we provide Simulation Red-Hat EX300 actual exam which are the best for clearing EX300 test, and to get certified by Red-Hat Red Hat Certified Engineer - RHCE (v6+v7). The EX300 Questions & Answers covers all the knowledge points of the real EX300 exam. Crack your Red-Hat EX300 Exam with latest dumps, guaranteed!
NEW QUESTION 1
In accordance with the following requirements to deploy ssh login service:
harry belongs to example.com which can remote login your systems.
However, users of remote.test cannot use ssh login to your machine.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
Notice:
tcp_wrappers has two configuration files and their priority level is /etc/hosts.allow->/etc/hosts.deny
NEW QUESTION 2
Prevent Mary from performing user configuration tasks in your system.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
Conclusions:
1. I find that it is common to add various service access limits in the exam RHCE. The exercises like: require
one network segment can be accessed another network segments can not be accessed, the following are some conclusions for various service:
tcp_wrappers:/etc/hosts.allow,/etc/hosts.deny
tcp_wrappers can filter the TCP’s accessing service. TCP whether has the filtering function which depends on this service whether use the function library of tcp_wrappers, or this service whether has the xinetd process of starting function of tcp_wrappers. tcp_wrappers’s main configuration file is /etc/hosts.allow,/etc/hosts.deny.
And the priority of the documents in hosts. allow is higher than hosts. deny. Visit will be passed if no match was found.
sshd,vsftpd can use the filtering service of tcp_wrappers. Configuration example:
Notice:
The two configuration files’ syntax can refer to hosts_access (5) and hosts_options(5) sshd_config
There are four parameters in this configuration file: DenyUsers, AllowUsers, DenyGroups, AllowGroups, they are used to limit some users or user groups to proceed Remote Login through the SSH. These parameters’ priority level is DenyUsers->AllowUsers->DenyGroups->AllowGroups
Configuration example:
httpd Service
Through the /etc/httpd/conf/httpd.conf in parameters, can add <Directory> to control the url access. Just as: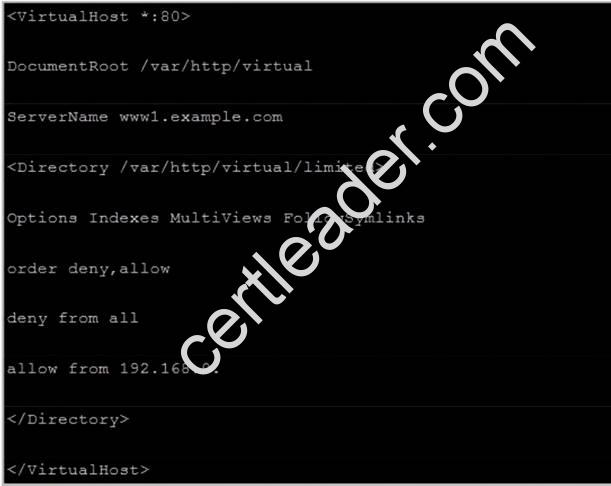
Notice:
So pay attention, deny’s and allow’s priority level in order deny,allow is: the backer has the higher priority level. But here, allow’s priority has a higher priority level.
nfs Service
nfs service directly control the visits through file /etc/exports, just as:
samba Service
Parameter hosts allow in /etc/samba/smb.conf which is used as Access Control, just as:
