We provide real GSNA exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GSNA Exam quickly & easily. The GSNA PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GSNA dumps pdf and vce product and material, you can easily pass the GSNA exam.
Online GIAC GSNA free dumps demo Below:
NEW QUESTION 1
Which of the following attacks allows the bypassing of access control lists on servers or routers, and helps an attacker to hide? (Choose two)
- A. DNS cache poisoning
- B. DDoS attack
- C. IP spoofing attack
- D. MAC spoofing
Answer: CD
Explanation:
Either IP spoofing or MAC spoofing attacks can be performed to hide the identity in the network. MAC spoofing is a hacking technique of changing an assigned Media Access Control (MAC) address of a networked device to a different one. The changing of the assigned MAC address may allow the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another computer. MAC spoofing is the activity of altering the MAC address of a network card. Answer A is incorrect. DNS cache poisoning is a maliciously created or unintended situation that provides data to a caching name server that did not originate from authoritative Domain Name System (DNS) sources. Once a DNS server has received such non-authentic datA, Caches it for future performance increase, it is considered poisoned, supplying the non-authentic data to the clients of the server. To perform a cache poisoning attack, the attacker exploits a flaw in the DNS software. If the server does not correctly validate DNS responses to ensure that they are from an authoritative source, the server will end up caching the incorrect entries locally and serve them to other users that make the same request. Answer B is incorrect. In a distributed denial of service (DDOS) attack, an attacker uses multiple computers throughout the network that has been previously infected. Such computers act as zombies and work together to send out bogus messages, thereby increasing the amount of phony traffic. The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. TFN, TRIN00, etc. are tools used for a DDoS attack.
NEW QUESTION 2
In which of the following techniques does an attacker take network traffic coming towards a host at one port and forward it from that host to another host?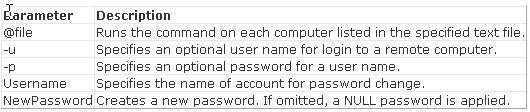
- A. Snooping
- B. UDP port scanning
- C. Firewalking
- D. Port redirection
Answer: D
Explanation:
Port redirection is a technique by which an attacker takes network traffic coming towards a host at one port and redirects it from that host to another host. For example, tools such as Fpipe and Datapipe are port redirection tools that accept connections at any specified port and resend them to other specified ports on specified hosts. For example, the following command establishes a listener on port 25 on the test system and then redirects the connection to port 80 on the target system using the source port of 25. C.\>fpipe -l 25 -s 25 -r 80 IP_address Answer C is incorrect. Firewalking is a technique for gathering information about a remote network protected by a firewall. This technique can be used effectively to perform information gathering attacks. In this technique, an attacker sends a crafted packet with a TTL value that is set to expire one hop past the firewall. If the firewall allows this crafted packet through, it forwards the packet to the next hop. On the next hop, the packet expires and elicits an ICMP "TTL expired in transit" message to the attacker. If the firewall does not allow the traffic, there should be no response, or an ICMP "administratively prohibited" message should be returned to the attacker. A malicious attacker can use firewalking to determine the types of ports/protocols that can bypass the firewall. To use firewalking, the attacker needs the IP address of the last known gateway before the firewall and the IP address of a host located behind the firewall. The main drawback of this technique is that if an administrator blocks ICMP packets from leaving the network, it is ineffective. Answer A is incorrect. Snooping is an activity of observing the content that appears on a computer monitor or watching what a user is typing. Snooping also occurs by using software programs to remotely monitor activity on a computer or network device. Hackers or attackers use snooping techniques and equipment such as keyloggers to monitor keystrokes, capture passwords and login information, and to intercept e-mail and other private communications. Sometimes, organizations also snoop their employees legitimately to monitor their use of organizations' computers and track Internet usage. Answer B is incorrect. In UDP port scanning, a UDP packet is sent to each port of the target system. If the remote port is closed, the server replies that the remote port is unreachable. If the remote Port is open, no such error is generated. Many firewalls block the TCP port scanning, at that time the UDP port scanning may be useful. Certain IDS and firewalls can detect UDP port scanning easily.
NEW QUESTION 3
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to track the system for user logins. To accomplish the task, you need to analyze the log configuration files. Which of the following Unix log configuration files can you use to accomplish the task?
