Exambible offers free demo for GCIA exam. "GIAC Certified Intrusion Analyst", also known as GCIA exam, is a GIAC Certification. This set of posts, Passing the GIAC GCIA exam, will help you answer those questions. The GCIA Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GCIA exams and revised by experts!
Online GIAC GCIA free dumps demo Below:
NEW QUESTION 1
Which of the following tools is used to detect wireless LANs using the 802.11b, 802.11a, and 802.11g WLAN standards on the Windows platform?
- A. Cain
- B. AiroPeek
- C. NetStumbler
- D. Snort
Answer: C
NEW QUESTION 2
Adam works as a professional Computer Hacking Forensic Investigator, a project has been assigned to him to investigate and examine files present on suspect's computer. Adam uses a tool with the help of which he can examine recovered deleted files, fragmented files, and other corrupted data. He can also examine the data, which was captured from the network, and access the physical RAM, and any processes running in virtual memory with the help of this tool. Which of the following tools is Adam using?
- A. Vedit
- B. WinHex
- C. HxD
- D. Evidor
Answer: B
NEW QUESTION 3
Which of the following tools works by using standard set of MS-DOS commands and can create an MD5 hash of an entire drive, partition, or selected files?
- A. DriveSpy
- B. Ontrack
- C. Device Seizure
- D. Forensic Sorter
Answer: A
NEW QUESTION 4
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
- A. Command injection attack
- B. Code injection attack
- C. Cross-Site Request Forgery
- D. Cross-Site Scripting attack
Answer: B
NEW QUESTION 5
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. The network contains a Windows Server 2008 Core computer. You want to install the DNS server role on the Windows Server 2008 Core computer. Which of the following commands will you use to accomplish the task?
- A. start /w ocsetup DnsServercorerole
- B. net start "dns server"
- C. start /w ocsetup DNS-Server-Core-Role
- D. start /w ocsetup DnsServer
Answer: C
NEW QUESTION 6
Which of the following statements is NOT true about the file slack spaces in Windows operating system?
- A. File slack is the space, which exists between the end of the file and the end of the last clust e
- B. Large cluster size will decrease the volume of the file slac
- C. File slack may contain data from the memory of the syste
- D. It is possible to find user names, passwords, and other important information in slac
Answer: B
NEW QUESTION 7
Which of the following wireless network standards operates on the 5 GHz band and transfers data at a rate of 54 Mbps?
- A. 802.11g
- B. 802.11a
- C. 802.11u
- D. 802.11b
Answer: B
NEW QUESTION 8
Adam, an expert computer user, doubts that virus named love.exe has attacked his computer. This virus acquires hidden and read-only attributes, so it is difficult to delete it. Adam decides to delete virus file love.exe from the command line. He wants to use del command for this purpose. Which of the following switches will he use with del command to delete hidden and read only-files?
- A. del /f /ah
- B. del /q /ar
- C. del /p /ar
- D. del /q
Answer: A
NEW QUESTION 9
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
- A. Encapsulating Security Payload
- B. Internet Key Exchange
- C. Skinny Client Control Protocol
- D. Authentication Header
Answer: ABD
NEW QUESTION 10
Which of the following types of firewall ensures that the packets are part of the established session?
- A. Switch-level firewall
- B. Application-level firewall
- C. Stateful inspection firewall
- D. Circuit-level firewall
Answer: C
NEW QUESTION 11
Which of the following commands will you use to display ARP packets in the snort-output?
- A. snort -v -i eth 0
- B. snort -d -v -i eth 0
- C. snort -dev -i eth 0
- D. snort -deva -i eth 0
Answer: D
NEW QUESTION 12
Which of the following utilities produces the output displayed in the image below?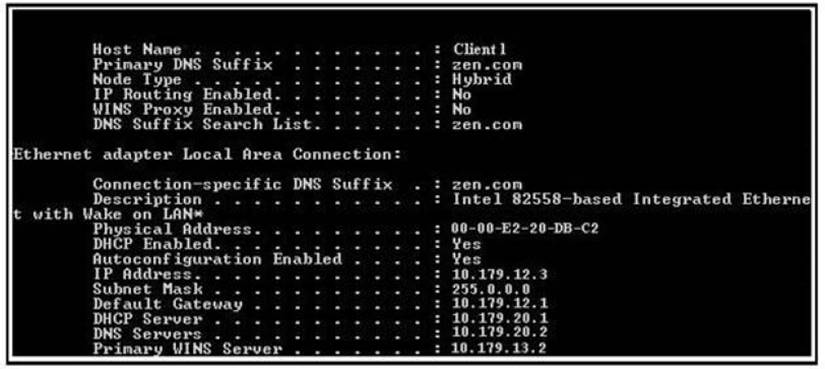
- A. IPCONFIG
- B. TRACERT
- C. PING
- D. PATHPING
Answer: A
NEW QUESTION 13
Which of the following distributes incorrect IP address to divert the traffic?
- A. IP spoofing
- B. Domain name server (DNS) poisoning
- C. Reverse Address Resolution Protocol
- D. Route table poisoning
Answer: B
NEW QUESTION 14
Which of the following firewalls inspects the actual contents of packets?
- A. Application-level firewall
- B. Stateful inspection firewall
- C. Packet filtering firewall
- D. Circuit-level firewall
Answer: A
NEW QUESTION 15
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
- A. Buffer-overflow attack
- B. Brute force attack
- C. Dictionary-based attack
- D. Password guessing
- E. Social engineering
- F. Zero-day attack
- G. Denial-of-service (DoS) attack
- H. Rainbow attack
Answer: BCDEH
NEW QUESTION 16
Which of the following tools performs comprehensive tests against web servers for multiple items, including over 6100 potentially dangerous files/CGIs?
- A. Dsniff
- B. Snort
- C. Nikto
- D. Sniffer
Answer: C
NEW QUESTION 17
Mark has been assigned a project to configure a wireless network for a company. The network should contain a Windows 2003 server and 30 Windows XP client computers. Mark has a single dedicated Internet connection that has to be shared among all the client computers and the server. The configuration needs to be done in a manner that the server should act as a proxy server for the client computers. Which of the following programs can Mark use to fulfill this requirement?
- A. Microsoft Internet Security & Acceleration Server (ISA)
- B. Wingate
- C. Sniffer
- D. SOCKS
Answer: B
NEW QUESTION 18
Which of the following commands will you use with the tcpdump command to capture the traffic from a filter stored in a file?
- A. tcpdump -A file_name
- B. tcpdump -D file_name
- C. tcpdump -X file_name
- D. tcpdump -F file_name
Answer: D
NEW QUESTION 19
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system and wants to install an Intrusion Detection System on the We-are-secure server so that he can receive alerts about any hacking attempts. Which of the following tools can John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- A. SARA
- B. Snort
- C. Samhain
- D. Tripwire
Answer: BC
NEW QUESTION 20
Which of the following tools is a wireless sniffer and analyzer that works on the Windows operating system?
- A. Aeropeek
- B. Void11
- C. Airsnort
- D. Kismet
Answer: A
NEW QUESTION 21
......
100% Valid and Newest Version GCIA Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/GCIA-exam-dumps.html (New 508 Q&As)
