Master the GSNA GIAC Systems and Network Auditor content and be ready for exam day success quickly with this Certleader GSNA free exam. We guarantee it!We make it a reality and give you real GSNA questions in our GIAC GSNA braindumps.Latest 100% VALID GIAC GSNA Exam Questions Dumps at below page. You can use our GIAC GSNA braindumps and pass your exam.
Also have GSNA free dumps questions for you:
NEW QUESTION 1
John works as a Security Professional. He is assigned a project to test the security of www.we-are-secure.com. John wants to get the information of all network connections and listening ports in the numerical form. Which of the following commands will he use?
- A. netstat -e
- B. netstat –r
- C. netstat -s
- D. netstat –an
Answer: D
Explanation:
According to the scenario, John will use the netstat -an command to accomplish the task. The netstat -an command is used to get the information of all network connections and listening ports in the numerical form. The netstat command displays
protocol-related statistics and the state of current TCP/IP connections. It is used to get information about the open connections on a computer, incoming and outgoing data, as well as the ports of remote computers to which the computer is connected. The netstat command gets all this networking information by reading the kernel routing tables in the memory. Answer A is incorrect. The netstat -e command displays the Ethernet information. Answer B is incorrect. The netstat -r command displays the routing table information. Answer C is incorrect. The netstat -s command displays per-protocol statistics. By default, statistics are shown for TCP, UDP and IP.
NEW QUESTION 2
What will happen if you write the following parameters in the web.xml file?
<session-config>
<session-timeout>0</session-timeout>
</session-config>
- A. There will be no effect on the session; it will last for its default time.
- B. The session will never expire.
- C. An error will occur during execution.
- D. The session will expire immediately.
Answer: B
Explanation:
The <session-timeout> element of the deployment descriptor sets the session timeout. If the time specified for timeout is zero or negative, the session will never timeout.
NEW QUESTION 3
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below: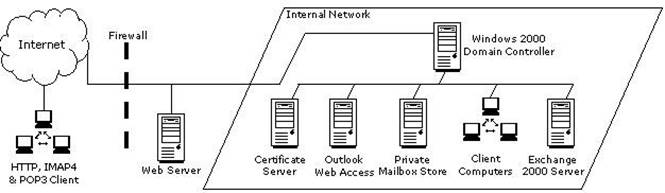
Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
- A. Install one front-end Exchange 2000 server and continue to run Microsoft Outlook Web Access on the existing serve
- B. Place the new server on the perimeter networ
- C. Configure unique URLs for each serve
- D. Configure Certificate Service
- E. Create a rule on the firewall to direct port 443 to the servers.
- F. Install two front-end Exchange 2000 server
- G. Place the new servers on the internal network and configure load balancing between the
- H. Configure Certificate Service
- I. Create a rule on the firewall to redirect port 443 to the servers.
- J. Install two front-end Exchange 2000 server
- K. Place the new servers on the perimeter network and configure load balancing between the
- L. Configure Certificate Service
- M. Create a rule on the firewall to redirect port 443 to the servers.
- N. Install two Exchange 2000 server
- O. Place the new servers on the perimeter networ
- P. Configure unique URLs for each serve
- Q. Configure Certificate Service
- R. Create a rule on the firewall to direct port 443 to the servers.
Answer: C
Explanation:
To ensure fault tolerance among the servers and to get the highest possible level of security and encryption for OWA clients, you must install two front-end Exchange 2000 servers. Place the new servers on the perimeter network and configure load balancing between them. To enhance security, you should also configure Certificate Services and create a rule on the firewall to redirect port 443 to the servers. The most secure firewall configuration is placing a firewall on either side of the front-end servers. This isolates the front-end servers in a perimeter network, commonly referred to as a demilitarized zone (DMZ). It is always better to configure more than one front-end server to get fault tolerance.