- A. /var/log/messages
- B. /var/log/secure
- C. /var/spool/mail
- D. /var/log/maillog
Answer: B
Explanation:
In Unix, the /var/log/secure file is used to track the systems for user logins. Answer D is incorrect. In Unix, the /var/log/maillog file is the normal system maillog file. Answer A is incorrect. In Unix, the /var/log/messages file is the main system message log file. Answer C is incorrect. In Unix, the /var/spool/mail file is the file where mailboxes are usually stored.
NEW QUESTION 4
You are the Security Consultant and you frequently do vulnerability assessments on client computers. You want to have a standardized approach that would be applicable to all of your clients when doing a vulnerability assessment. What is the best way to do this?
- A. Utilize OVAL.
- B. Create your own standard and use it with all clients.
- C. Utilize each client's security policies when doing a vulnerability assessment for that client.
- D. Utilize the Microsoft security recommendations.
Answer: A
Explanation:
Open Vulnerability Assessment Language (OVAL) is a common language for security professionals to use when checking for the presence of vulnerabilities on computer systems. OVAL provides a baseline method for performing vulnerability assessments on local computer systems. Answer D is incorrect. While Microsoft security standards will be appropriate for many of your clients, they won't help clients using Linux, Macintosh, or Unix. They also won't give you insight into checking your firewalls or routers. Answer C is incorrect. This would not fulfill the requirement of having a standardized approach applicable to all clients. B is incorrect. This would not be the best way. You should use common industry standards, like OVAL.
NEW QUESTION 5
John works as a Network Administrator for Perfect Solutions Inc. The company has a
Linux-based network. John is working as a root user on the Linux operating system. He has recently backed up his entire Linux hard drive into the my_backup.tgz file. The size of the my_backup.tgz file is 800MB. Now, he wants to break this file into two files in which the size of the first file named my_backup.tgz.aa should be 600MB and that of the second file named my_backup.tgz.ab should be 200MB. Which of the following commands will John use to accomplish his task?
- A. split --verbose -b 200m my_backup.tgz my_backup.tgz
- B. split --verbose -b 200m my_backup.tgz my_backup.tgz
- C. split --verbose -b 600m my_backup.tgz my_backup.tgz
- D. split --verbose -b 600m my_backup.tgz my_backup.tgz
Answer: D
Explanation:
According to the scenario, John wants to break the my_backup.tgz file into two files in which the size of the first file named my_backup.tgz.aa should be 600MB and that of the second file named my_backup.tgz.ab should be 200MB. Hence, he will use the the split --verbose -b 600 my_backup.tgz my_backup.tgz. command, which will automatically break the first file into 600MB named my_backup.tgz.aa, and the rest of the data (200MB) will be assigned to the second file named my_backup.tgz.ab. The reason behind the names is that the split command provides suffixes as 'aa', 'ab', 'ac', ..., 'az', 'ba', 'bb', etc. in the broken file names by default. Hence, both conditions, the file names as well as the file sizes, match with this command. Note: If the size of the tar file my_backup.tgz is 1300MB, the command split --verbose -b 600 my_backup.tgz my_backup.tgz. breaks the my_backup.tgz file into three files, i.e., my_backup.tgz.aa of size 600MB, my_backup.tgz.ab of size 600MB, and my_backup.tgz.ac of size 100MB.
NEW QUESTION 6
Sarah works as a Web Developer for XYZ CORP. She is creating a Web site for her company. Sarah wants greater control over the appearance and presentation of Web pages. She wants the ability to precisely specify the display attributes and the appearance of elements on the Web pages. How will she accomplish this?
- A. Use the Database Design wizard.
- B. Make two templates, one for the index page and the other for all other pages.
- C. Use Cascading Style Sheet (CSS).
- D. Make a template and use it to create each Web page.
Answer: C
Explanation:
Sarah should use the Cascading Style Sheet (CSS) while creating Web pages. This will give her greater control over the appearance and presentation of the Web pages and will also enable her to precisely specify the display attributes and the appearance of elements on the Web pages.
NEW QUESTION 7
You work as a Desktop Support Technician for XYZ CORP. The company uses a Windows-based network comprising 50 Windows XP Professional computers. You want to
include the Safe Mode with Command Prompt feature into the boot.ini file of a Windows XP Professional computer. Which of the following switches will you use?
