Master the CEH-001 Certified Ethical Hacker (CEH) content and be ready for exam day success quickly with this Certleader CEH-001 sample question. We guarantee it!We make it a reality and give you real CEH-001 questions in our GAQM CEH-001 braindumps.Latest 100% VALID GAQM CEH-001 Exam Questions Dumps at below page. You can use our GAQM CEH-001 braindumps and pass your exam.
GAQM CEH-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Low humidity in a data center can cause which of the following problems?
- A. Heat
- B. Corrosion
- C. Static electricity
- D. Airborne contamination
Answer: C
NEW QUESTION 2
A particular database threat utilizes a SQL injection technique to penetrate a target system. How would an attacker use this technique to compromise a database?
- A. An attacker uses poorly designed input validation routines to create or alter SQL commands to gain access to unintended data or execute commands of the database
- B. An attacker submits user input that executes an operating system command to compromise a target system
- C. An attacker gains control of system to flood the target system with requests, preventing legitimate users from gaining access
- D. An attacker utilizes an incorrect configuration that leads to access with higher-than- expected privilege of the database
Answer: A
Explanation:
Using the poorly designed input validation to alter or steal data from a database is a SQL injection attack.
NEW QUESTION 3
Paul has just finished setting up his wireless network. He has enabled numerous security features such as changing the default SSID, enabling WPA encryption, and enabling MAC filtering on his wireless router. Paul notices that when he uses his wireless connection, the speed is sometimes 54 Mbps and sometimes it is only 24Mbps or less. Paul connects to his wireless router's management utility and notices that a machine with an unfamiliar name is connected through his wireless connection. Paul checks the router's logs and notices that the unfamiliar machine has the same MAC address as his laptop. What is Paul
seeing here?
- A. MAC spoofing
- B. Macof
- C. ARP spoofing
- D. DNS spoofing
Answer: A
NEW QUESTION 4
What is Form Scalpel used for?
- A. Dissecting HTML Forms
- B. Dissecting SQL Forms
- C. Analysis of Access Database Forms
- D. Troubleshooting Netscape Navigator
- E. Quatro Pro Analysis Tool
Answer: A
Explanation:
Form Scalpel automatically extracts forms from a given web page and splits up all fields for editing and manipulation.
NEW QUESTION 5
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server in your organization. They notice that there is excessive number of functions in the source code that might lead to buffer overflow. These C++ functions do not check bounds. Identify the line in the source code that might lead to buffer overflow?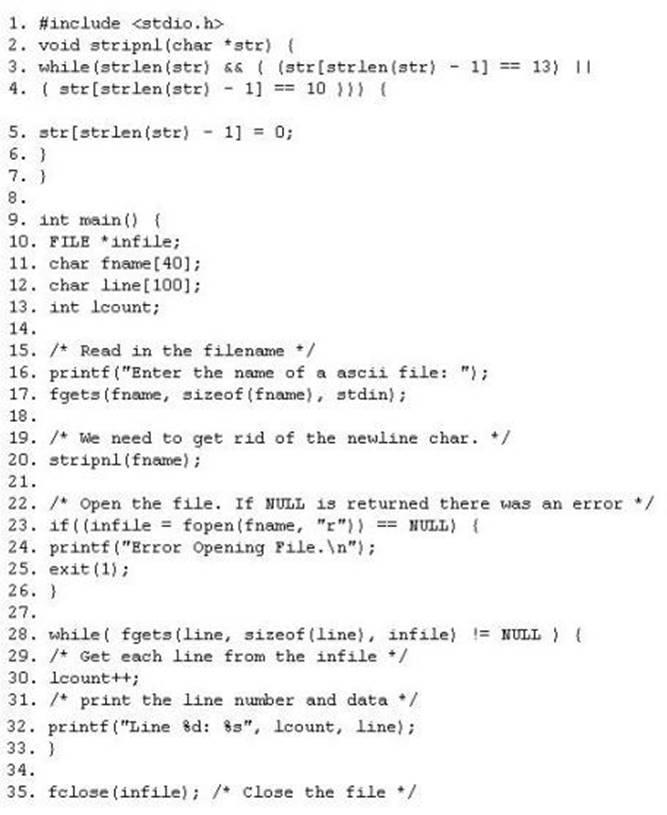
- A. 9A.9
- B. 17B.17
- C. 20C.20
- D. 32D.32
- E. 35E.35
Answer: B
NEW QUESTION 6
Information gathered from social networking websites such as Facebook, Twitter and LinkedIn can be used to launch which of the following types of attacks? (Choose two.)
