It is more faster and easier to pass the Cisco 350-701 exam by using Verified Cisco Implementing and Operating Cisco Security Core Technologies questuins and answers. Immediate access to the Latest 350-701 Exam and find the same core area 350-701 questions with professionally verified answers, then PASS your exam with a high score now.
Also have 350-701 free dumps questions for you:
NEW QUESTION 1
Which information is required when adding a device to Firepower Management Center?
- A. username and password
- B. encryption method
- C. device serial number
- D. registration key
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Device_Management_Basics.html#ID-2242-0000069d
NEW QUESTION 2
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
- A. Certificate Trust List
- B. Endpoint Trust List
- C. Enterprise Proxy Service
- D. Secured Collaboration Proxy
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/special/unified-communications/guide/unified-comm/unified-comm-tlsproxy.html
NEW QUESTION 3
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer: B
NEW QUESTION 4
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
- A. Check integer, float, or Boolean string parameters to ensure accurate values.
- B. Use prepared statements and parameterized queries.
- C. Secure the connection between the web and the app tier.
- D. Write SQL code instead of using object-relational mapping libraries.
- E. Block SQL code execution in the web application database login.
Answer: AB
Explanation:
Reference: https://en.wikipedia.org/wiki/SQL_injection
NEW QUESTION 5
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
- A. DDoS
- B. antispam
- C. antivirus
- D. encryption
- E. DLP
Answer: DE
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
NEW QUESTION 6
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
- A. Enable IP Layer enforcement.
- B. Activate the Advanced Malware Protection license
- C. Activate SSL decryption.
- D. Enable Intelligent Proxy.
Answer: D
NEW QUESTION 7
Which two mechanisms are used to control phishing attacks? (Choose two.)
- A. Enable browser alerts for fraudulent websites.
- B. Define security group memberships.
- C. Revoke expired CRL of the websites.
- D. Use antispyware software.
- E. Implement email filtering techniques.
Answer: AE
NEW QUESTION 8
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
- A. user input validation in a web page or web application
- B. Linux and Windows operating systems
- C. database
- D. web page images
Answer: C
Explanation:
Reference: https://tools.cisco.com/security/center/resources/sql_injection
NEW QUESTION 9
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
- A. smurf
- B. distributed denial of service
- C. cross-site scripting
- D. rootkit exploit
Answer: C
NEW QUESTION 10
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
- A. AMP
- B. AnyConnect
- C. DynDNS
- D. Talos
Answer: D
NEW QUESTION 11
Where are individual sites specified to be blacklisted in Cisco Umbrella?
- A. application settings
- B. content categories
- C. security settings
- D. destination lists
Answer: D
NEW QUESTION 12
Which attack is commonly associated with C and C++ programming languages?
- A. cross-site scripting
- B. water holing
- C. DDoS
- D. buffer overflow
Answer: D
Explanation:
Reference: https://en.wikipedia.org/wiki/Buffer_overflow
NEW QUESTION 13
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
- A. Patch for cross-site scripting.
- B. Perform backups to the private cloud.
- C. Protect against input validation and character escapes in the endpoint.
- D. Install a spam and virus email filter.
- E. Protect systems with an up-to-date antimalware program.
Answer: DE
NEW QUESTION 14
Which SNMPv3 configuration must be used to support the strongest security possible?
- A. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- B. asa-host(config)#snmp-server group myv3 v3 noauth asa- host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa- host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- C. asa-host(config)#snmp- server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv 3des ciscXXXXXXXXasa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- D. asa- host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
Answer: D
NEW QUESTION 15
What are two list types within AMP for Endpoints Outbreak Control? (Choose two.)
- A. blocked ports
- B. simple custom detections
- C. command and control
- D. allowed applications
- E. URL
Answer: BD
Explanation:
Reference: https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf chapter 2
NEW QUESTION 16
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
- A. authentication server: Cisco Identity Service Engine
- B. supplicant: Cisco AnyConnect ISE Posture module
- C. authenticator: Cisco Catalyst switch
- D. authenticator: Cisco Identity Services Engine
- E. authentication server: Cisco Prime Infrastructure
Answer: AC
Explanation:
Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
NEW QUESTION 17
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two.)
- A. Sophos engine
- B. white list
- C. RAT
- D. outbreak filters
- E. DLP
Answer: AD
NEW QUESTION 18
Refer to the exhibit.
What does the number 15 represent in this configuration?
- A. privilege level for an authorized user to this router
- B. access list that identifies the SNMP devices that can access the router
- C. interval in seconds between SNMPv3 authentication attempts
- D. number of possible failed attempts until the SNMPv3 user is locked out
Answer: B
NEW QUESTION 19
Refer to the exhibit.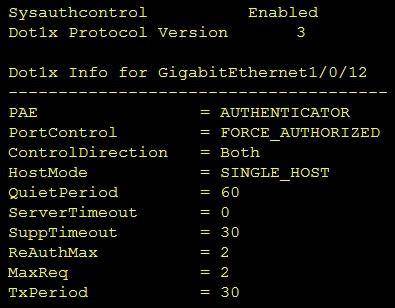
Which command was used to display this output?
- A. show dot1x all
- B. show dot1x
- C. show dot1x all summary
- D. show dot1x interface gi1/0/12
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x-pba.html
NEW QUESTION 20
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
- A. hypervisor
- B. virtual machine
- C. network
- D. application
Answer: D
Explanation:
Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
NEW QUESTION 21
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
- A. Application Control
- B. Security Category Blocking
- C. Content Category Blocking
- D. File Analysis
Answer: B
Explanation:
Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories
NEW QUESTION 22
......
P.S. Easily pass 350-701 Exam with 102 Q&As Dumpscollection Dumps & pdf Version, Welcome to Download the Newest Dumpscollection 350-701 Dumps: http://www.dumpscollection.net/dumps/350-701/ (102 New Questions)