NEW QUESTION 4
Which of the following methods can be helpful to eliminate social engineering threat? (Choose three)
- A. Data encryption
- B. Data classification
- C. Password policies
- D. Vulnerability assessments
Answer: BCD
Explanation:
The following methods can be helpful to eliminate social engineering threat: Password policies Vulnerability assessments Data classification Password policy should specify that how the password can be shared. Company should implement periodic penetration and vulnerability assessments. These assessments usually consist of using known hacker tools and common hacker techniques to breach a network security. Social engineering should also be used for an accurate assessment. Since social engineers use the knowledge of others to attain information, it is essential to have a data classification model in place that all employees know and follow. Data classification assigns level of sensitivity of company information. Each classification level specifies that who can view and edit data, and how it can be shared.
NEW QUESTION 5
Adam works on a Linux system. He is using Sendmail as the primary application to transmit e-mails. Linux uses Syslog to maintain logs of what has occurred on the system. Which of the following log files contains e-mail information such as source and destination IP addresses, date and time stamps etc?
- A. /var/log/mailog
- B. /var/log/logmail
- C. /log/var/mailog
- D. /log/var/logd
Answer: A
Explanation:
/var/log/mailog ?le generally contains the source and destination IP addresses, date and time stamps, and other information that may be used to check the information contained within an e-mail header. Linux uses Syslog to maintain logs of what has occurred on the system. The configuration file /etc/syslog.conf is used to determine where the Syslog service (Syslogd) sends its logs. Sendmail can create event messages and is usually configured to record the basic information such as the source and destination addresses, the sender and recipient addresses, and the message ID of e-mail. The syslog.conf will display the location of the log file for e-mail. Answer B, C, D are incorrect. All these files are not valid log files.
NEW QUESTION 6
In a network, a data packet is received by a router for transmitting it to another network. For forwarding the packet to the other available networks, the router is configured with a static or a dynamic route. What are the benefits of using a static route?
- A. It is a fault tolerant path.
- B. It reduces load on routers, as no complex routing calculations are required.
- C. It reduces bandwidth usage, as there is no excessive router traffic.
- D. It provides precise control over the routes that packets will take across the network.
Answer: BCD
Explanation:
Static routing is a data communication concept that describes a way to configure path selection of routers in computer networks. This is achieved by manually adding routes to the routing table. However, when there is a change in the network or a failure occurs between two statically defined nodes, traffic will not be rerouted. Static routing is beneficial in many ways: Precise control over the routes that a packet will take across the network Reduced load on the routers, as no complex routing calculations are required Reduced bandwidth use, as there is no excessive router traffic. Easy to configure in small networks Answer A is incorrect. This is a property of a dynamic route. A static route cannot choose the best path. It can only choose the paths that are manually entered.
When there is a change in the network or a failure occurs between two statically defined nodes, traffic will not be rerouted.
NEW QUESTION 7
You work as a Network Administrator for Tech Perfect Inc. For security issues, the company requires you to harden its routers. You therefore write the following code: Router#config terminal Router(config) #no ip bootp server Router(config) #no ip name- server Router(config) #no ntp server Router(config) #no snmp server Router(config) #no ip http server Router(config) #^Z Router# What services will be disabled by using this configuration fragment?
- A. BootP service
- B. Finger
- C. CDP
- D. DNS function
Answer: AD
Explanation:
The above configuration fragment will disable the following services from the router: The BootP service The DNS function The Network Time Protocol The Simple Network Management Protocol Hyper Text Transfer Protocol
NEW QUESTION 8
Mark works as a Web Developer for XYZ CORP. He is developing a Web site for the company. He wants to use frames in the Web site. Which of the following is an HTML tag used to create frames?
- A. <REGION>
- B. <TABLESET>
- C. <FRAMEWINDOW>
- D. <FRAMESET>
Answer: D
Explanation:
<FRAMESET> tag specifies a frameset used to organize multiple frames and nested framesets in an HTML document. It defines the location, size, and orientation of frames. An HTML document can either contain a <FRAMESET> tag or a <BODY> tag. Answer A, B, C are incorrect. There are no HTML tags such as <TABLESET>,
<FRAMEWINDOW>, and <REGION>.
NEW QUESTION 9
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
- A. Change hub with switch.
- B. Deploying a powerful antenna.
- C. Disabling SSID broadcast.
- D. Implement WEP.