2. Paying attention to use Mount parameters: _netdev,defaults when you are mounting ISCSI disk.
3. Stop the NetworkManager
/etc/init.d/NetworkManager stop chkconfig NetworkManager off
4. When you are deploying ifcfg-ethX, add parameters: PEERDNS=no
5. Empty the firewall in RHCSARHCE: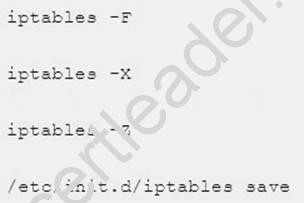
6. Narrow lv steps: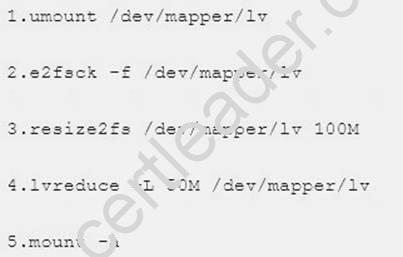
7. Mount the using command - swap which is newly added in /etc/fstab
8. If Verification is not passed when you are installing software, can import public key: rpm import
/etc/pki/rpm…/…release and so on. In yum.repo, you also can deploy gpgkey, for example, gpgkey=/etc/pki/rpm…/…release
9. When you are using “Find” command to search and keep these files, paying attention to use cp -a to copy files if you use user name and authority as your searching methods.
NEW QUESTION 3
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Secured webserver.
Configure the website https://serverX.example.com with TLS
SSLCertificate file http://classroom.example.com/pub/rhce/tls/certs/system1.networkX.crt
SSLCertificatekeyfile http://classroom.example.com/pub/rhce/tls/private/system1.networkX.key
SSL CA certificate file http://classroom.example.com/pub/example-ca.crt
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 4
Add a cron schedule to take full backup of /home on every day at 5:30 pm to /dev/st0 device.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
1. vi /var/schedule
30 17 * * * /sbin/dump -0u /dev/st0 /dev/hda7
2. crontab /var/schedule
3. service crond restart
We can add the cron schedule either by specifying the scripts path on /etc/crontab file or by creating on text file on crontab pattern.
cron helps to schedule on recurring events. Pattern of cron is: Minute Hour Day of Month Month Day of Week Commands
0-59 0-23 1-31 1-12 0-7 where 0 and 7 mean Sunday.
Note * means every. To execute the command on every two minutes */2.
NEW QUESTION 5
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Configure smb access.
Share the /sambadir directory via SMB on serverX
Your SMB server must be a member of the TESTGROUP workgroup
The share name must be data
The data share must be available to example.com domain clients only
The data share must be browseable
susan must have read access to the share, authenticating with the same password “password”, if necessary
Configure the serverX to share /opstack with SMB share name must be cluster
The user frankenstein has readable, writeable, accessable to the /opstack SMB share
Both users should have the SMB passwd “SaniTago”
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 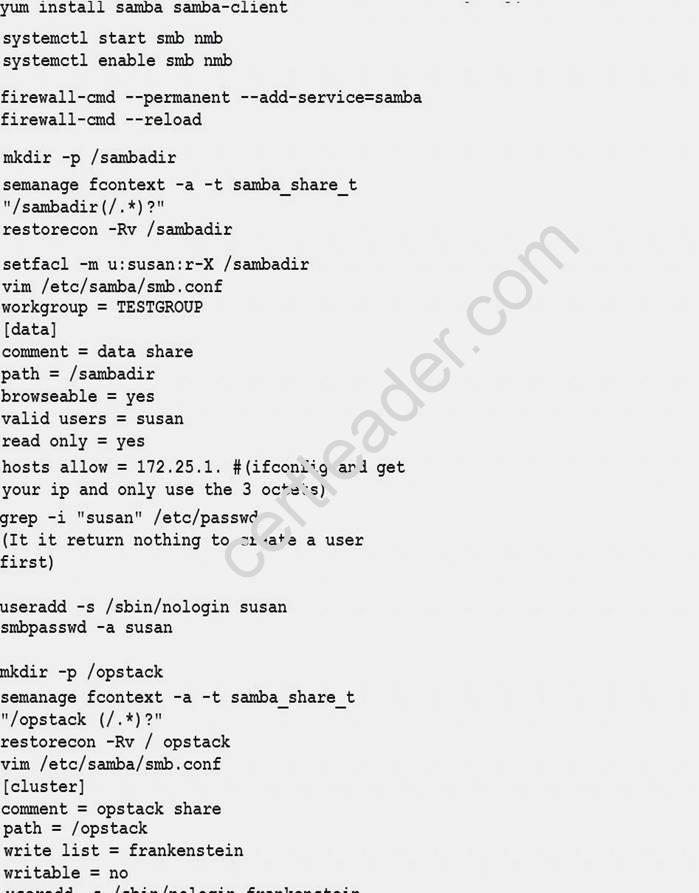
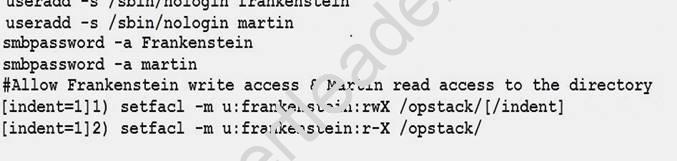
[/indent]
NEW QUESTION 6
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Script2.
