Exam Code: GSEC (Practice Exam Latest Test Questions VCE PDF)
Exam Name: GIAC Security Essentials Certification
Certification Provider: GIAC
Free Today! Guaranteed Training- Pass GSEC Exam.
Online GIAC GSEC free dumps demo Below:
NEW QUESTION 1
You are going to upgrade your hard disk's file system from FAT to NTFS. What are the major advantages of the NTFS file system over FAT16 and FAT32 file systems?
Each correct answer represents a complete solution. Choose all that apply.
- A. NTFS gives better file security than FAT16 and FAT32.
- B. Automatic backu
- C. NTFS file system supports for larger hard disk
- D. NTFS give improved disk compression than FAT16 and FAT32.
Answer: ACD
NEW QUESTION 2
During a scheduled evacuation training session the following events took place in this order:
* 1. Evacuation process began by triggering the building fire alarm.
* 2a. The meeting point leader arrived first at the designated meeting point and immediately began making note of who was and was not accounted for.
* 2b. Stairwell and door monitors made it to their designated position to leave behind a box of flashlights and prop the stairway doors open with a garbage can so employees can find exits and dispose of food and beverages.
2c. Special needs assistants performed their assigned responsibility to help employees out that require special assistance.
* 3. The safety warden communicated with the meeting point leader via walkie talkie to collect a list of missing personnel and communicated this information back to the searchers.
* 4. Searchers began checking each room and placing stick-it notes on the bottom of searched doors to designate which areas were cleared.
* 5. All special need assistants and their designated wards exited the building.
* 6. Searchers complete their assigned search pattern and exit with the Stairwell/door monitors.
Given this sequence of events, which role is in violation of its expected evacuation tasks?
- A. Safety warden
- B. Stairwell and door monitors
- C. Meeting point leader
- D. Searchers
- E. Special needs assistants
Answer: B
NEW QUESTION 3
In preparation to do a vulnerability scan against your company's systems. You've taken the steps below:
You've notified users that there will be a system test.
You've priontized and selected your targets and subnets.
You've configured the system to do a deep scan.
You have a member of your team on call to answer questions.
Which of the following is a necessary step to take prior to starting the scan?
- A. Placing the incident response team on cal
- B. Clear relevant system log file
- C. Getting permission to run the sca
- D. Scheduling the scan to run before OS update
Answer: C
NEW QUESTION 4
Many IIS servers connect to Microsoft SQL databases. Which of the following statements about SQL server security is TRUE?
- A. SQL Server patches are part of the operating system patche
- B. SQL Server should be installed on the same box as your IIS web server when they communicate as part of the web applicatio
- C. It is good practice to never use integrated Windows authentication for SQL Serve
- D. It is good practice to not allow users to send raw SQL commands to the SQL Serve
Answer: D
NEW QUESTION 5
Which of the following BEST describes the two job functions of Microsoft Baseline Security Analyzer (MBSA)?
- A. Vulnerability scanner and auditing tool
- B. Auditing tool and alerting system
- C. Configuration management and alerting system
- D. Security patching and vulnerability scanner
Answer: D
NEW QUESTION 6
In a /24 subnet, which of the following is a valid broadcast address?
- A. 200.11.11.1
- B. 221.10.10.10
- C. 245.20.30.254
- D. 192.10.10.255
Answer: D
NEW QUESTION 7
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?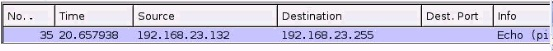
- A. Block DNS traffic across the router
- B. Disable forwarding of unsolicited TCP requests
- C. Disable IP-directed broadcast requests
- D. Block UDP packets at the firewall
Answer: C
NEW QUESTION 8
You are responsible for technical support at a company. One of the employees complains that his new laptop cannot connect to the company wireless network. You have verified that he is entering a valid password/passkey. What is the most likely problem?