Answer: C
Explanation:
Disabling SSID broadcast will free up bandwidth in a WLAN environment. It is used to enhance security of a Wireless LAN (WLAN). It makes difficult for attackers to find the access point (AP). It is also used by enterprises to prevent curious people from trying to access the WLAN.
NEW QUESTION 10
You are responsible for a large network that has its own DNS servers. You periodically check the log to see if there are any problems. Which of the following are likely errors you might encounter in the log? (Choose three)
- A. The DNS server could not create FTP socket for address [IP address of server]
- B. The DNS server could not create an SMTP socket
- C. Active Directory Errors
- D. The DNS server could not create a Transmission Control Protocol (TCP) socket
- E. The DNS server could not initialize the Remote Procedure Call (RPC) service
Answer: CDE
Explanation:
There are a number of errors one could find in a Windows Server 2003 DNS log. They are as follows: The DNS server could not create a Transmission Control Protocol. The DNS server could not open socket for address. The DNS server could not initialize the Remote Procedure Call (RPC) service. The DNS server could not bind the main datagram socket. The DNS Server service relies on Active Directory to store and retrieve information for Active Directory-integrated zones. And several active directory errors are possible. Answer B is incorrect. DNS Servers do not create FTP connections. Answer A is incorrect. DNS Servers do not create SMTP connections.
NEW QUESTION 11
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to do RARP mapping from hardware mapping addresses to IP addresses. Which of the following Unix configuration files can you use to accomplish the task?
- A. /etc/dhcpd.conf
- B. /etc/motd
- C. /etc/exports
- D. /etc/ethers
Answer: D
Explanation:
In Unix, the /etc/ethers file is used by system administrators for RARP mapping from hardware mapping addresses to IP addresses.
Answer A is incorrect. In Unix, the /etc/dhcpd.conf file is the configuration file for the DHCP server daemon. Answer C is incorrect. In Unix, the /etc/exports file describes exported file systems for NFS services. Answer B is incorrect. In Unix, the /etc/motd file automatically displays the message of the day after a successful login.
NEW QUESTION 12
Which of the following statements about the traceroute utility are true?
- A. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host.
- B. It records the time taken for a round trip for each packet at each router.
- C. It is an online tool that performs polymorphic shell code attacks.
- D. It generates a buffer overflow exploit by transforming an attack shell code so that the new attack shell code cannot be recognized by any Intrusion Detection Systems.
Answer: AB
Explanation:
Traceroute is a route-tracing utility that displays the path an IP packet takes to reach its destination. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host. This tool also records the time taken for a round trip for each packet at each router that can be used to find any faulty router along the path. Answer C, D are incorrect. Traceroute does not perform polymorphic shell code attacks. Attacking tools such as ADMutate areused to perform polymorphic shell code attacks.
NEW QUESTION 13
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. In which of the following forms can eBox Platform be used?
- A. Unified Communications Server
- B. Network Infrastructure Manager
- C. Gateway
- D. Sandbox
Answer: ABC
Explanation:
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. eBox Platform can act as a Gateway, Network Infrastructure Manager, Unified Threat Manager, Office Server, Unified Communications Server or a combination of them. Besides, eBox Platform includes a development framework to ease the development of new Unix-based services. Answer D is incorrect. eBox Platform cannot act as a sandbox. A sandbox is a security mechanism for separating running programs. It is often used to execute untested code, or untrusted programs, from unverified third-parties, suppliers, and untrusted users.
NEW QUESTION 14
Which of the following is the most secure place to host a server that will be accessed publicly through the Internet?
- A. A DNS Zone
- B. An Intranet
- C. A stub zone
- D. A demilitarized zone (DMZ)
Answer: D
Explanation:
A demilitarized zone (DMZ) is the most secure place to host a server that will be accessed publicly through the Internet. Demilitarized zone (DMZ) or perimeter network is a small network that lies in between the Internet and a private network. It is the boundary between the Internet and an internal network, usually a combination of firewalls and bastion hosts that are gateways between inside networks and outside networks. DMZ provides a large enterprise network or corporate network the ability to use the Internet while still maintaining its security. Answer B is incorrect. Hosting a server on the intranet for public access will not be good from a security point of view.