Create a script on serverX called /root/createusers
When this script is called with the argument, it should add all the users from the file
Download the file from station.network0.example.c">
http://station.network0.example.com/pub/testfile
All users should have the login shell as /bin/false, password not required
When this script is called with any other argument, it should print the message as “Input File Not Found”
When this script is run without any argument, it should display “Usage:/root/createusers”
NOTE: if the users are added no need to delete
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 7
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client. Password for both of the two systems is atenorth
System’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this domain, this domain provides the following user account: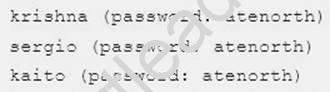
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you made still can be operated after the restart without manual intervention, virtual machine instances of all examinations must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the host and network, although you correctly configured the network service but would have to allow the host or network is blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification, each exam question has some radio buttons to help you identify which questions you have already completed or not completed. Certainly, you do not need to care these buttons if you don’t need them.
Mount a NFS Share
Mount a NFS Share to system1.domain11.example.com on the system2, as required:
1. Mount the /public to the directory /mnt/nfsmount
2. Mount the /protected to the directory /mnt/nfssecure, in a security way, key download from the following URL:
http://host.domain11.example.com/materials/nfs_client.keytab
3. User deepak can create files in /mnt/nfssecure/project
4. These file systems automatically hang up when the system is started
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 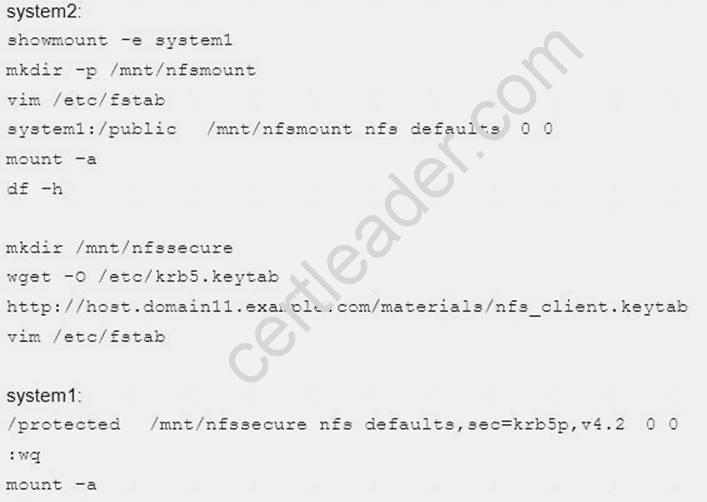
NEW QUESTION 8
There are two different networks 192.168.0.0/24 and 192.168.1.0/24. Where 192.168.0.254 and 192.168.1.254 IP Address are assigned on Server. Verify your network settings by pinging 192.168.1.0/24 Network's Host.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 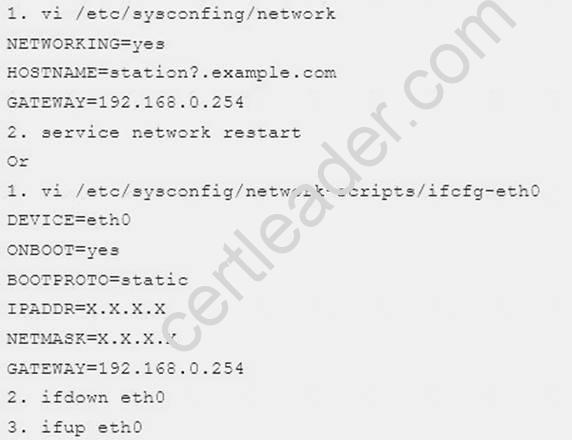
NEW QUESTION 9
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client. Password for both of the two systems is atenorth
System’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this domain, this domain provides the following user account: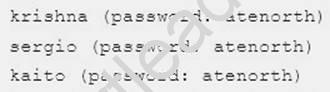
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you made still can be operated after the restart without manual intervention, virtual machine instances of all examinations must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the host and network, although you correctly configured the network service but would have to allow the host or network is blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification, each exam question has some radio buttons to help you identify which questions you have already completed or not completed. Certainly, you do not need to care these buttons if you don’t need them.
