It is impossible to pass EC-Council 312-50v11 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed EC-Council 312-50v11 practice questions. You will get a surprising result by our Regenerate Certified Ethical Hacker Exam (CEH v11) practice guides.
Check 312-50v11 free dumps before getting the full version:
NEW QUESTION 1
Which Intrusion Detection System is the best applicable for large environments where critical assets on the network need extra scrutiny and is ideal for observing sensitive network segments?
- A. Honeypots
- B. Firewalls
- C. Network-based intrusion detection system (NIDS)
- D. Host-based intrusion detection system (HIDS)
Answer: C
NEW QUESTION 2
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?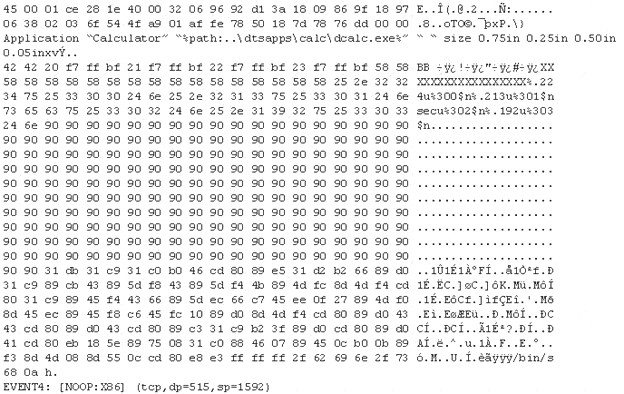
- A. The buffer overflow attack has been neutralized by the IDS
- B. The attacker is creating a directory on the compromised machine
- C. The attacker is attempting a buffer overflow attack and has succeeded
- D. The attacker is attempting an exploit that launches a command-line shell
Answer: D
NEW QUESTION 3
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- A. WHOIS
- B. CAPTCHA
- C. IANA
- D. IETF
Answer: A
NEW QUESTION 4
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He’s determined that the application is vulnerable to SQL injection, and has introduced conditional timing delays into injected queries to determine whether they are successful. What type of SQL injection is Elliot most likely performing?
- A. Error-based SQL injection
- B. Blind SQL injection
- C. Union-based SQL injection
- D. NoSQL injection
Answer: B
NEW QUESTION 5
Which regulation defines security and privacy controls for Federal information systems and organizations?
- A. HIPAA
- B. EU Safe Harbor
- C. PCI-DSS
- D. NIST-800-53
Answer: D
NEW QUESTION 6
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
- A. har.txt
- B. SAM file
- C. wwwroot
- D. Repair file
Answer: B
NEW QUESTION 7
The network team has well-established procedures to follow for creating new rules on the firewall. This includes having approval from a manager prior to implementing any new rules. While reviewing the firewall configuration, you notice a recently implemented rule but cannot locate manager approval for it. What would be a good step to have in the procedures for a situation like this?
- A. Have the network team document the reason why the rule was implemented without prior manager approval.
- B. Monitor all traffic using the firewall rule until a manager can approve it.
- C. Do not roll back the firewall rule as the business may be relying upon it, but try to get manager approval as soon as possible.
- D. Immediately roll back the firewall rule until a manager can approve it
Answer: D
NEW QUESTION 8
Suppose your company has just passed a security risk assessment exercise. The results display that the risk of the breach in the main company application is 50%. Security staff has taken some measures and
implemented the necessary controls. After that, another security risk assessment was performed showing that risk has decreased to 10%. The risk threshold for the application is 20%. Which of the following risk decisions will be the best for the project in terms of its successful continuation with the most business profit?
- A. Accept the risk
- B. Introduce more controls to bring risk to 0%
- C. Mitigate the risk
- D. Avoid the risk
Answer: A
NEW QUESTION 9
Which of the following tools can be used for passive OS fingerprinting?
- A. nmap
- B. tcpdump
- C. tracert
- D. ping
Answer: B
NEW QUESTION 10
Study the following log extract and identify the attack.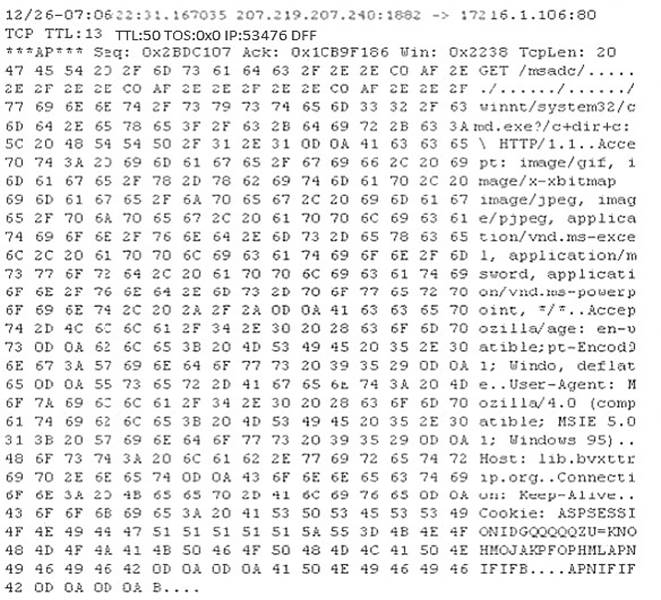
- A. Hexcode Attack
- B. Cross Site Scripting
- C. Multiple Domain Traversal Attack
- D. Unicode Directory Traversal Attack
Answer: D
NEW QUESTION 11
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
- A. Use the Cisco's TFTP default password to connect and download the configuration file
- B. Run a network sniffer and capture the returned traffic with the configuration file from the router
- C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
- D. Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
Answer: BD
NEW QUESTION 12
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.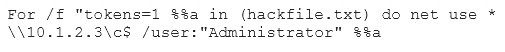
What is Eve trying to do?
