Act now and download your GIAC GSEC test today! Do not waste time for the worthless GIAC GSEC tutorials. Download Rebirth GIAC GIAC Security Essentials Certification exam with real questions and answers and begin to learn GIAC GSEC with a classic professional.
Also have GSEC free dumps questions for you:
NEW QUESTION 1
Which of the following is a required component for successful 802.lx network authentication?
- A. Supplicant
- B. 3rd-party Certificate Authority
- C. Ticket Granting Server (TGS)
- D. IPSec
Answer: A
NEW QUESTION 2
With regard to defense-in-depth, which of the following statements about network design principles is correct?
- A. A secure network design requires that systems that have access to the Internet should not be accessible from the Internet and that systems accessible from the Internet should not have access to the Interne
- B. A secure network design requires that networks utilize VLAN (Virtual LAN) implementations to insure that private and semi-public systems are unable to reach each other without going through a firewal
- C. A secure network design will seek to provide an effective administrative structure by providing a single choke-point for the network from which all security controls and restrictions will be enforce
- D. A secure network design will seek to separate resources by providing a security boundary between systems that have different network security requirement
Answer: D
NEW QUESTION 3
Which of the following protocols provides maintenance and error reporting function?
- A. UDP
- B. ICMP
- C. PPP
- D. IGMP
Answer: B
NEW QUESTION 4
Which of the following protocols is used by a host that knows its own MAC (Media Access Control) address to query a server for its own IP address?
- A. RARP
- B. ARP
- C. DNS
- D. RDNS
Answer: A
NEW QUESTION 5
When an IIS filename extension is mapped, what does this mean?
- A. Files with the mapped extensions cannot be interpreted by the web serve
- B. The file and all the data from the browser's request are handed off to the mapped interprete
- C. The files with the mapped extensions are interpreted by CMD.EX
- D. The files with the mapped extensions are interpreted by the web browse
Answer: B
NEW QUESTION 6
What type of attack can be performed against a wireless network using the tool Kismet?
- A. IP spoofing
- B. Eavesdropping
- C. Masquerading
- D. Denial of Service
Answer: B
NEW QUESTION 7
A US case involving malicious code is brought to trial. An employee had opened a helpdesk ticket to report specific instances of strange behavior on her system. The IT helpdesk representative collected information by interviewing the user and escalated the ticket to the system administrators. As the user had regulated and sensitive data on her computer, the system administrators had the hard drive sent to the company's forensic consultant for analysis and configured a new hard drive for the user. Based on the recommendations from the forensic consultant and the company's legal department, the CEO decided to prosecute the author of the malicious code. During the court case, which of the following would be able to provide direct evidence?
- A. The IT helpdesk representative
- B. The company CEO
- C. The user of the infected system
- D. The system administrator who removed the hard drive
Answer: C
NEW QUESTION 8
Included below is the output from a resource kit utility run against local host.
Which command could have produced this output? 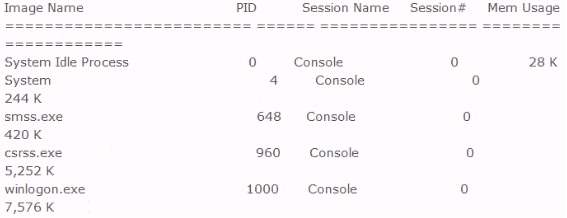
- A. Schtasks
- B. Task kill
- C. SC
- D. Task list
Answer: D
NEW QUESTION 9
Which of the following is a Layer 3 device that will typically drop directed broadcast traffic?
- A. Hubs
- B. Bridges
- C. Routers
- D. Switches
Answer: C
NEW QUESTION 10
Which of the following TCP packet flags indicates that host should IMMEDIATELY terminate the connection containing the packet?
- A. FIN
- B. URG
- C. SYN
- D. RST
Answer: D
NEW QUESTION 11
Users at the Marketing department are receiving their new Windows XP Professional workstations. They will need to maintain local work files in the first logical volume, and will use a second volume for the information shared between the area group. Which is the best file system design for these workstations?
- A. Both volumes should be converted to NTFS at install tim
- B. First volume should be FAT32 and second volume should be NTF
- C. First volume should be EFS and second volume should be FAT32.
- D. Both volumes should be converted to FAT32 with NTFS DACL
Answer: A
NEW QUESTION 12
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
- A. Physical
- B. Administrative
- C. Automatic
- D. Technical
Answer: ABD
NEW QUESTION 13
Which of the below choices should an organization start with when implementing an effective risk management process?
- A. Implement an incident response plan
- B. Define security policy requirements
- C. Conduct periodic reviews
- D. Design controls and develop standards for each technology you plan to deploy
Answer: B
NEW QUESTION 14
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. You want to mount an SMBFS share from a Linux workstation. Which of the following commands can you use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
- A. smbmount
- B. mount smb
- C. smbfsmount
- D. mount -t smbfs
Answer: AD
NEW QUESTION 15
Which of the following heights of fence deters only casual trespassers?
- A. 8 feet
- B. 2 to 2.5 feet
- C. 6 to 7 feet
- D. 3 to 4 feet
Answer: D
NEW QUESTION 16
SSL session keys are available in which of the following lengths?
- A. 40-bit and 128-bi
- B. 64-bit and 128-bi
- C. 128-bit and 1,024-bi
- D. 40-bit and 64-bi
Answer: A
NEW QUESTION 17
In addition to securing the operating system of production honey pot hosts, what is recommended to prevent the honey pots from assuming the identities of production systems that could result in the denial of service for legitimate users?
- A. Deploy the honey pot hosts as physically close as possible to production system
- B. Deploy the honey pot hosts in an unused part of your address spac
- C. Deploy the honey pot hosts to only respond to attack
- D. Deploy the honey pot hosts on used address spac
Answer: B
NEW QUESTION 18
Which of the following statements would be seen in a Disaster Recovery Plan?
- A. "Instructions for notification of the media can be found in Appendix A"
- B. "The Emergency Response Plan should be executed in the case of any physical disaster listed on page 3."
- C. "The target for restoration of business operations is 72 hours from the declaration of disaster."
- D. "After arriving at the alternate site, utilize the server build checklist to rebuild all servers on the server rebuild list."
Answer: D
NEW QUESTION 19
What is the name of the command-line tool for Windows that can be used to manage audit policies on remote systems?
- A. SECEDTT.EXE
- B. POLCLI.EXE
- C. REMOTEAUDIT.EXE
- D. AUDITPOL.EXE
Answer: D
NEW QUESTION 20
What is the process of simultaneously installing an operating system and a Service Pack called?
- A. Synchronous Update
- B. Slipstreaming
- C. Simultaneous Update
- D. Synchronizing
Answer: B
NEW QUESTION 21
......
P.S. 2passeasy now are offering 100% pass ensure GSEC dumps! All GSEC exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/GSEC/ (279 New Questions)