Configure NFS service
Configure the NFS service on the system1, as required:
1. Share the directory /public in read only way, just can be accessed by systems in domain11.example.com at the same time.
2. Share the directory /protected in rad and write way, Kerberos security encryption required, you can use the key provided by the following URL:
http://host.domain11.example.com/materials/nfs_server.keytab
3. The directory /protected should contain the sub directory named project and the owner name is deepak;
4. User deepak can access /protected/project in read and write ways
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
system1: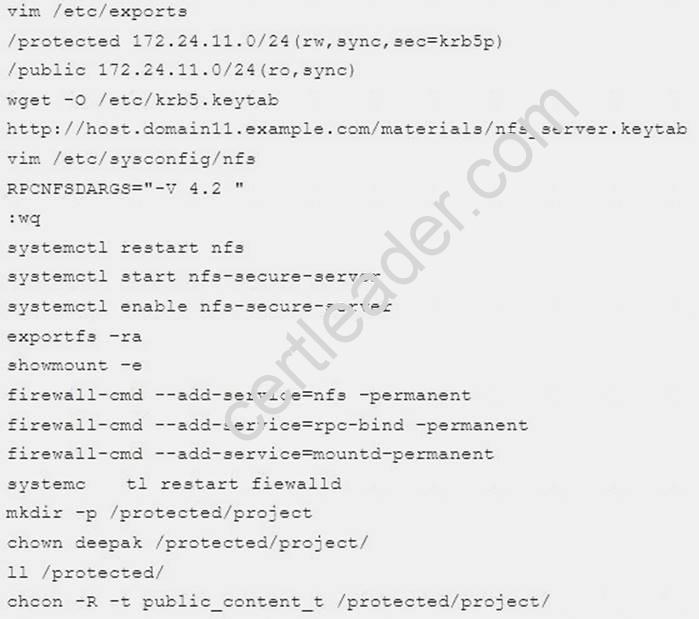
NEW QUESTION 10
You access the iscsi shared storage. The storage server ip is 172.24.30.100. Separate of 1500M space, format as ext3 file system, mount under /mnt/data, and make sure the root-start automatically mount.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 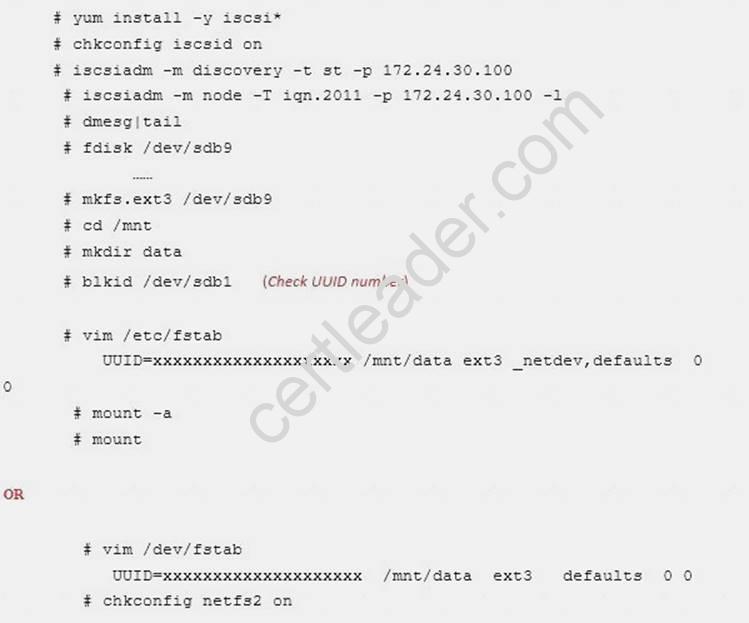
NEW QUESTION 11
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
NFS server.
