Cause all that matters here is passing the EC-Council 412-79v10 exam. Cause all that you need is a high score of 412-79v10 EC-Council Certified Security Analyst (ECSA) V10 exam. The only one thing you need to do is downloading Pass4sure 412-79v10 exam study guides now. We will not let you down with our money-back guarantee.
NEW QUESTION 1
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
- A. SSI injection attack
- B. Insecure cryptographic storage attack
- C. Hidden field manipulation attack
- D. Man-in-the-Middle attack
Answer: B
NEW QUESTION 2
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 3
A chipset is a group of integrated circuits that are designed to work together and are usually marketed as a single product.” It is generally the motherboard chips or the chips used on the expansion card.
Which one of the following is well supported in most wireless applications?
- A. Orinoco chipsets
- B. Prism II chipsets
- C. Atheros Chipset
- D. Cisco chipset
Answer: B
NEW QUESTION 4
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
- A. SMTP Queue Bouncing
- B. SMTP Message Bouncing
- C. SMTP Server Bouncing
- D. SMTP Mail Bouncing
Answer: D
NEW QUESTION 5
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florida. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa.
She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, requested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for.
What principal of social engineering did Julia use?
- A. Reciprocation
- B. Friendship/Liking
- C. Social Validation
- D. Scarcity
Answer: A
NEW QUESTION 6
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
- A. TCP port 152
- B. UDP port 177
- C. UDP port 123
- D. TCP port 113
Answer: C
NEW QUESTION 7
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer: B
NEW QUESTION 8
Frank is working on a vulnerability assessment for a company on the West coast. The company hired Frank to assess its network security through scanning, pen tests, and vulnerability assessments. After discovering numerous known vulnerabilities detected by a temporary IDS he set up, he notices a number of items that show up as unknown but questionable in the logs.
He looks up the behavior on the Internet, but cannot find anything related. What organization should Frank submit the log to find out if it is a new vulnerability or not?
- A. CVE
- B. IANA
- C. RIPE
- D. APIPA
Answer: A
NEW QUESTION 9
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client’s operating environment, threat perception, security and compliance requirements, ROE, and budget.
Various components need to be considered for testing while developing the scope of the project.
Which of the following is NOT a pen testing component to be tested?
- A. System Software Security
- B. Intrusion Detection
- C. Outside Accomplices
- D. Inside Accomplices
Answer: C
NEW QUESTION 10
Jim performed a vulnerability analysis on his network and found no potential problems. He runs another utility that executes exploits against his system to verify the results of the vulnerability test. The second utility executes five known exploits against his network in which the vulnerability analysis said were not exploitable.
What kind of results did Jim receive from his vulnerability analysis?
- A. True negatives
- B. False negatives
- C. False positives
- D. True positives
Answer: B
NEW QUESTION 11
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 12
Identify the type of firewall represented in the diagram below: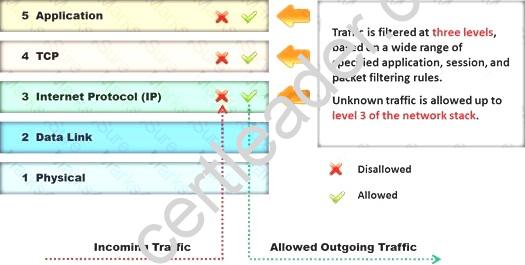
- A. Stateful multilayer inspection firewall
- B. Application level gateway
- C. Packet filter
- D. Circuit level gateway
Answer: A
NEW QUESTION 13
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 14
Which one of the following log analysis tools is a Cisco Router Log Format log analyzer and it parses logs, imports them into a SQL database (or its own built-in database), aggregates them, and generates the dynamically filtered reports, all through a web interface?
- A. Event Log Tracker
- B. Sawmill
- C. Syslog Manager
- D. Event Log Explorer
Answer: B
NEW QUESTION 15
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment. The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: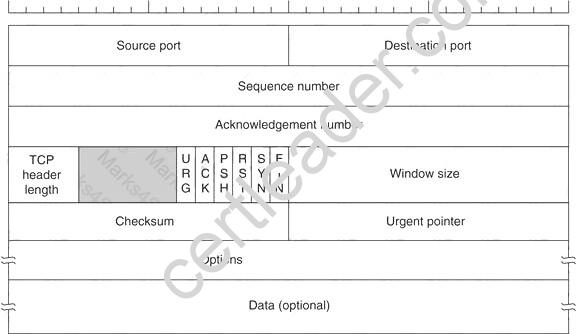
- A. 16 bits
- B. 32 bits
- C. 8 bits
- D. 24 bits
Answer: B
NEW QUESTION 16
Which of the following statement holds true for TCP Operation?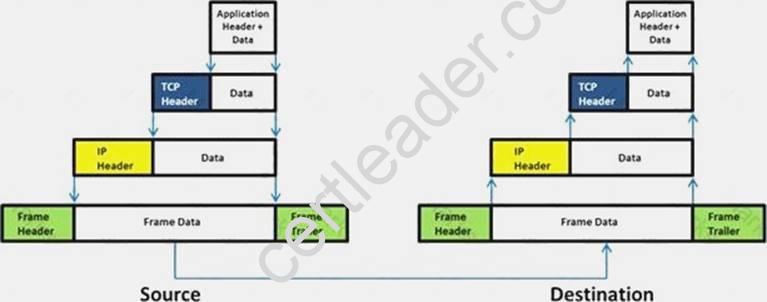
- A. Port numbers are used to know which application the receiving host should pass the data to
- B. Sequence numbers are used to track the number of packets lost in transmission
- C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
- D. Data transfer begins even before the connection is established
Answer: D
NEW QUESTION 17
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers.
