Master the 412-79v9 EC-Council Certified Security Analyst (ECSA) v9 content and be ready for exam day success quickly with this Testking 412-79v9 testing engine. We guarantee it!We make it a reality and give you real 412-79v9 questions in our EC-Council 412-79v9 braindumps.Latest 100% VALID EC-Council 412-79v9 Exam Questions Dumps at below page. You can use our EC-Council 412-79v9 braindumps and pass your exam.
Also have 412-79v9 free dumps questions for you:
NEW QUESTION 1
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
- A. 802.11b
- B. 802.11a
- C. 802.11n
- D. 802.11-Legacy
Answer: D
NEW QUESTION 2
Which of the following protocol’s traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
- A. Reverse Gossip Transport Protocol (RGTP)
- B. Real-time Transport Protocol (RTP)
- C. Remote Desktop Protocol (RDP)
- D. Session Initiation Protocol (SIP)
Answer: C
Explanation:
Reference: http://wiki.wireshark.org/RDP
NEW QUESTION 3
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.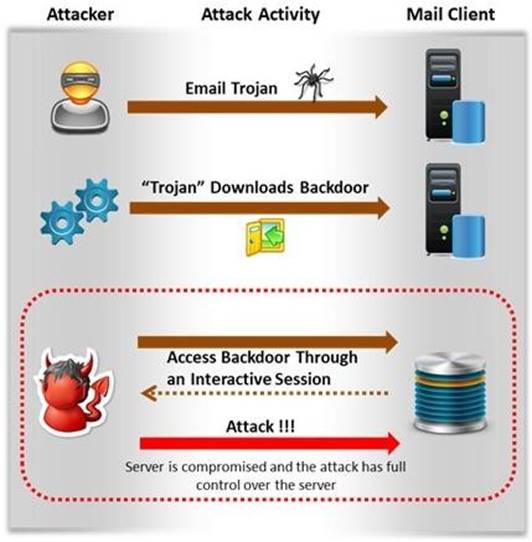
Which of the following techniques do attackers use to create backdoors to covertly gather
critical information about a target machine?
- A. Internal network mapping to map the internal network of the target machine
- B. Port scanning to determine what ports are open or in use on the target machine
- C. Sniffing to monitor all the incoming and outgoing network traffic
- D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Answer: D
NEW QUESTION 4
Which of the following is an application alert returned by a web application that helps an attacker guess a valid username?
- A. Invalid username or password
- B. Account username was not found
- C. Incorrect password
- D. Username or password incorrect
Answer: C
NEW QUESTION 5
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
- A. ROCHESTON fileformat:+ppt
- B. ROCHESTON ppt:filestring
- C. ROCHESTON filetype:ppt
- D. ROCHESTON +ppt:filesearch
Answer: C
Explanation:
Reference: http://blog.hubspot.com/blog/tabid/6307/bid/1264/12-Quick-Tips-To-Search-Google-Like-An-Expert.aspx (specific document types)
NEW QUESTION 6
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer: C
NEW QUESTION 7
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
- A. 3001-3100
- B. 5000-5099
- C. 6666-6674
- D. 0 – 1023
Answer: D
Explanation:
Reference: https://www.ietf.org/rfc/rfc1700.txt (well known port numbers, 4th para)
NEW QUESTION 8
John, a penetration tester, was asked for a document that defines the project, specifies goals, objectives, deadlines, the resources required, and the approach of the project. Which of the following includes all of these requirements?