Configure serverX with the following requirements
Share the /nfsshare directory within the example.com domain clients only, share must be writable
Share the /nfssecure, enable krb5p security to secure access to the NFS share from URL
http://station.network0.example.com/pub/keytabs/serverX.keytab
Create a directory named as protected under /nfssecure
The exported directory should have read/write access from all subdomains of the example.com domain Ensure the directory /nfssecure/protected should be owned by the user harry with read/write permission
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 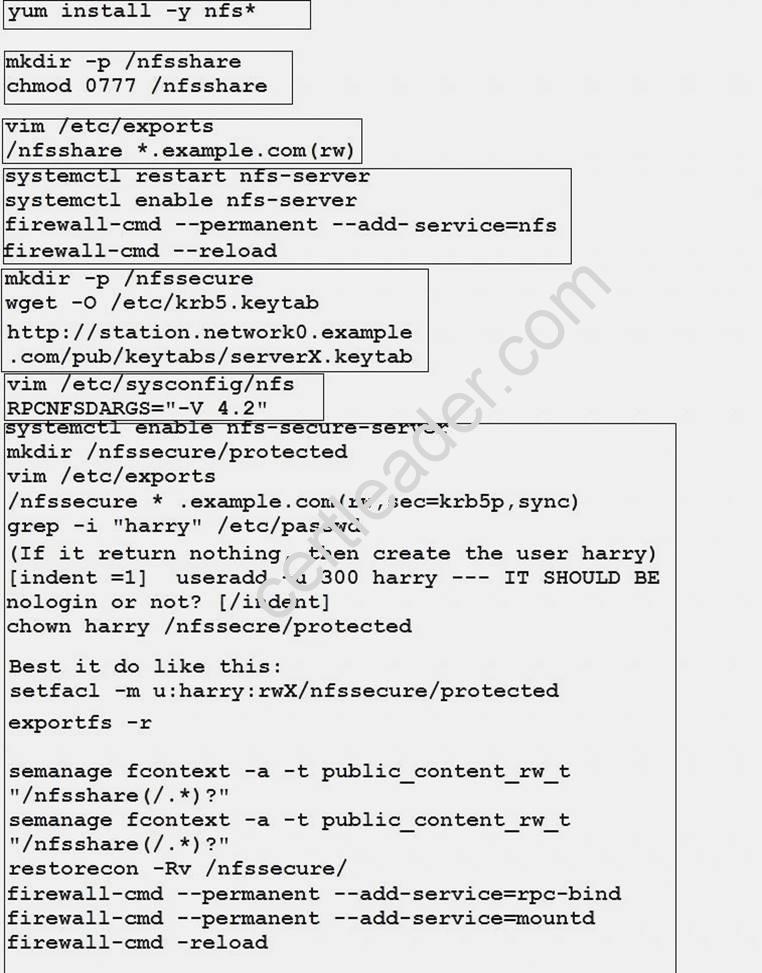

NEW QUESTION 12
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Customize the User Environment
Create a command called qstat on both serverX and desktop.
It should be able to execute the following command (ps –eo pid, tid, class, rtprio, ni, pri, psr, pcpu, stat, wchan:14, comm).
The command should be executable by all users.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 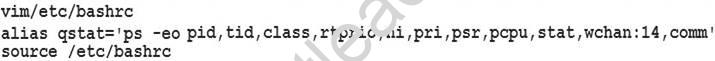
NEW QUESTION 13
Create the directory /storage and group owner should be the sysusers group.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
chgrp sysusers /storage
Verify using ls -ld /storage command.