- A. A firewall is blocking hi
- B. His laptop is incompatibl
- C. MAC filtering is blocking hi
- D. His operating system is incompatibl
Answer: C
NEW QUESTION 9
Validating which vulnerabilities in a network environment are able to be exploited by an attacker is called what?
- A. Anomaly detection
- B. Vulnerability scanning
- C. Perimeter assessment
- D. Penetration testing
Answer: B
NEW QUESTION 10
You have implemented a firewall on the company's network for blocking unauthorized network connections. Which of the following types of security control is implemented in this case?
- A. Detective
- B. Preventive
- C. Directive
- D. Corrective
Answer: B
NEW QUESTION 11
Which of the following statements about Secure Sockets Layer (SSL) are true? Each correct answer represents a complete solution. Choose two.
- A. It provides communication privacy, authentication, and message integrit
- B. It provides mail transfer servic
- C. It uses a combination of public key and symmetric encryption for security of dat
- D. It provides connectivity between Web browser and Web serve
Answer: AC
NEW QUESTION 12
Which of the following features of Windows 7 allows an administrator to both passively review installed software and configure policies to prevent out-of-date or insecure software from running?
- A. Direct Access
- B. Software Restriction Policies
- C. App Locker
- D. User Account Control
Answer: C
NEW QUESTION 13
What are the two actions the receiver of a PGP email message can perform that allows establishment of trust between sender and receiver?
- A. Decode the message by decrypting the asymmetric key with his private key, then using the asymmetric key to decrypt the messag
- B. Decode the message by decrypting the symmetric key with his private key, then using the symmetric key to decrypt the messag
- C. Decode the message by decrypting the symmetric key with his public key, then using the symmetric key to decrypt the messag
- D. Decrypt the message by encrypting the digital signature with his private key, then using the digital signature to decrypt the messag
Answer: A
NEW QUESTION 14
At what point in the Incident Handling process should an organization determine its approach to notifying law enforcement?
- A. When performing analysis
- B. When preparing policy
- C. When recovering from the incident
- D. When reacting to an incident
Answer: D
NEW QUESTION 15
Which of the following applications cannot proactively detect anomalies related to a computer?
- A. Firewall installed on the computer
- B. NIDS
- C. HIDS
- D. Anti-virus scanner
Answer: B
NEW QUESTION 16
What defensive measure could have been taken that would have protected the confidentiality of files that were divulged by systems that were compromised by malware?
- A. Ingress filtering at the host level
- B. Monitoring for abnormal traffic flow
- C. Installing file integrity monitoring software
- D. Encrypting the files locally when not in use
Answer: D
NEW QUESTION 17
Which of the following statements about Network Address Translation (NAT) are true? Each correct answer represents a complete solution. Choose two.
- A. It reduces the need for globally unique IP addresse
- B. It allows external network clients access to internal service
- C. It allows the computers in a private network to share a global, ISP assigned address to connect to the Interne
- D. It provides added security by using Internet access to deny or permit certain traffic from the Bastion Hos
Answer: AC
NEW QUESTION 18
Which of the following Linux commands can change both the username and group name a file belongs to?
- A. chown
- B. chgrp
- C. chmod
- D. newgrp
Answer: B
NEW QUESTION 19
You work as a Network Administrator for McNeil Inc. The company has a Linux-based network. David, a Sales Manager, wants to know the name of the shell that he is currently using. Which of the following commands will he use to accomplish the task?
- A. mv $shell
- B. echo $shell
- C. rm $shell
- D. ls $shell
Answer: B
NEW QUESTION 20
What technical control provides the most critical layer of defense if an intruder is able to bypass all physical security controls and obtain tapes containing critical data?
- A. Camera Recordings
- B. Security guards
- C. Encryption
- D. Shredding
- E. Corrective Controls
Answer: C
NEW QUESTION 21
......
Recommend!! Get the Full GSEC dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/GSEC-dumps/ (New 279 Q&As Version)