- A. Smurf attack
- B. Social engineering attack
- C. SQL injection attack
- D. Phishing attack
- E. Fraggle attack
- F. Distributed denial of service attack
Answer: BD
NEW QUESTION 7
Which security strategy requires using several, varying methods to protect IT systems against attacks?
- A. Defense in depth
- B. Three-way handshake
- C. Covert channels
- D. Exponential backoff algorithm
Answer: A
NEW QUESTION 8
How does a denial-of-service attack work?
- A. A hacker prevents a legitimate user (or group of users) from accessing a service
- B. A hacker uses every character, word, or letter he or she can think of to defeat authentication
- C. A hacker tries to decipher a password by using a system, which subsequently crashes the network
- D. A hacker attempts to imitate a legitimate user by confusing a computer or even another person
Answer: A
NEW QUESTION 9
What is the primary drawback to using advanced encryption standard (AES) algorithm with a 256 bit key to share sensitive data?
- A. Due to the key size, the time it will take to encrypt and decrypt the message hinders
- B. efficient communication.
- C. To get messaging programs to function with this algorithm requires complex configurations.
- D. It has been proven to be a weak cipher; therefore, should not be trusted to protect sensitive data.
- E. It is a symmetric key algorithm, meaning each recipient must receive the key through a different channel than the message.
Answer: D
NEW QUESTION 10
While scanning a network you observe that all of the web servers in the DMZ are responding to ACK packets on port 80.
What can you infer from this observation?
- A. They are using Windows based web servers.
- B. They are using UNIX based web servers.
- C. They are not using an intrusion detection system.
- D. They are not using a stateful inspection firewall.
Answer: D
Explanation:
If they used a stateful inspection firewall this firewall would know if there has been a SYN-ACK before the ACK.
NEW QUESTION 11
You are the CIO for Avantes Finance International, a global finance company based in Geneva. You are responsible for network functions and logical security throughout the entire corporation. Your company has over 250 servers running Windows Server, 5000 workstations running Windows Vista, and 200 mobile users working from laptops on Windows 7.
Last week, 10 of your company's laptops were stolen from salesmen while at a conference in Amsterdam. These laptops contained proprietary company information. While doing damage assessment on the possible public relations nightmare this may become, a news story leaks about the stolen laptops and also that sensitive information from those computers was posted to a blog online.
What built-in Windows feature could you have implemented to protect the sensitive information on these laptops?
- A. You should have used 3DES which is built into Windows
- B. If you would have implemented Pretty Good Privacy (PGP) which is built into Windows, the sensitive information on the laptops would not have leaked out
- C. You should have utilized the built-in feature of Distributed File System (DFS) to protect the sensitive information on the laptops
- D. You could have implemented Encrypted File System (EFS) to encrypt the sensitive files on the laptops
Answer: D
NEW QUESTION 12
Jake works as a system administrator at Acme Corp. Jason, an accountant of the firm befriends him at the canteen and tags along with him on the pretext of appraising him about potential tax benefits. Jason waits for Jake to swipe his access card and follows him through the open door into the secure systems area. How would you describe Jason's behavior within a security context?
- A. Smooth Talking
- B. Swipe Gating
- C. Tailgating
- D. Trailing
Answer: C
NEW QUESTION 13
Which of the following parameters enables NMAP's operating system detection feature?
