We provide real GCIH exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GCIH Exam quickly & easily. The GCIH PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GCIH dumps pdf and vce product and material, you can easily pass the GCIH exam.
GIAC GCIH Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following attacking methods allows the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another computer by changing the Media Access Control address?
- A. IP address spoofing
- B. VLAN hoping
- C. ARP spoofing
- D. MAC spoofing
Answer: D
NEW QUESTION 2
Which of the following can be used as a Trojan vector to infect an information system?
Each correct answer represents a complete solution. Choose all that apply.
- A. NetBIOS remote installation
- B. Any fake executable
- C. Spywares and adware
- D. ActiveX controls, VBScript, and Java scripts
Answer: ABCD
NEW QUESTION 3
Which of the following provides packet-level encryption between hosts in a LAN?
- A. PPTP
- B. IPsec
- C. PFS
- D. Tunneling protocol
Answer: B
NEW QUESTION 4
Which of the following is an Internet mapping technique that relies on various BGP collectors that collect information such as routing updates and tables and provide this information publicly?
- A. AS Route Inference
- B. Path MTU discovery (PMTUD)
- C. AS PATH Inference
- D. Firewalking
Answer: C
NEW QUESTION 5
Which of the following are the primary goals of the incident handling team?
Each correct answer represents a complete solution. Choose all that apply.
- A. Freeze the scene.
- B. Repair any damage caused by an incident.
- C. Prevent any further damage.
- D. Inform higher authorities.
Answer: ABC
NEW QUESTION 6
Which of the following attacks is specially used for cracking a password?
- A. PING attack
- B. Dictionary attack
- C. Vulnerability attack
- D. DoS attack
Answer: B
NEW QUESTION 7
Which of the following steps of incident response is steady in nature?
- A. Containment
- B. Eradication
- C. Preparation
- D. Recovery
Answer: C
NEW QUESTION 8
Which of the following HTTP requests is the SQL injection attack?
- A. http://www.xsecurity.com/cgiin/bad.cgi?foo=..%fc%80%80%80%80%af../bin/ls%20-al
- B. http://www.victim.com/example?accountnumber=67891&creditamount=999999999
- C. http://www.myserver.com/search.asp?lname=adam%27%3bupdate%20usertable%20set% 20pass wd%3d %27hCx0r%27%3b--%00
- D. http://www.myserver.com/script.php?mydata=%3cscript%20src=%22http%3a%2f% 2fwww.yourser ver.c0m %2fbadscript.js%22%3e%3c%2fscript%3e
Answer: C
NEW QUESTION 9
You run the following PHP script:
<?php $name = mysql_real_escape_string($_POST["name"]);
$password = mysql_real_escape_string($_POST["password"]); ?>
What is the use of the mysql_real_escape_string() function in the above script.
Each correct answer represents a complete solution. Choose all that apply.
- A. It can be used to mitigate a cross site scripting attack.
- B. It can be used as a countermeasure against a SQL injection attack.
- C. It escapes all special characters from strings $_POST["name"] and $_POST["password"] except ' and ".
- D. It escapes all special characters from strings $_POST["name"] and $_POST["password"].
Answer: BD
NEW QUESTION 10
John works as a Professional Ethical Hacker for NetPerfect Inc. The company has a Linux-based network. All client computers are running on Red Hat 7.0 Linux. The Sales Manager of the company complains to John that his system contains an unknown package named as tar.gz and his documents are exploited. To resolve the problem, John uses a Port scanner to enquire about the open ports and finds out that the HTTP server service port on 27374 is open. He suspects that the other computers on the network are also facing the same problem. John discovers that a malicious application is using the synscan tool to randomly generate IP addresses.
Which of the following worms has attacked the computer?
- A. Code red
- B. Ramen
- C. LoveLetter
- D. Nimda
Answer: B
NEW QUESTION 11
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
Each correct answer represents a complete solution. Choose all that apply.
- A. The attacker must determine the right values for all the form inputs.
- B. The attacker must target a site that doesn't check the referrer header.
- C. The target site should have limited lifetime authentication cookies.
- D. The target site should authenticate in GET and POST parameters, not only cookies.
Answer: AB
NEW QUESTION 12
Which of the following tools can be used to detect the steganography?
- A. Dskprobe
- B. Blindside
- C. ImageHide
- D. Snow
Answer: A
NEW QUESTION 13
Which of the following statements are true regarding SYN flood attack?
- A. The attacker sends a succession of SYN requests to a target system.
- B. SYN flood is a form of Denial-of-Service (DoS) attack.
- C. The attacker sends thousands and thousands of ACK packets to the victim.
- D. SYN cookies provide protection against the SYN flood by eliminating the resources allocated on the target host.
Answer: ABD
NEW QUESTION 14
Choose and reorder the steps of an incident handling process in their correct order.
Solution:
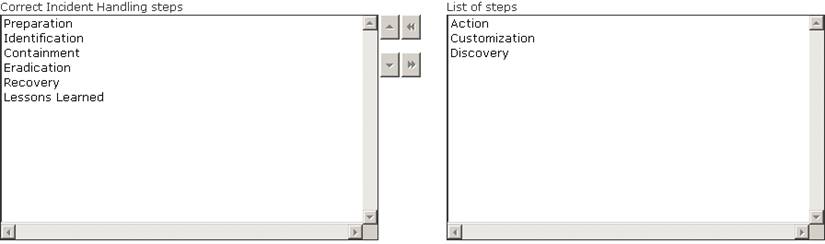
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
You enter the following URL on your Web browser:
http://www.we-are-secure.com/scripts/..%co%af../..%co%
af../windows/system32/cmd.exe?/c+dir+c:\
What kind of attack are you performing?
- A. Directory traversal
- B. Replay
- C. Session hijacking
- D. URL obfuscating
Answer: A
NEW QUESTION 16
You work as a Network Administrator for Net Perfect Inc. The company has a Windows-based network. The company wants to fix potential vulnerabilities existing on the tested systems. You use Nessus as a vulnerability scanning program to fix the vulnerabilities. Which of the following vulnerabilities can be fixed using Nessus?
Each correct answer represents a complete solution. Choose all that apply.
- A. Misconfiguration (e.
- B. open mail relay, missing patches, etc.)
- C. Vulnerabilities that allow a remote cracker to control sensitive data on a system
- D. Vulnerabilities that allow a remote cracker to access sensitive data on a system
- E. Vulnerabilities that help in Code injection attacks
Answer: ABC
NEW QUESTION 17
Which of the following malicious code can have more than one type of trigger, multiple task capabilities, and can replicate itself in more than one manner?
- A. Macro virus
- B. Blended threat
- C. Trojan
- D. Boot sector virus
Answer: B
NEW QUESTION 18
......
P.S. Surepassexam now are offering 100% pass ensure GCIH dumps! All GCIH exam questions have been updated with correct answers: https://www.surepassexam.com/GCIH-exam-dumps.html (328 New Questions)