You should get like drwxr-x--- 2 root sysusers 4096 Mar 16 17:59 /storage chgrp command is used to change the group ownership of particular files or directory.
Another way you can use the chown command. chown root:sysusers /storage
NEW QUESTION 14
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client. Password for both of the two systems is atenorth
System’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this domain, this domain provides the following user account: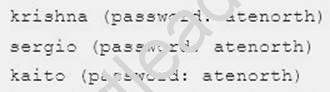
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you made still can be operated after the restart without manual intervention, virtual machine instances of all examinations must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the host and network, although you correctly configured the network service but would have to allow the host or network is blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification, each exam question has some radio buttons to help you identify which questions you have already completed or not completed. Certainly, you do not need to care these buttons if you don’t need them.
Configure a Database
Create a Maria DB database named Contacts on system1 and meet the following requirements at the same time:
The database should contain the contents of the database replication, URL for copying files is:
http://rhgls.domain11.example.com/materials/users.mdb
Database just can be accessed by localhost
In addition to the root user, this database only can be searched by user Luigi, user’s password is redhat
The password for root user is redhat, does not allow empty password
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 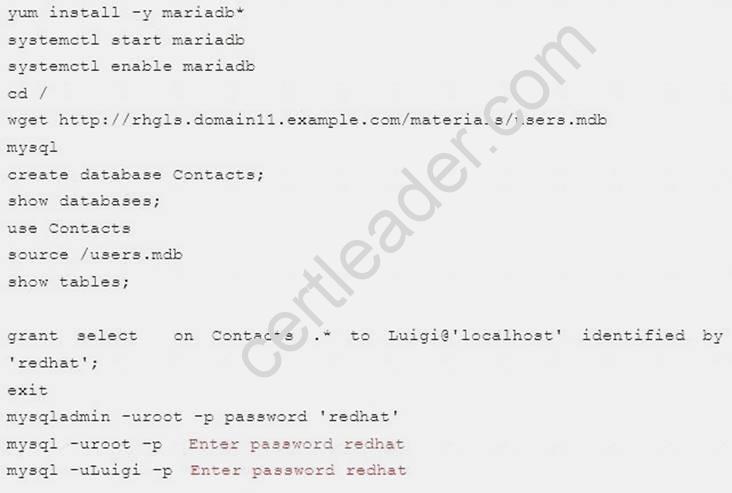
NEW QUESTION 15
Write a script /root/program. The request is when you input the kernel parameters for script, the script should return to user. When input the user parameters, the script should return to kernel. And when the script has no parameters or the parameters are wrong, the standard error output should be “usage:/root/program kernel|user”.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 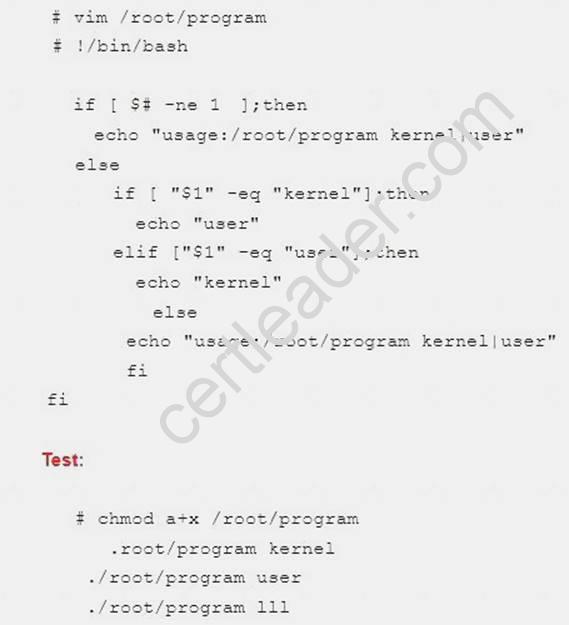
NEW QUESTION 16
One Package named zsh is dump on ftp://server1.example.com under pub directory. Install the package from ftp server.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
rpm -ivh ftp://server1.example.com/pub/zsh-*
Package will install
rpm command is used to install, update and remove the package, -i means install, -v means verbose and -h means display the hash mark.