- A. Penetration testing project plan
- B. Penetration testing software project management plan
- C. Penetration testing project scope report
- D. Penetration testing schedule plan
Answer: A
Explanation:
Rfere http://books.google.com.pk/books?id=7dwEAAAAQBAJ&pg=SA4-PA14&lpg=SA4-
PA14&dq=penetration+testing+document+that+defines+the+project,+specifies+goals,+obje ctives,+deadlines,+the+resources+required,+and+the+approach+of+the+project&source=b l&ots=SQCLHNtthN&sig=kRcccmtDtCdZgB7hASShxSRbfOM&hl=en&sa=X&ei=hyMfVOKz GYvmarvFgaAL&ved=0CB0Q6AEwAA#v=onepage&q=penetration%20testing%20docume nt%20that%20defines%20the%20project%2C%20specifies%20goals%2C%20objectives% 2C%20deadlines%2C%20the%20resources%20required%2C%20and%20the%20approac h%20of%20the%20project&f=false
NEW QUESTION 9
Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
- A. PIPEDA
- B. PCI DSS
- C. Human Rights Act 1998
- D. Data Protection Act 1998
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
NEW QUESTION 10
Which of the following external pen testing tests reveals information on price, usernames and passwords, sessions, URL characters, special instructors, encryption used, and web page behaviors?
- A. Check for Directory Consistency and Page Naming Syntax of the Web Pages
- B. Examine Server Side Includes (SSI)
- C. Examine Hidden Fields
- D. Examine E-commerce and Payment Gateways Handled by the Web Server
Answer: C
Explanation:
Reference: http://www.scribd.com/doc/133636402/LPTv4-Module-18-External-Penetration-Testing-NoRestriction (page 71)
NEW QUESTION 11
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools. The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected.
Conventionally it is achieved by comparing the MAC address of the participating wireless devices.
Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?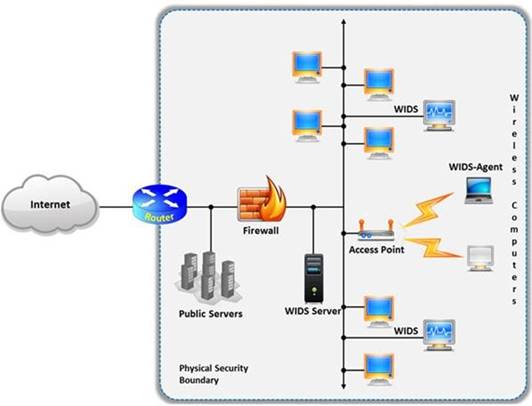
- A. Social engineering
- B. SQL injection
- C. Parameter tampering
- D. Man-in-the-middle attack
Answer: D
Explanation:
Reference: http://www.infosecwriters.com/text_resources/pdf/Wireless_IDS_JDixon.pdf (page 5)
NEW QUESTION 12
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 13
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework (ISSAF)
- C. Bell Labs Network Security Framework
- D. The IBM Security Framework
Answer: A
NEW QUESTION 14
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
- A. Penetration Testing Agreement
- B. Rules of Behavior Agreement
- C. Liability Insurance
- D. Non-Disclosure Agreement
Answer: D
NEW QUESTION 15
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.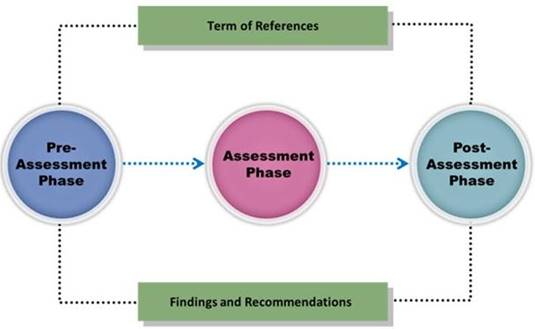
What does a vulnerability assessment identify?