- A. /safeboot:network /sos /bootlog /noguiboot
- B. /safeboot:minimal /sos /bootlog /noguiboot
- C. /safeboot:minimal(alternateshell) /sos /bootlog /noguiboot
- D. /safeboot:dsrepair /sos
Answer: C
Explanation:
Safe-mode boot switches are used in the Windows operating systems to use the afe-mode boot feature. To use this feature the user should press F8 during boot. These modes are available in the Boot.ini file. Users can also automate the boot process using this feature. Various switches used for various modes are given below:
NEW QUESTION 8
Which of the following statements are true about data aggregation?
- A. A common aggregation purpose is to get more information about particular groups based on specific variables.
- B. Data aggregation cannot be user-based.
- C. Data aggregation is any process in which information is gathered and expressed in a summary form.
- D. Online analytic processing (OLAP) is a simple type of data aggregation.
Answer: ACD
Explanation:
Data aggregation is any process in which information is gathered and expressed in a summary form, for purposes such as statistical analysis. A common aggregation purpose is to get more information about particular groups based on specific variables such as age, profession, or income. The information about such groups can then be used for Web site personalization to choose content and advertising likely to appeal to an individual belonging to one or more groups for which data has been collected. For example, a site that sells music CDs might advertise certain CDs based on the age of the user and the data aggregate for their age group. Online analytic processing (OLAP) is a simple type of data aggregation in which the marketer uses an online reporting mechanism to process the information. Answer B is incorrect. Data aggregation can be user-based. Personal data aggregation services offer the user a single point for collection of their personal information from other Web sites. The customer uses a single master personal identification number (PIN) to give them access to their various accounts (such as those for financial institutions, airlines, book and music clubs, and so on). Performing this type of data aggregation is sometimes referred to as "screen scraping."
NEW QUESTION 9
You work as a Software Developer for UcTech Inc. You are building a Web site that will contain study materials on the Java language. The company wants that members can
access all the pages, but non-members have only limited access to the Web site pages. Which of the following security mechanisms will you use to accomplish the task?
- A. Data integrity
- B. Authentication
- C. Confidentiality
- D. Authorization
Answer: D
Explanation:
Authorization is a process that verifies whether a user has permission to access a Web resource. A Web server can restrict access to some of its resources to only those clients that log in using a recognized username and password. To be authorized, a user must first be authenticated. Answer B is incorrect. Authentication is the process of verifying the identity of a user. This is usually done using a user name and password. This process compares the provided user name and password with those stored in the database of an authentication server. Answer C is incorrect. Confidentiality is a mechanism that ensures that only the intended and authorized recipients are able to read data. The data is so encrypted that even if an unauthorized user gets access to it, he will not get any meaning out of it. Answer A is incorrect. Data integrity is a mechanism that ensures that the data is not modified during transmission from source to destination. This means that the data received at the destination should be exactly the same as that sent from the source.
NEW QUESTION 10
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint. Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
- A. nmap -sS
- B. nmap -sU -p
- C. nmap -O -p
- D. nmap -sT
Answer: C
Explanation:
The nmap -O -p switch can be used to perform TCP/IP stack fingerprinting. Nmap is a free open-source utility for network exploration and security auditing. It is used to discover computers and services on a computer network, thus creating a "map" of the network. Just like many simple port scanners, Nmap is capable of discovering passive services. In addition, Nmap may be able to determine various details about the remote computers. These include operating system, device type, uptime, software product used to run a service, exact version number of that product, presence of some firewall techniques and, on a local area network, even vendor of the remote network card. Nmap runs on Linux, Microsoft Windows etc. Answer B is incorrect. The nmap -sU -p switch can be used to perform UDP port scanning. Answer A is incorrect. The nmap -sS switch is used to perform a TCP half scan. TCP SYN scanning is also known as half-open scanning because in this a full TCP connection is never opened. Answer D is incorrect. The nmap -sT switch is used to perform a TCP full scan.
NEW QUESTION 11
You work as a Software Developer for UcTech Inc. You build an online book shop, so that users can purchase books using their credit cards. You want to ensure that only the administrator can access the credit card information sent by users. Which security mechanism will you use to accomplish the task?