- A. NMAP -sV
- B. NMAP -oS
- C. NMAP -sR
- D. NMAP -O
Answer: D
NEW QUESTION 14
Pandora is used to attack network operating systems.
- A. Windows
- B. UNIX
- C. Linux
- D. Netware
- E. MAC OS
Answer: D
Explanation:
While there are not lots of tools available to attack Netware, Pandora is one that can be used.
NEW QUESTION 15
When using Wireshark to acquire packet capture on a network, which device would enable the capture of all traffic on the wire?
- A. Network tap
- B. Layer 3 switch
- C. Network bridge
- D. Application firewall
Answer: A
NEW QUESTION 16
What is the correct PCAP filter to capture all TCP traffic going to or from host
192.168.0.125 on port 25?
- A. tcp.src == 25 and ip.host == 192.168.0.125
- B. host 192.168.0.125:25
- C. port 25 and host 192.168.0.125
- D. tcp.port == 25 and ip.host == 192.168.0.125
Answer: D
NEW QUESTION 17
Take a look at the following attack on a Web Server using obstructed URL: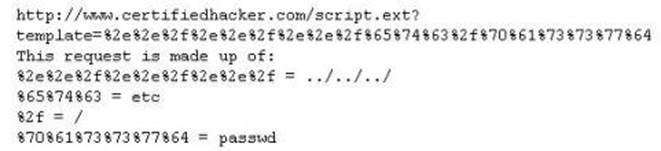
How would you protect from these attacks?
- A. Configure the Web Server to deny requests involving "hex encoded" characters
- B. Create rules in IDS to alert on strange Unicode requests
- C. Use SSL authentication on Web Servers
- D. Enable Active Scripts Detection at the firewall and routers
Answer: B
NEW QUESTION 18
Which set of access control solutions implements two-factor authentication?
- A. USB token and PIN
- B. Fingerprint scanner and retina scanner
- C. Password and PIN
- D. Account and password
Answer: A
NEW QUESTION 19
Samuel is the network administrator of DataX Communications, Inc. He is trying to configure his firewall to block password brute force attempts on his network. He enables blocking the intruder's IP address for a period of 24 hours' time after more than three unsuccessful attempts. He is confident that this rule will secure his network from hackers on the Internet.
But he still receives hundreds of thousands brute-force attempts generated from various IP addresses around the world. After some investigation he realizes that the intruders are using a proxy somewhere else on the Internet which has been scripted to enable the random usage of various proxies on each request so as not to get caught by the firewall rule.
Later he adds another rule to his firewall and enables small sleep on the password attempt so that if the password is incorrect, it would take 45 seconds to return to the user to begin another attempt. Since an intruder may use multiple machines to brute force the password, he also throttles the number of connections that will be prepared to accept from a particular IP address. This action will slow the intruder's attempts.
Samuel wants to completely block hackers brute force attempts on his network.
What are the alternatives to defending against possible brute-force password attacks on his site?
- A. Enforce a password policy and use account lockouts after three wrong logon attempts even though this might lock out legit users
- B. Enable the IDS to monitor the intrusion attempts and alert you by e-mail about the IP address of the intruder so that you can block them at theFirewall manually
- C. Enforce complex password policy on your network so that passwords are more difficult to brute force
- D. You cannot completely block the intruders attempt if they constantly switch proxies
Answer: D
NEW QUESTION 20
When writing shellcodes, you must avoid because these will end the string.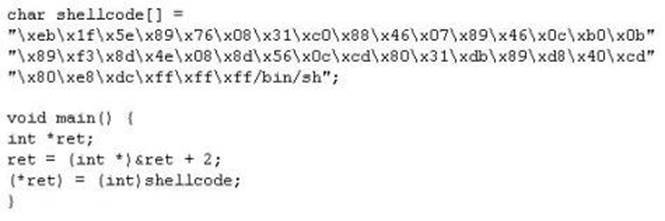
- A. Root bytes
- B. Null bytes
- C. Char bytes
- D. Unicode bytes
Answer: B
NEW QUESTION 21
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
- A. LibPcap
- B. WinPcap
- C. Wincap
- D. None of the above
Answer: B
Explanation:
WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets
bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
NEW QUESTION 22
John has scanned the web server with NMAP. However, he could not gather enough information to help him identify the operating system running on the remote host accurately.