Which one of the following cannot handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall/router(edge device)-net architecture”
- D. “Internet-firewall -net architecture”
Answer: B
NEW QUESTION 18
What is the target host IP in the following command?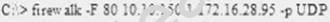
- A. Firewalk does not scan target hosts
- B. 172.16.28.95
- C. This command is using FIN packets, which cannot scan target hosts
- D. 10.10.150.1
Answer: A
NEW QUESTION 19
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.
What are the two types of ‘white-box’ penetration testing?
- A. Announced testing and blind testing
- B. Blind testing and double blind testing
- C. Blind testing and unannounced testing
- D. Announced testing and unannounced testing
Answer: D
NEW QUESTION 20
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 21
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
- A. Hash Key Length
- B. C/R Value Length
- C. C/R Key Length
- D. Hash Value Length
Answer: B
NEW QUESTION 22
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
- A. ROCHESTON fileformat:+ppt
- B. ROCHESTON ppt:filestring
- C. ROCHESTON filetype:ppt
- D. ROCHESTON +ppt:filesearch
Answer: C
NEW QUESTION 23
What are the security risks of running a "repair" installation for Windows XP?
- A. There are no security risks when running the "repair" installation for Windows XP
- B. Pressing Shift+F1 gives the user administrative rights
- C. Pressing Ctrl+F10 gives the user administrative rights
- D. Pressing Shift+F10 gives the user administrative rights
Answer: D
NEW QUESTION 24
Which of the following policy forbids everything with strict restrictions on all usage of the company systems and network?
- A. Information-Protection Po
- B. Paranoid Policy
- C. Promiscuous Policy
- D. Prudent Policy
Answer: B
NEW QUESTION 25
What is the maximum value of a “tinyint” field in most database systems?
- A. 222
- B. 224 or more
- C. 240 or less
- D. 225 or more
Answer: D
NEW QUESTION 26
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
NEW QUESTION 27
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.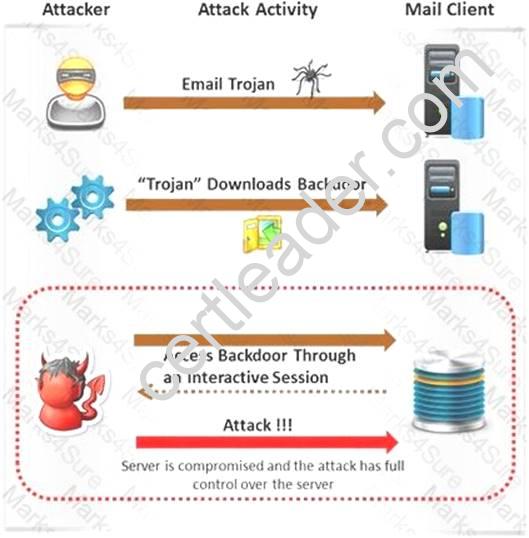
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
- A. Internal network mapping to map the internal network of the target machine
- B. Port scanning to determine what ports are open or in use on the target machine
- C. Sniffing to monitor all the incoming and outgoing network traffic
- D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Answer: D
NEW QUESTION 28
An "idle" system is also referred to as what?
- A. Zombie
- B. PC not being used
- C. Bot
- D. PC not connected to the Internet
Answer: A
NEW QUESTION 29
As a security analyst you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
- A. The employees network usernames and passwords
- B. The MAC address of the employees' computers
- C. The IP address of the employees computers
- D. Bank account numbers and the corresponding routing numbers
Answer: C
NEW QUESTION 30
Identify the type of authentication mechanism represented below: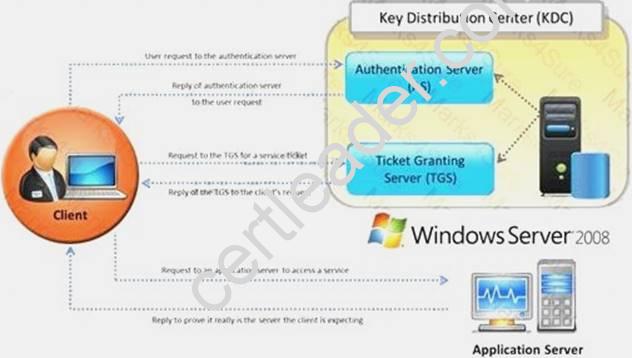
- A. NTLMv1
- B. NTLMv2
- C. LAN Manager Hash
- D. Kerberos
Answer: D
NEW QUESTION 31
......
Recommend!! Get the Full 412-79v10 dumps in VCE and PDF From Dumpscollection, Welcome to Download: http://www.dumpscollection.net/dumps/412-79v10/ (New 201 Q&As Version)
