 New Questions)
