we provide Simulation Cisco 350-701 exam engine which are the best for clearing 350-701 test, and to get certified by Cisco Implementing and Operating Cisco Security Core Technologies. The 350-701 Questions & Answers covers all the knowledge points of the real 350-701 exam. Crack your Cisco 350-701 Exam with latest dumps, guaranteed!
Online 350-701 free questions and answers of New Version:
NEW QUESTION 1
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
- A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
- B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
- C. The IPsec configuration that is set up on the active device must be duplicated on the standby device.
- D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
- E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
Answer: BC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
NEW QUESTION 2
For which two conditions can an endpoint be checked using ISE posture assessment? (Choose two.)
- A. computer identity
- B. Windows service
- C. user identity
- D. Windows firewall
- E. default browser
Answer: BC
NEW QUESTION 3
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
- A. RSA SecureID
- B. Internal Database
- C. Active Directory
- D. LDAP
Answer: C
NEW QUESTION 4
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
- A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
- B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
- C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
- D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-cr-c4.html#wp6039879000
NEW QUESTION 5
In which cloud services model is the tenant responsible for virtual machine OS patching?
- A. IaaS
- B. UCaaS
- C. PaaS
- D. SaaS
Answer: A
Explanation:
Reference: https://www.cmswire.com/cms/information-management/cloud-service-models-iaas-saas-paas-how-microsoft-office-365-azure-fit-in-021672.php
NEW QUESTION 6
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
- A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
- B. Cisco FTDv with one management interface and two traffic interfaces configured
- C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
- D. Cisco FTDv with two management interfaces and one traffic interface configured
- E. Cisco FTDv configured in routed mode and IPv6 configured
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/white-paper-c11-740505.html
NEW QUESTION 7
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
- A. Certificate Trust List
- B. Endpoint Trust List
- C. Enterprise Proxy Service
- D. Secured Collaboration Proxy
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/special/unified-communications/guide/unified-comm/unified-comm-tlsproxy.html
NEW QUESTION 8
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
- A. DMVPN
- B. FlexVPN
- C. IPsec DVTI
- D. GET VPN
Answer: D
NEW QUESTION 9
DRAG DROP
Drag and drop the capabilities from the left onto the correct technologies on the right.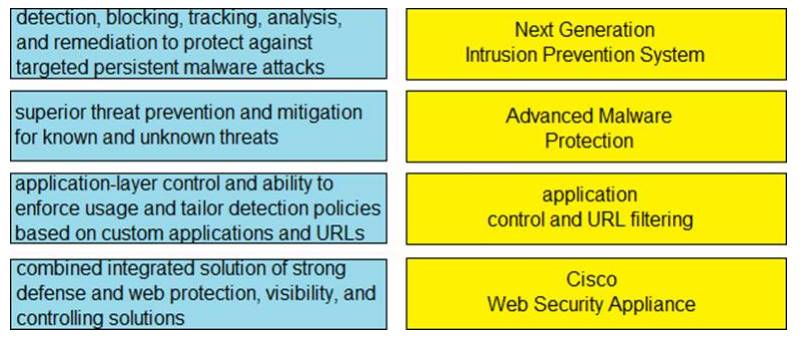
Solution:
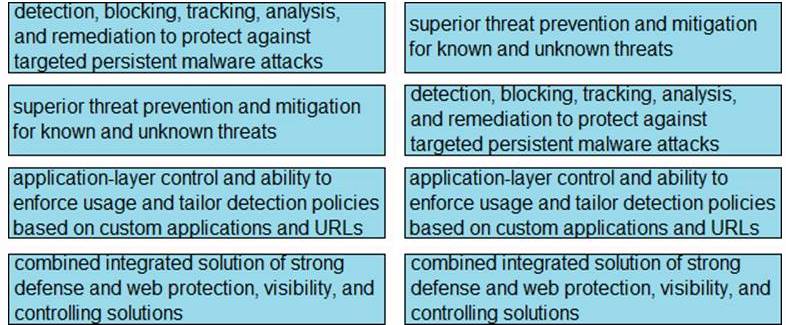
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
- A. transparent
- B. redirection
- C. forward
- D. proxy gateway
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
NEW QUESTION 11
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
- A. Enable IP Layer enforcement.
- B. Activate the Advanced Malware Protection license
- C. Activate SSL decryption.
- D. Enable Intelligent Proxy.
Answer: D
NEW QUESTION 12
DRAG DROP
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.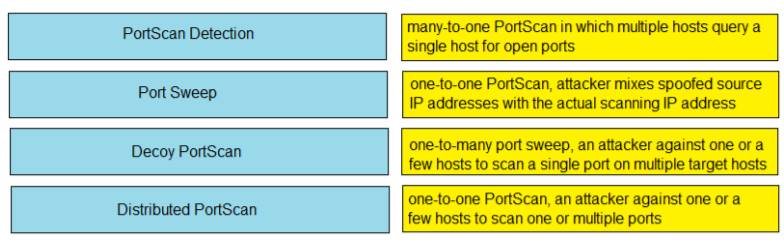
Solution:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)
- A. biometric factor
- B. time factor
- C. confidentiality factor
- D. knowledge factor
- E. encryption factor
Answer: AD
NEW QUESTION 14
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
- A. Check integer, float, or Boolean string parameters to ensure accurate values.
- B. Use prepared statements and parameterized queries.
- C. Secure the connection between the web and the app tier.
- D. Write SQL code instead of using object-relational mapping libraries.
- E. Block SQL code execution in the web application database login.
Answer: AB
Explanation:
Reference: https://en.wikipedia.org/wiki/SQL_injection
NEW QUESTION 15
Which VPN technology can support a multivendor environment and secure traffic between sites?
- A. SSL VPN
- B. GET VPN
- C. FlexVPN
- D. DMVPN
Answer: C
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/data_sheet_c78-704277.html
NEW QUESTION 16
Which two descriptions of AES encryption are true? (Choose two.)
- A. AES is less secure than 3DES.
- B. AES is more secure than 3DES.
- C. AES can use a 168-bit key for encryption.
- D. AES can use a 256-bit key for encryption.
- E. AES encrypts and decrypts a key three times in sequence.
Answer: BD
Explanation:
Reference: https://gpdb.docs.pivotal.io/43190/admin_guide/topics/ipsec.html
NEW QUESTION 17
......
P.S. Easily pass 350-701 Exam with 337 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared 350-701 Dumps: https://www.certshared.com/exam/350-701/ (337 New Questions)