- A. Confidentiality
- B. Data integrity
- C. Authentication
- D. Authorization
Answer: A
Explanation:
Confidentiality is a mechanism that ensures that only the intendeA, Duthorized recipients are able to read data. The data is so encrypted that even if an unauthorized user gets access to it, he will not get any meaning out of it. Answer D is incorrect. Authorization is a process that verifies whether a user has permission to access a Web resource. A Web server can restrict access to some of its resources to only those clients that log in using a recognized username and password. To be authorized, a user must first be authenticated. Answer C is incorrect. Authentication is the process of verifying the identity of a user. This is usually done using a user name and password. This process compares the provided user name and password with those stored in the database of an authentication server. Answer B is incorrect. Data integrity is a mechanism that ensures that the data is not modified during transmission from source to destination. This means that the data received at the destination should be exactly the same as that sent from the source.
NEW QUESTION 12
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP based switched network. A root bridge has been elected in the switched network. You have installed a new switch with a lower bridge ID than the existing root bridge. What will happen?
- A. The new switch starts advertising itself as the root bridge.
- B. The new switch divides the network into two broadcast domains.
- C. The new switch works as DR or BDR.
- D. The new switch blocks all advertisements.
Answer: A
Explanation:
The new switch starts advertising itself as the root bridge. It acts as it is the only bridge on the network. It has a lower Bridge ID than the existing root, so it is elected as the root bridge after the BPDUs converge and when all switches know about the new switch that it is the better choice. Answer B, C, D are incorrect. All these are not valid options, according to the given scenario.
NEW QUESTION 13
Which of the following statements about a perimeter network are true? (Choose three)
- A. It has a connection to the Internet through an external firewall and a connection to an internal network through an interior firewall.
- B. It has a connection to a private network through an external firewall and a connection to an internal network through an interior firewall.
- C. It is also known as a demilitarized zone or DMZ.
- D. It prevents access to the internal corporate network for outside users.
Answer: ACD
Explanation:
A perimeter network, also known as a demilitarized zone or DMZ, is a small network that lies in between the Internet and a private network. It has a connection to the Internet through an external firewall and a connection to the internal network through an interior firewall. It allows outside users access to the specific servers located in the perimeter network while preventing access to the internal corporate network. Servers, routers, and switches that maintain security by preventing the internal network from being exposed on the Internet are placed in a perimeter network. A perimeter network is commonly used for deploying e-mail and Web servers for a company.
NEW QUESTION 14
You work as a Network Administrator for XYZ CORP. The company has a Windows-based network. You want to configure the ACL with a Cisco router. Which of the following router prompts can you use to accomplish the task?
- A. router(config-if)#
- B. router(config)#
- C. router(config-ext-nacl)#
- D. router#
Answer: C
Explanation:
The auditor of a Cisco router should be familiar with the variety of privilege modes. The current privilege mode can be quickly identified by looking at the current router prompt. The prime modes of a Cisco router are as follows: #Nonprivileged mode: router>
#Priviledged mode: router# #Global configuration mode: router(config)# #Interface configuration mode: router(config-if)# #ACL configuration mode: router(config-ext-nacl)#
#Boot loader mode: router(boot) #Remote connectivity config mode: router(config-line)#
NEW QUESTION 15
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to run a command that forces all the unwritten blocks in the buffer cache to be written to the disk. Which of the following Unix commands can you use to accomplish the task?
- A. swapon
- B. tune2fs
- C. swapoff
- D. sync
Answer: D
Explanation:
The sync command is used to flush filesystem buffers. It ensures that all disk writes have been completed before the processor is halted or rebooted. Generally, it is preferable to use reboot or halt to shut down a system, as they may perform additional actions such as resynchronizing the hardware clock and flushing internal caches before performing a final sync. Answer B is incorrect. In Unix, the tune2fs command is used to adjust tunable filesystem parameters on the second extended filesystems. Answer A is incorrect. In Unix, the swapon command is used to activate a swap partition. Answer C is incorrect. In Unix, the swapoff command is used to de-activate a swap partition.
NEW QUESTION 16
In which of the following attacking methods does an attacker distribute incorrect IP address?