- A. Disgruntled employees
- B. Weaknesses that could be exploited
- C. Physical security breaches
- D. Organizational structure
Answer: B
NEW QUESTION 16
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.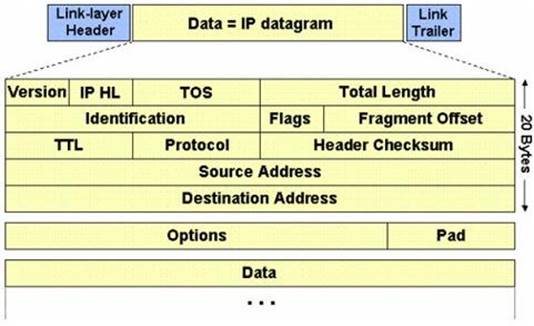
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer: C
Explanation:
Reference: http://www.freesoft.org/CIE/Course/Section3/7.htm (fragment offset: 13 bits)
NEW QUESTION 17
A directory traversal (or path traversal) consists in exploiting insufficient security validation/sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" are passed through to the file APIs.
The goal of this attack is to order an application to access a computer file that is not intended to be accessible. This attack exploits a lack of security (the software is acting exactly as it is supposed to) as opposed to exploiting a bug in the code.
To perform a directory traversal attack, which sequence does a pen tester need to follow to manipulate variables of reference files?
- A. dot-dot-slash (../) sequence
- B. Denial-of-Service sequence
- C. Brute force sequence
- D. SQL Injection sequence
Answer: A
Explanation:
Reference: https://www.cs.ucsb.edu/~vigna/publications/2010_doupe_cova_vigna_dimva10.pdf (pae 7, directory traversal)
NEW QUESTION 18
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
- A. Passive Assessment
- B. Host-based Assessment
- C. External Assessment
- D. Application Assessment
Answer: D
NEW QUESTION 19
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.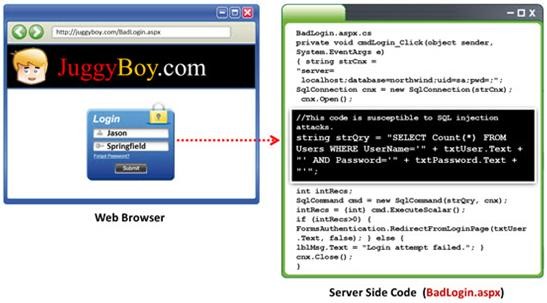
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
- A. Send single quotes as the input data to catch instances where the user input is not sanitized
- B. Send double quotes as the input data to catch instances where the user input is not sanitized
- C. Send long strings of junk data, just as you would send strings to detect buffer overruns
- D. Use a right square bracket (the “]” character) as the input data to catch instances wherethe user input is used as part of a SQL identifier without any input sanitization
Answer: D
NEW QUESTION 20
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company’s private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based on the specific needs of an organization. Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic weakness of which one of the following Protocol?
- A. Lightweight Directory Access Protocol (LDAP)
- B. Simple Network Management Protocol (SNMP)
- C. Telnet
- D. Secure Shell (SSH)
Answer: D
NEW QUESTION 21
Output modules allow Snort to be much more flexible in the formatting and presentation of output to its users. Snort has 9 output plug-ins that push out data in different formats. Which one of the following output plug-ins allows alert data to be written in a format easily importable to a database?
- A. unified
- B. csv
- C. alert_unixsock
- D. alert_fast
Answer: B
NEW QUESTION 22
Which of the following protocols cannot be used to filter VoIP traffic?
- A. Media Gateway Control Protocol (MGCP)
- B. Real-time Transport Control Protocol (RTCP)
- C. Session Description Protocol (SDP)
- D. Real-Time Publish Subscribe (RTPS)
Answer: D
NEW QUESTION 23
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 24
Which one of the following 802.11 types has WLAN as a network support?
- A. 802.11b
- B. 802.11-Legacy
- C. 802.11n
- D. 802.11g
Answer: C
NEW QUESTION 25
Nessus can test a server or a network for DoS vulnerabilities. Which one of the following script tries to kill a service?
- A. ACT_DENIAL
- B. ACT_FLOOD
- C. ACT_KILL_HOST
- D. ACT_ATTACK
Answer: A
NEW QUESTION 26
......
100% Valid and Newest Version 412-79v9 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/412-79v9/ (New 203 Q&As)