NEW QUESTION 17
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Webpage content modification.
Implement website for serverX.examp">http://serverX.example.com/owndir
Create a directory named as “owndir” under the document root of webserver
Download station.network0.example.com/pub">
http://station.network0.example.com/pub/rhce/restrict.html
Rename the file into ondex.html
The content of the owndir should be visible to everyone browsing from your local system but should not be accessible from other location
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 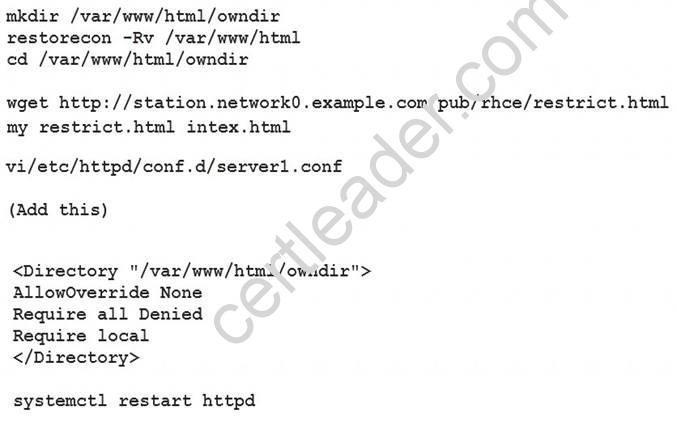
NEW QUESTION 18
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client. Password for both of the two systems is atenorth
System’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this domain, this domain provides the following user account:
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you made still can be operated after the restart without manual intervention, virtual machine instances of all examinations must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the host and network, although you correctly configured the network service but would have to allow the host or network is blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification, each exam question has some radio buttons to help you identify which questions you have already completed or not completed. Certainly, you do not need to care these buttons if you don’t need them.
Create a script
Create a script named /root/foo.sh on the system1, make it provide the following characteristics:
When running /root/foo.sh redhat, the output is fedora
When running /root/foo.sh fedora, the output is redhat
When there is no parameter or parameter is not redhat or fedora, the following information will be generated by the error output: /root/foo.sh redhat:fedora
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 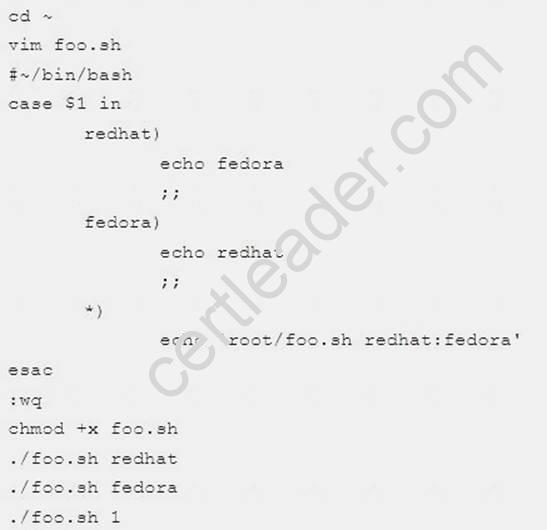
NEW QUESTION 19
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client. Password for both of the two systems is atenorth
System’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this domain, this domain provides the following user account:
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you made still can be operated after the restart without manual intervention, virtual machine instances of all examinations must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the host and network, although you correctly configured the network service but would have to allow the host or network is blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain
my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification, each exam question has some radio buttons to help you identify which questions you have already completed or not completed. Certainly, you do not need to care these buttons if you don’t need them.
Configure the SSH Access as required:
Users can visit your two virtual machine systems via clients of domain group3.example.com through SSH remote.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Solution 1:
Modify file /etc/hosts.allow Add a line: sshd: 172.24.11. Modify file /etc/hosts.deny Add a line: sshd: 172.25.0.