- A. DNS poisoning
- B. IP spoofing
- C. Mac flooding
- D. Man-in-the-middle
Answer: A
Explanation:
In DNS poisoning attack, an attacker distributes incorrect IP address. DNS cache poisoning is a maliciously created or unintended situation that provides data to a caching name server that did not originate from authoritative Domain Name System (DNS) sources. Once a DNS server has received such non-authentic datA, Caches it for future performance increase, it is considered poisoned, supplying the non-authentic data to the clients of the server. To perform a cache poisoning attack, the attacker exploits a flaw in the DNS software. If the server does not correctly validate DNS responses to ensure that they are from an authoritative source, the server will end up caching the incorrect entries locally and serve them to other users that make the same request. Answer B is incorrect. IP (Internet Protocol) address spoofing is an attack in which an attacker creates the IP packets with a forged (spoofed) source IP address with the purpose of concealing the identity of the sender or impersonating another computing system. The basic protocol for sending data over the Internet and many other computer networks is the Internet Protocol ("IP"). The header of each IP packet contains, among other things, the numerical source and destination address of the packet. The source address is normally the address that the packet was sent from. By forging the header so it contains a different address, an attacker can make it appear that the packet was sent by a different machine. The machine that receives spoofed packets will send response back to the forged source address, which means that this technique is mainly used when the attacker does not care about the response or the attacker has some way of guessing the response. Answer D is incorrect. Man-in-the-middle attacks occur when an attacker successfully inserts an intermediary software or program between two communicating hosts. The intermediary software or program allows attackers to listen to and modify the communication packets passing between the two hosts. The software intercepts the communication packets and then sends the information to the receiving host. The receiving host responds to the software, presuming it to be the legitimate client. Answer C is incorrect. MAC flooding is a technique employed to compromise the security of network switches. In a typical MAC flooding attack, a switch is flooded with packets, each containing different source MAC addresses. The intention is to consume the limited memory set aside in the switch to store the MAC address-to-physical port translation table. The result of this attack causes the switch to enter a state called failopen mode, in which all incoming packets are broadcast out on all ports (as with a hub), instead of just down the correct port as per normal operation. A malicious user could then use a packet sniffer (such as Wireshark) running in promiscuous mode to capture sensitive data from other computers (such as unencrypted passwords, e- mail and instant messaging conversations), which would not be accessible were the switch operating normally.
NEW QUESTION 17
Which of the following are the countermeasures against WEP cracking?
- A. Using the longest key supported by hardware.
- B. Changing keys often.
- C. Using a non-obvious key.
- D. Using a 16 bit SSID.
Answer: ABC
Explanation:
A user can use some countermeasures to prevent WEP cracking. Although WEP is least secure, it should not be used. However, a user can use the following methods to mitigate WEP cracking: Use a non-obvious key. Use the longest key supported by hardware. Change keys often. Use WEP in combination with other security features, such as rapid WEP key rotation and dynamic keying using 802.1x. Consider WEP a deterrent, not a guarantee. Answer D is incorrect. SSID stands for Service Set Identifier. It is used to identify a wireless network. SSIDs are case sensitive text strings and have a maximum length of 32 characters. All wireless devices on a wireless network must have the same SSID in order to communicate with each other. The SSID on computers and the devices in WLAN can be set manually and automatically. Configuring the same SSID as that of the other Wireless Access Points (WAPs) of other networks will create a conflict. A network administrator often uses a public SSID that is set on the access point. The access point broadcasts SSID to all wireless devices within its range. Some newer wireless access points have the ability to disable the automatic SSID broadcast feature in order to improve network security.
NEW QUESTION 18
You work as a Software Developer for UcTech Inc. You want to ensure that a class is informed whenever an attribute is added, removed, or replaced in a session. Which of the following is the event that you will use to accomplish the task?
- A. HttpSessionBindingEvent
- B. HttpAttributeEvent
- C. HttpSessionEvent
- D. HttpSessionAttributeEvent
Answer: A
Explanation:
To be informed whenever an attribute is added, removed, or replaced in a session, a class must have a method with HttpSessionBindingEvent as its attribute. The HttpSessionBindingEvent class extends the HttpSessionEvent class. The HttpSessionBindingEvent class is used with the following listeners: HttpSessionBindingListener: It notifies the attribute when it is bound or unbound from a session. HttpSessionAttributeListener: It notifies the class when an attribute is bound, unbound, or replaced in a session. The session binds the object by a call to the HttpSession.setAttribute() method and unbinds the object by a call to the HttpSession.removeAttribute() method. Answer C is incorrect. The HttpSessionEvent is associated with the HttpSessionListener interface and HttpSessionActivationListener.
NEW QUESTION 19
......
Recommend!! Get the Full GSNA dumps in VCE and PDF From Dumpscollection.com, Welcome to Download: https://www.dumpscollection.net/dumps/GSNA/ (New 368 Q&As Version)
