Master the GCIA GIAC Certified Intrusion Analyst content and be ready for exam day success quickly with this Testking GCIA dumps. We guarantee it!We make it a reality and give you real GCIA questions in our GIAC GCIA braindumps.Latest 100% VALID GIAC GCIA Exam Questions Dumps at below page. You can use our GIAC GCIA braindumps and pass your exam.
Free GCIA Demo Online For GIAC Certifitcation:
NEW QUESTION 1
What is the function of PING LOCALHOST command?
- A. It verifies that DNS is correctly set up to allow communication with a host, named LOCALHO S
- B. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the domain controlle
- C. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the successfully initialized IP addres
- D. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the loopback address 127.0.0.1.
Answer: D
NEW QUESTION 2
Which of the following is a technique of attacks in which the attacker secretly listens to the private conversation between victims?
- A. Dialler attack
- B. Denial of service
- C. Eavesdropping
- D. Intrusion
Answer: C
NEW QUESTION 3
Which of the following utilities produces the output shown in the image below?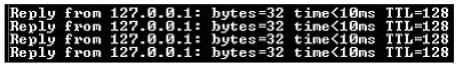
- A. IPCONFIG
- B. PING
- C. PATHPING
- D. TRACERT
Answer: B
NEW QUESTION 4
Which of the following user authentications are supported by the SSH-1 protocol but not by the SSH-2 protocol?
Each correct answer represents a complete solution. Choose all that apply.
- A. TIS authentication
- B. Rhosts (rsh-style) authentication
- C. Kerberos authentication
- D. Password-based authentication
Answer: ABC
NEW QUESTION 5
Which of the following types of firewall functions by creating two different communications, one between the client and the firewall, and the other between the firewall and the end server?
- A. Stateful firewall
- B. Proxy-based firewall
- C. Packet filter firewall
- D. Endian firewall
Answer: B
NEW QUESTION 6
Which of the following is a checksum algorithm?
- A. Hash buster
- B. Snort
- C. Adler-32
- D. Dsniff
Answer: C
NEW QUESTION 7
Which of the following is the default port for DNS zone transfer?
- A. Port 21
- B. Port 80
- C. Port 23
- D. Port 53
Answer: D
NEW QUESTION 8
You work as a Network Administrator for a bank. For securing the bank's network, you configure a firewall and an IDS. In spite of these security measures, intruders are able to attack the network.
After a close investigation, you find that your IDS is not configured properly and hence is unable to generate alarms when needed. What type of response is the IDS giving?
- A. False Positive
- B. True Negative
- C. False Negative
- D. True Positive
Answer: C
NEW QUESTION 9
Which of the following is an open-source Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software?
- A. Nmap
- B. Internet bot
- C. Dsniff
- D. Nikto
Answer: D
NEW QUESTION 10
Which of the following programs in UNIX is used to identify and fix lost blocks or orphans?
- A. File Check (fck)
- B. Block Check (bsck)
- C. Lost Block (lck)
- D. Filesystem Check (fsck)
Answer: D
NEW QUESTION 11
Which of the following file systems supports the hot fixing feature?
- A. FAT16
- B. exFAT
- C. NTFS
- D. FAT32
Answer: C
NEW QUESTION 12
Which of the following commands prints out the headers of packets regarding the boolean expression?
- A. tcpdump
- B. vmstat
- C. iftop
- D. iostat
Answer: A
NEW QUESTION 13
Smith works as a Network Administrator for HCP Inc. He sets up a DNS server on the network and enables DNS service on all computers. However, DNS is not working properly. Which of the following commands should Smith use to verify the DNS configuration?
- A. ping
- B. nslookup
- C. tracert
- D. pathping
Answer: B
NEW QUESTION 14
Victor works as a professional Ethical Hacker for SecureEnet Inc. He has been assigned a job to test an image, in which some secret information is hidden, using Steganography. Victor performs the following techniques to accomplish the task:
* 1. Smoothening and decreasing contrast by averaging the pixels of the area where significant color transitions occurs.
* 2. Reducing noise by adjusting color and averaging pixel value.
* 3. Sharpening, Rotating, Resampling, and Softening the image.
Which of the following Steganography attacks is Victor using?
- A. Chosen-Stego Attack
- B. Active Attacks
- C. Stegdetect Attack
- D. Steg-Only Attack
Answer: B
NEW QUESTION 15
What is the name of the group of blocks which contains information used by the operating system in Linux system?
- A. logblock
- B. Bootblock
- C. Superblock
- D. Systemblock
Answer: C
NEW QUESTION 16
John works as a professional Ethical Hacker. He has been assigned a project for testing the security of www.we-are-secure.com. He wants to corrupt an IDS signature database so that performing attacks on the server is made easy and he can observe the flaws in the We-are-secure server. To perform his task, he first of all sends a virus that continuously changes its signature to avoid detection from IDS. Since the new signature of the virus does not match the old signature, which is entered in the IDS signature database, IDS becomes unable to point out the malicious virus. Which of the following IDS evasion attacks is John performing?
- A. Insertion attack
- B. Session splicing attack
- C. Evasion attack
- D. Polymorphic shell code attack
Answer: D
NEW QUESTION 17
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. You are configuring an Internet connection on a server. Which of the following servers filters outbound Web traffic on the network?
- A. Proxy server
- B. DNS server
- C. WINS server
- D. DHCP server
Answer: A
NEW QUESTION 18
Which of the following is an example of a social engineering attack?
- A. Phishing
- B. Man-in-the-middle attack
- C. Browser Sniffing
- D. E-mail bombing
Answer: A
NEW QUESTION 19
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to send malicious data packets in such a manner that one packet fragment overlaps data from a previous fragment so that he can perform IDS evasion on the We-are-secure server and execute malicious data. Which of the following tools can he use to accomplish the task?
- A. Hunt
- B. Alchemy Remote Executor
- C. Mendax
- D. Ettercap
Answer: C
NEW QUESTION 20
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
- A. portsentry
- B. libnids
- C. nmap
- D. scanlogd
Answer: ABD
NEW QUESTION 21
......
P.S. Easily pass GCIA Exam with 508 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy GCIA Dumps: https://www.2passeasy.com/dumps/GCIA/ (508 New Questions)