NEW QUESTION 15
You work as a Network Analyst for XYZ CORP. The company has a Unix-based network. You want to view the directories in alphabetical order. Which of the following Unix commands will you use to accomplish the task?
- A. cat
- B. chmod
- C. cp
- D. ls
Answer: D
Explanation:
In Unix, the ls command is used to view the directories in alphabetical order. Answer A is incorrect. In Unix, the cat command in Unix is used to create or display short files. Answer B is incorrect. In Unix, the chmod command is used to change permissions. Answer C is incorrect. In Unix, the cp command is used for copying files.
NEW QUESTION 16
Which of the following wireless security features provides the best wireless security mechanism?
- A. WEP
- B. WPA with 802.1X authentication
- C. WPA
- D. WPA with Pre Shared Key
Answer: B
Explanation:
WPA with 802.1X authentication provides best wireless security mechanism. 802.1X authentication, also known as WPA-Enterprise, is a security mechanism for wireless networks. 802.1X provides port-based authentication, which involves communications between a supplicant, authenticator, and authentication server. The supplicant is often software on a client device, the authenticator is a wired Ethernet switch or wireless access point, and an authentication server is generally a RADIUS database. The authenticator acts like a security guard to a protected network. The supplicant (client device) is not allowed access through the authenticator to the protected side of the network until the supplicant's identity is authorized. With 802.1X port-based authentication, the supplicant provides credentials, such as user name/password or digital certificate, to the authenticator, and the authenticator forwards the credentials to the authentication server for verification. If the credentials are valid, the supplicant (client device) is allowed to access resources located on the protected side of the network.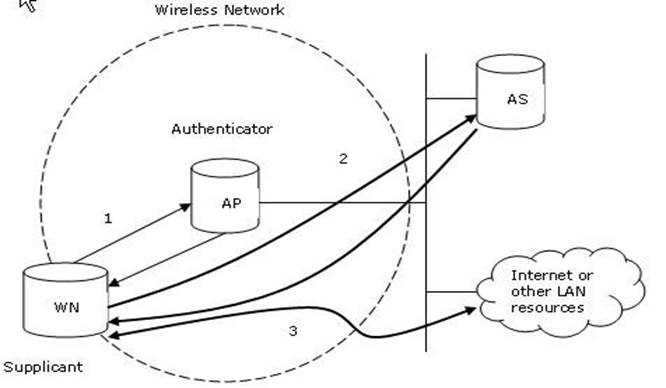
Answer A is incorrect. Wired equivalent privacy (WEP) uses the stream cipher RC4 (Rivest Cipher). WEP uses the Shared Key Authentication, since both the access point and the wireless device possess the same key. Attacker with enough Initialization Vectors can crack the key used and gain full access to the network. Answer D is incorrect. WPA-PSK is a strong encryption where encryption keys are automatically changed (called rekeying) and authenticated between devices after a fixed period of time, or after a fixed number of packets has been transmitted. Answer C is incorrect. WAP uses TKIP (Temporal Key Integrity Protocol) to enhance data encryption, but still vulnerable to different password
cracking attacks.
NEW QUESTION 17
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
- A. 24171811
- B. 24619311
- C. 24171111
- D. 24171311
Answer: B
Explanation:
You took 3 seconds to establish a connection. During this time, the value of the Initial Sequence Number would become [24171311 + (1 * 64000) + (3 * 128000)], i.e., 24619311.
NEW QUESTION 18
An executive in your company reports odd behavior on her PDA. After investigation you discover that a trusted device is actually copying data off the PDA. The executive tells you that the behavior started shortly after accepting an e-business card from an unknown person. What type of attack is this?
- A. Session Hijacking
- B. Bluesnarfing
- C. Privilege Escalation
- D. PDA Hijacking
Answer: B
Explanation:
Bluesnarfing is a rare attack in which an attacker takes control of a bluetooth enabled device. One way to do this is to get your PDA to accept the attacker's device as a trusted device.
NEW QUESTION 19
......
P.S. Easily pass GSNA Exam with 368 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy GSNA Dumps: https://www.2passeasy.com/dumps/GSNA/ (368 New Questions)