What would you suggest to John to help identify the OS that is being used on the remote web server?
- A. Connect to the web server with a browser and look at the web page.
- B. Connect to the web server with an FTP client.
- C. Telnet to port 8080 on the web server and look at the default page code.
- D. Telnet to an open port and grab the banner.
Answer: D
Explanation:
Most people don’t care about changing the banners presented by applications listening to open ports and therefore you should get fairly accurate information when grabbing banners from open ports with, for example, a telnet application.
NEW QUESTION 23
Jane has just accessed her preferred e-commerce web site and she has seen an item she would like to buy. Jane considers the price a bit too steep; she looks at the page source code and decides to save the page locally to modify some of the page variables. In the context of web application security, what do you think Jane has changed?
- A. An integer variable
- B. A 'hidden' price value
- C. A 'hidden' form field value
- D. A page cannot be changed locally; it can only be served by a web server
Answer: C
Explanation:
Changing hidden form values is possible when a web site is poorly built and is trusting the visitors computer to submit vital data, like the price of a product, to the database.
NEW QUESTION 24
A consultant is hired to do physical penetration testing at a large financial company. In the first day of his assessment, the consultant goes to the company`s building dressed like an electrician and waits in the lobby for an employee to pass through the main access gate,
then the consultant follows the employee behind to get into the restricted area. Which type of attack did the consultant perform?
- A. Man trap
- B. Tailgating
- C. Shoulder surfing
- D. Social engineering
Answer: B
NEW QUESTION 25
What is the main disadvantage of the scripting languages as opposed to compiled programming languages?
- A. Scripting languages are hard to learn.
- B. Scripting languages are not object-oriented.
- C. Scripting languages cannot be used to create graphical user interfaces.
- D. Scripting languages are slower because they require an interpreter to run the code.
Answer: D
NEW QUESTION 26
Which of the following countermeasure can specifically protect against both the MAC Flood and MAC Spoofing attacks?
- A. Configure Port Security on the switch
- B. Configure Port Recon on the switch
- C. Configure Switch Mapping
- D. Configure Multiple Recognition on the switch
Answer: A
NEW QUESTION 27
Which of the following tools are used for enumeration? (Choose three.)
- A. SolarWinds
- B. USER2SID
- C. Cheops
- D. SID2USER
- E. DumpSec
Answer: BDE
Explanation:
USER2SID, SID2USER, and DumpSec are three of the tools used for system enumeration. Others are tools such as NAT and Enum. Knowing which tools are used in each step of the hacking methodology is an important goal of the CEH exam. You should spend a portion of your time preparing for the test practicing with the tools and learning to understand their output.
NEW QUESTION 28
After a client sends a connection request (SYN) packet to the server, the server will respond (SYN-ACK) with a sequence number of its choosing, which then must be acknowledged (ACK) by the client. This sequence number is predictable; the attack connects to a service first with its own IP address, records the sequence number chosen, and then opens a second connection from a forged IP address. The attack doesn't see the SYN-ACK (or any other packet) from the server, but can guess the correct responses. If the source IP address is used for authentication, then the attacker can use the one-sided communication to break into the server. What attacks can you successfully launch against a server using the above technique?
- A. Denial of Service attacks
- B. Session Hijacking attacks
- C. Web page defacement attacks
- D. IP spoofing attacks
Answer: B
NEW QUESTION 29
......
Recommend!! Get the Full CEH-001 dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/CEH-001-dumps/ (New 878 Q&As Version)
