Act now and download your EC-Council ECSAv10 test today! Do not waste time for the worthless EC-Council ECSAv10 tutorials. Download Updated EC-Council EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing exam with real questions and answers and begin to learn EC-Council ECSAv10 with a classic professional.
Online EC-Council ECSAv10 free dumps demo Below:
NEW QUESTION 1
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
- A. intitle:"exchange server"
- B. outlook:"search"
- C. locate:"logon page"
- D. allinurl:"exchange/logon.asp"
Answer: D
NEW QUESTION 2
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set.
What is Terri trying to accomplish by sending this IP packet?
- A. Poison the switch's MAC address table by flooding it with ACK bits
- B. Enable tunneling feature on the switch
- C. Trick the switch into thinking it already has a session with Terri's computer
- D. Crash the switch with a DoS attack since switches cannot send ACK bits
Answer: C
NEW QUESTION 3
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
- A. TCP port 152
- B. UDP port 177
- C. UDP port 123
- D. TCP port 113
Answer: C
NEW QUESTION 4
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and G.
Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- A. 802.11b
- B. 802.11g
- C. 802.11-Legacy
- D. 802.11n
Answer: A
NEW QUESTION 5
Harold is a web designer who has completed a website for ghttech.net. As part of the maintenance agreement he signed with the client, Harold is performing research online and seeing how much exposure the site has received so far. Harold navigates to google.com and types in the following search.
link:www.ghttech.net
What will this search produce?
- A. All sites that link to ghttech.net
- B. Sites that contain the code: link:www.ghttech.net
- C. All sites that ghttech.net links to
- D. All search engines that link to .net domains
Answer: A
NEW QUESTION 6
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
- A. Penetration Testing Agreement
- B. Rules of Behavior Agreement
- C. Liability Insurance
- D. Non-Disclosure Agreement
Answer: D
NEW QUESTION 7
From where can clues about the underlying application environment can be collected?
- A. From source code
- B. From file types and directories
- C. From executable file
- D. From the extension of the file
Answer: D
NEW QUESTION 8
Identify the injection attack represented in the diagram below: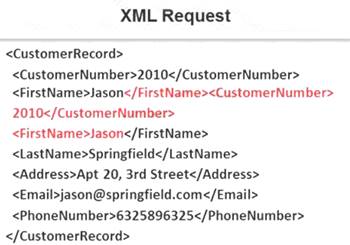
- A. XPath Injection Attack
- B. XML Request Attack
- C. XML Injection Attack
- D. Frame Injection Attack
Answer: C
NEW QUESTION 9
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer: C
NEW QUESTION 10
What will the following URL produce in an unpatched IIS Web Server?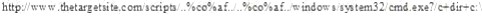
- A. Execute a buffer flow in the C: drive of the web server
- B. Insert a Trojan horse into the C: drive of the web server
- C. Directory listing of the C:windowssystem32 folder on the web server
- D. Directory listing of C: drive on the web server
Answer: D
NEW QUESTION 11
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?
- A. Reverse Address Resolution Protocol (RARP)
- B. HTTP (Hypertext Transfer Protocol)
- C. SMTP (Simple Mail Transfer Protocol)
- D. Telnet
Answer: A
NEW QUESTION 12
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 13
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 14
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
- A. Testing to provide a more complete view of site security
- B. Testing focused on the servers, infrastructure, and the underlying software, including the target
- C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
- D. Testing performed from a number of network access points representing each logical and physical segment
Answer: B
NEW QUESTION 15
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
- A. Inference-based Assessment
- B. Service-based Assessment Solutions
- C. Product-based Assessment Solutions
- D. Tree-based Assessment
Answer: A
NEW QUESTION 16
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A. PortQry
- B. Netstat
- C. Telnet
- D. Tracert
Answer: A
NEW QUESTION 17
What are the 6 core concepts in IT security?