Both of them need to be configured. Solution 2:
Add a firewall
firewall-cmd –zone=block --add-source=172.25.11.0/24 --permanent firewall-cmd –reload Both of them need to be configured
NEW QUESTION 20
Make Secondary belongs the jeff and marion users on sysusers group. But harold user should not belongs to sysusers group.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
usermod -G sysusers jeff
usermod -G sysuser marion
Verify by reading /etc/group file Note:
Using usermod command we can make user belongs to different group. There are two types of group one primary and another is secondary. Primary group can be only one but user can belong to more than one group as secondary.
usermod -g groupname username - To change the primary group of the user. usermod -G groupname username
- To make user belongs to secondary group.
NEW QUESTION 21
Configure the ftp to allow anonymously download the directory /var/ftp/pub, and reject the domain t3gg.com to access.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 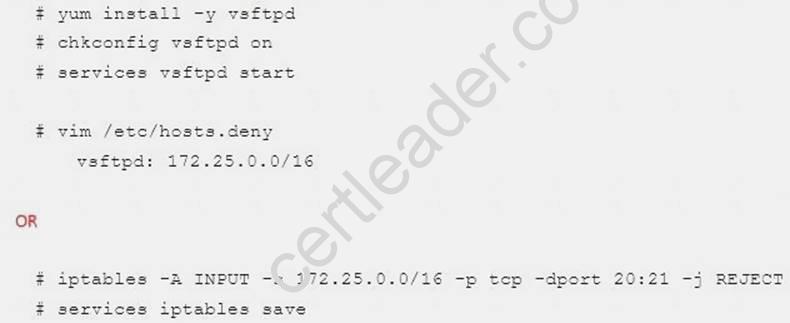
NEW QUESTION 22
Give Full Permission to owner user and owner group member but no permission to others on /data.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
We can change the permission of file/directory either character symbol method or numeric method. Permission:
r-Read w-Write
x-Execute Permission Category u- Owner User g- Owner Group
o- Others Operators
+ -> Add the Permissions
- ->Remove the Permissions = ->Assign the Permissions Numeric Method: 4 -> Read
2 -> Write
1 -> Execute
Total: 7, total for owner user, owner group member and for others: 777
1. chmod u+rwx /data
2 .chmod g+rwx /data
3. chmod o-rwx /data or
chmod 770 /data
4 Verify the /data: ls -ld /data
5. You will get drwxrwx---
NEW QUESTION 23
Please open the ip_forward and take effect permanently.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 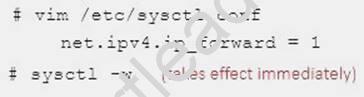
If no “sysctl.conf” option, use these commands: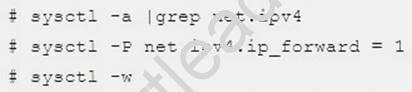
NEW QUESTION 24
Configure the nfs server, share the /common directory to domain30.example.com, and allow client to have the root user right when access as a root user.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 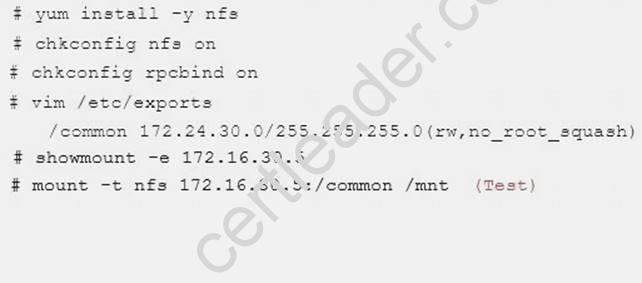
NEW QUESTION 25
......
P.S. Easily pass EX300 Exam with 88 Q&As Dumpscollection Dumps & pdf Version, Welcome to Download the Newest Dumpscollection EX300 Dumps: http://www.dumpscollection.net/dumps/EX300/ (88 New Questions)