- A. Eve is trying to connect as a user with Administrator privileges
- B. Eve is trying to enumerate all users with Administrative privileges
- C. Eve is trying to carry out a password crack for user Administrator
- D. Eve is trying to escalate privilege of the null user to that of Administrator
Answer: C
NEW QUESTION 13
If you want to only scan fewer ports than the default scan using Nmap tool, which option would you use?
- A. –r
- B. –F
- C. –P
- D. –sP
Answer: B
NEW QUESTION 14
While using your bank’s online servicing you notice the following string in the URL bar:
“http: // www. MyPersonalBank. com/ account?id=368940911028389&Damount=10980&Camount=21”
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
- A. Cookie Tampering
- B. SQL Injection
- C. Web Parameter Tampering
- D. XSS Reflection
Answer: C
NEW QUESTION 15
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters. With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
- A. Online Attack
- B. Dictionary Attack
- C. Brute Force Attack
- D. Hybrid Attack
Answer: D
NEW QUESTION 16
What is the algorithm used by LM for Windows2000 SAM?
- A. MD4
- B. DES
- C. SHA
- D. SSL
Answer: B
NEW QUESTION 17
Bob is acknowledged as a hacker of repute and is popular among visitors of "underground" sites.
Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well.
In this context, what would be the most effective method to bridge the knowledge gap between the "black" hats or crackers and the "white" hats or computer security professionals? (Choose the test answer.)
- A. Educate everyone with books, articles and training on risk analysis, vulnerabilities and safeguards.
- B. Hire more computer security monitoring personnel to monitor computer systems and networks.
- C. Make obtaining either a computer security certification or accreditation easier to achieve so more individuals feel that they are a part of something larger than life.
- D. Train more National Guard and reservist in the art of computer security to help out in times of emergency or crises.
Answer: A
NEW QUESTION 18
Todd has been asked by the security officer to purchase a counter-based authentication system. Which of the following best describes this type of system?
- A. A biometric system that bases authentication decisions on behavioral attributes.
- B. A biometric system that bases authentication decisions on physical attributes.
- C. An authentication system that creates one-time passwords that are encrypted with secret keys.
- D. An authentication system that uses passphrases that are converted into virtual passwords.
Answer: C
NEW QUESTION 19
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c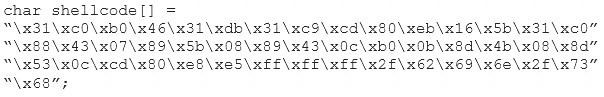
What is the hexadecimal value of NOP instruction?
- A. 0x60
- B. 0x80
- C. 0x70
- D. 0x90
Answer: D
NEW QUESTION 20
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs: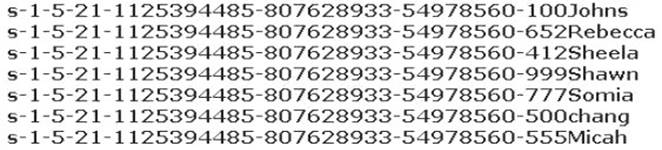
From the above list identify the user account with System Administrator privileges.
- A. John
- B. Rebecca
- C. Sheela
- D. Shawn
- E. Somia
- F. Chang
- G. Micah
Answer: F
NEW QUESTION 21
A technician is resolving an issue where a computer is unable to connect to the Internet using a wireless access point. The computer is able to transfer files locally to other machines, but cannot successfully reach the Internet. When the technician examines the IP address and default gateway they are both on the 192.168.1.0/24. Which of the following has occurred?
- A. The computer is not using a private IP address.
- B. The gateway is not routing to a public IP address.
- C. The gateway and the computer are not on the same network.
- D. The computer is using an invalid IP address.
Answer: B
NEW QUESTION 22
Which results will be returned with the following Google search query? site:target.com – site:Marketing.target.com accounting
- A. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting.
- B. Results matching all words in the query.
- C. Results for matches on target.com and Marketing.target.com that include the word “accounting”
- D. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
Answer: D
NEW QUESTION 23
Study the snort rule given below: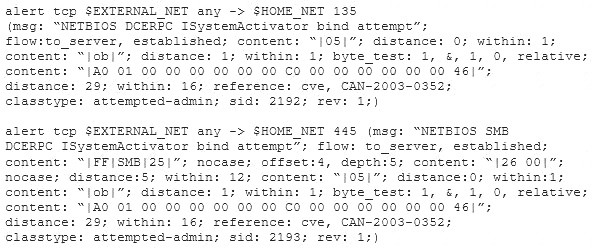
From the options below, choose the exploit against which this rule applies.
- A. WebDav
- B. SQL Slammer
- C. MS Blaster
- D. MyDoom
Answer: C
NEW QUESTION 24
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, small sized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
- A. tcpsplice
- B. Burp
- C. Hydra
- D. Whisker
Answer: D
NEW QUESTION 25
Which of the following are well known password-cracking programs?
- A. L0phtcrack
- B. NetCat
- C. Jack the Ripper
- D. Netbus
- E. John the Ripper
Answer: AE
NEW QUESTION 26
......
Recommend!! Get the Full 312-50v11 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/312-50v11-pdf-download.html (New 254 Q&As Version)
