We provide real GSEC exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GSEC Exam quickly & easily. The GSEC PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GSEC dumps pdf and vce product and material, you can easily pass the GSEC exam.
Free demo questions for GIAC GSEC Exam Dumps Below:
NEW QUESTION 1
What is the motivation behind SYN/FIN scanning?
- A. The SYN/FIN combination is useful for signaling to certain Trojan
- B. SYN/FIN packets are commonly used to launch denial of service attacks against BSD host
- C. The crafted SYN/FIN packet sometimes gets past firewalls and filtering router
- D. A SYN/FIN packet is used in session hijacking to take over a sessio
Answer: B
NEW QUESTION 2
What protocol is a WAN technology?
- A. 802.11
- B. 802.3
- C. Ethernet
- D. Frame Relay
Answer: D
NEW QUESTION 3
Which of the following SIP INVITE lines indicates to the remote registrar the VoIP phone that initiated the call?
- A. Via
- B. To
- C. From-Agent
- D. User-Agent
Answer: D
NEW QUESTION 4
Where is the source address located in an IPv4 header?
- A. At an offset of 20 bytes
- B. At an offset of 8 bytes
- C. At an offset of 16 bytes
- D. At an offset of 12 bytes
Answer: D
NEW QUESTION 5
If you do NOT have an original file to compare to, what is a good way to identify steganography in potential carrier files?
- A. Determine normal properties through methods like statistics and look for changes
- B. Determine normal network traffic patterns and look for changes
- C. Find files with the extension .stg
- D. Visually verify the files you suspect to be steganography messages
Answer: A
NEW QUESTION 6
Your organization is developing a network protection plan. No single aspect of your network seems more important than any other. You decide to avoid separating your network into segments or categorizing the systems on the network. Each device on the network is essentially protected in the same manner as all other devices.
This style of defense-in-depth protection is best described as which of the following?
- A. Uniform protection
- B. Threat-oriented
- C. Information-centric
- D. Protected enclaves
Answer: A
NEW QUESTION 7
What is the maximum passphrase length in Windows 2000/XP/2003?
- A. 255 characters
- B. 127 characters
- C. 95 characters
- D. 63 characters
Answer: B
NEW QUESTION 8
What is SSL primarily used to protect you against?
- A. Session modification
- B. SQL injection
- C. Third-patty sniffing
- D. Cross site scripting
Answer: C
NEW QUESTION 9
You work as a Network Administrator for World Perfect Inc. The company has a Linux-based network. You have configured a Linux Web server on the network. A user complains that the Web server is not responding to requests. The process list on the server shows multiple instances of the HTTPD process. You are required to stop the Web service. Which of the following commands will you use to resolve the issue?
- A. killall httpd
- B. endall httpd
- C. kill httpd
- D. end httpd
Answer: A
NEW QUESTION 10
Which of the following systems acts as a NAT device when utilizing VMware in NAT mode?
- A. Guest system
- B. Local gateway
- C. Host system
- D. Virtual system
Answer: D
NEW QUESTION 11
Which of the following defines the communication link between a Web server and Web
applications?
- A. CGI
- B. PGP
- C. Firewall
- D. IETF
Answer: A
NEW QUESTION 12
The previous system administrator at your company used to rely heavily on email lists, such as vendor lists and Bug Traq to get information about updates and patches. While a useful means of acquiring data, this requires time and effort to read through. In an effort to speed things up, you decide to switch to completely automated updates and patching. You set up your systems to automatically patch your production servers using a cron job and a scripted apt-get upgrade command. Of the following reasons, which explains why you may want to avoid this plan?
- A. The apt-get upgrade command doesn't work with the cron command because of incompatibility
- B. Relying on vendor and 3rd party email lists enables updates via email, for even faster patching
- C. Automated patching of production servers without prior testing may result in unexpected behavior or failures
- D. The command apt-get upgrade is incorrect, you need to run the apt-get update command
Answer: D
NEW QUESTION 13
Which of the following is an Implementation of PKI?
- A. SSL
- B. 3DES
- C. Kerberos
- D. SHA-1
Answer: A
NEW QUESTION 14
Which Host-based IDS (HIDS) method of log monitoring utilizes a list of keywords or phrases that define the events of interest for the analyst, then takes a list of keywords to watch for and generates alerts when it sees matches in log file activity?
- A. Passive analysis
- B. Retroactive analysis
- C. Exclusive analysis
- D. Inclusive analysis
Answer: D
NEW QUESTION 15
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. For testing purposes, you have configured a default IP-table with several filtering rules. You want to reconfigure the table. For this, you decide to remove the rules from all the chains in the table. Which of the following commands will you use?
- A. IPTABLES -D
- B. IPTABLES -A
- C. IPTABLES -h
- D. IPTABLES -F
Answer: D
NEW QUESTION 16
If a DNS client wants to look up the IP address for good.news.com and does not receive an authoritative reply from its local DNS server, which name server is most likely to provide an authoritative reply?
- A. The news.com domain name server
- B. The .com (top-level) domain name server
- C. The .(root-level) domain name server
- D. The .gov (top-level) domain name server
Answer: A
NEW QUESTION 17
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back: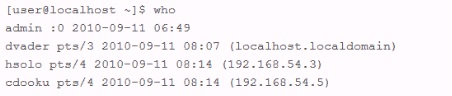
- A. The contents of the /var/log/messages file has been altered
- B. The contents of the bash history file has been altered
- C. The contents of the utmp file has been altered
- D. The contents of the http logs have been altered
Answer: B
NEW QUESTION 18
Which of the following are advantages of Network Intrusion Detection Systems (NIDS)?
- A. Analysis of encrypted traffic
- B. Provide insight into network traffic
- C. Detection of network operations problems
- D. Provide logs of network traffic that can be used as part of other security measure
- E. Inexpensive to manage
- F. B, C, and D
- G. A, C, and E
- H. B, D, and E
- I. A, B, and C
Answer: C
NEW QUESTION 19
The Windows 'tracert' begins by sending what type of packet to the destination host?
- A. A UDP packet with a TTL of 1
- B. An ICMP Echo Request
- C. An ICMP Router Discovery
- D. An ICMP Echo Reply
Answer: A
NEW QUESTION 20
Which of the following languages enable programmers to store cookies on client computers? Each correct answer represents a complete solution. Choose two.
- A. DHTML
- B. Perl
- C. HTML
- D. JavaScript
Answer: BD
NEW QUESTION 21
......
P.S. Thedumpscentre.com now are offering 100% pass ensure GSEC dumps! All GSEC exam questions have been updated with correct answers: https://www.thedumpscentre.com/GSEC-dumps/ (279 New Questions)