- A. Server management, website domains, firewalls, IDS, IPS, and auditing
- B. Authentication, authorization, confidentiality, integrity, availability, and non-repudiation
- C. Passwords, logins, access controls, restricted domains, configurations, and tunnels
- D. Biometrics, cloud security, social engineering, DoS attack, viruses, and Trojans
Answer: B
NEW QUESTION 18
Which one of the following log analysis tools is a Cisco Router Log Format log analyzer and it parses logs, imports them into a SQL database (or its own built-in database), aggregates them, and generates the dynamically filtered reports, all through a web interface?
- A. Event Log Tracker
- B. Sawmill
- C. Syslog Manager
- D. Event Log Explorer
Answer: B
NEW QUESTION 19
Output modules allow Snort to be much more flexible in the formatting and presentation of output to its users. Snort has 9 output plug-ins that push out data in different formats. Which one of the following output plug-ins allows alert data to be written in a format easily importable to a database?
- A. unified
- B. csv
- C. alert_unixsock
- D. alert_fast
Answer: B
NEW QUESTION 20
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 21
Which of the following statements is true about the LM hash?
- A. Disabled in Windows Vista and 7 OSs
- B. Separated into two 8-character strings
- C. Letters are converted to the lowercase
- D. Padded with NULL to 16 characters
Answer: A
NEW QUESTION 22
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
- A. Passive IDS
- B. Active IDS
- C. Progressive IDS
- D. NIPS
Answer: B
NEW QUESTION 23
Which of the following defines the details of services to be provided for the client’s organization and the list of services required for performing the test in the organization?
- A. Draft
- B. Report
- C. Requirement list
- D. Quotation
Answer: D
NEW QUESTION 24
What is the difference between penetration testing and vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
- B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer: A
NEW QUESTION 25
Which one of the following 802.11 types has WLAN as a network support?
- A. 802.11b
- B. 802.11-Legacy
- C. 802.11n
- D. 802.11g
Answer: C
NEW QUESTION 26
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, statefull firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet.
Why is that?
- A. IPSEC does not work with packet filtering firewalls
- B. NAT does not work with IPSEC
- C. NAT does not work with statefull firewalls
- D. Statefull firewalls do not work with packet filtering firewalls
Answer: B
NEW QUESTION 27
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
- A. EXTRACT* FROM StudentTable WHERE roll_number = 1 order by 1000
- B. DUMP * FROM StudentTable WHERE roll_number = 1 AND 1=1—
- C. SELECT * FROM StudentTable WHERE roll_number = '' or '1' = '1‘
- D. RETRIVE * FROM StudentTable WHERE roll_number = 1'#
Answer: C
NEW QUESTION 28
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.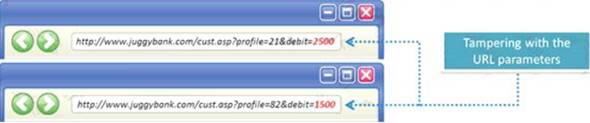
What is the best way to protect web applications from parameter tampering attacks?
- A. Validating some parameters of the web application
- B. Minimizing the allowable length of parameters
- C. Using an easily guessable hashing algorithm
- D. Applying effective input field filtering parameters
Answer: D
NEW QUESTION 29
An "idle" system is also referred to as what?
- A. Zombie
- B. PC not being used
- C. Bot
- D. PC not connected to the Internet
Answer: A
NEW QUESTION 30
Identify the correct formula for Return on Investment (ROI).
- A. ROI = ((Expected Returns – Cost of Investment) / Cost of Investment) * 100
- B. ROI = (Expected Returns + Cost of Investment) / Cost of Investment
- C. ROI = (Expected Returns Cost of Investment) / Cost of Investment
- D. ROI = ((Expected Returns + Cost of Investment) / Cost of Investment) * 100
Answer: C
NEW QUESTION 31
......
Thanks for reading the newest ECSAv10 exam dumps! We recommend you to try the PREMIUM 2passeasy ECSAv10 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/ECSAv10/ (201 Q&As Dumps)
