Proper study guides for Replace GIAC GIAC Systems and Network Auditor certified begins with GIAC GSNA preparation products which designed to deliver the Validated GSNA questions by making you pass the GSNA test at your first time. Try the free GSNA demo right now.
Free demo questions for GIAC GSNA Exam Dumps Below:
NEW QUESTION 1
You work as a Software Developer for UcTech Inc. You want to create a new session. Which of the following methods can you use to accomplish the task?
- A. getNewSession(true)
- B. getSession(false)
- C. getSession()
- D. getSession(true)
- E. getNewSession()
Answer: CD
Explanation:
The getSession() method of the HttpServletRequest interface returns the current session associated with the request, or creates a new session if no session exists. The method has two syntaxes as follows: public HttpSession getSession(): This method creates a new session if it does not exist. public HttpSession getSession(boolean create): This method becomes similar to the above method if create is true, and returns the current session if create is false. It returns null if no session exists. Answer B is incorrect. The getSession(false) method returns a pre-existing session. It returns null if the client has no session associated with it.
NEW QUESTION 2
You work as a Network Auditor for XYZ CORP. The company has a Windows-based network. While auditing the company's network, you are facing problems in searching the faults and other entities that belong to it. Which of the following risks may occur due to the existence of these problems?
- A. Residual risk
- B. Inherent risk
- C. Secondary risk
- D. Detection risk
Answer: D
Explanation:
Detection risks are the risks that an auditor will not be able to find what they are looking to detect. Hence, it becomes tedious to report negative results when material conditions (faults) actually exist. Detection risk includes two types of risk: Sampling risk: This risk occurs when an auditor falsely accepts or erroneously rejects an audit sample. Nonsampling risk: This risk occurs when an auditor fails to detect a condition because of not applying the appropriate procedure or using procedures inconsistent with the audit objectives (detection faults). Answer A is incorrect. Residual risk is the risk or danger of an action or an event, a method or a (technical) process that, although being abreast with science, still conceives these dangers, even if all theoretically possible safety measures would be applied (scientifically conceivable measures). The formula to calculate residual risk is (inherent risk) x (control risk) where inherent risk is (threats vulnerability). In the economic context, residual means "the quantity left over at the end of a process; a remainder". Answer B is incorrect. Inherent risk, in auditing, is the risk that the account or section being audited is materially misstated without considering internal controls due to error or fraud. The assessment of inherent risk depends on the professional judgment of the auditor, and it is done after assessing the business environment of the entity being audited. Answer C is incorrect. A secondary risk is a risk that arises as a straight consequence of implementing a risk response. The secondary risk is an outcome of dealing with the original risk. Secondary risks are not as rigorous or important as primary risks, but can turn out to be so if not estimated and planned properly.
NEW QUESTION 3
You work as the Network Administrator for a company. You configure a Windows 2000- based computer as the Routing and Remote Access server, so that users can access the company's network, remotely. You want to log a record of all the users who access the network by using Routing and Remote Access. What will you do to log all the logon activities?
- A. On the Routing and Remote Access server, enable log authentication requests in auditing, and define the path for the log file in Remote Access Logging.
- B. On the Routing and Remote Access server, enable log authentication requests in Remote Access Logging.
- C. On the Routing and Remote Access server, enable log authentication requests in auditing.
- D. Do nothing as the Windows 2000-based Routing and Remote Access server automatically creates a log record for each connection attempt.
Answer: B
Explanation:
The Routing and Remote Access service can log all the records of authentication and accounting information for connection attempts when Windows authentication or accounting is enabled. This can be done by enabling the log authentication requests in the properties of the Remote Access Logging folder, in the Routing and Remote Access snap-in , where you can configure the type of activity to log, i.e., accounting or authentication activity and log file settings. This information is stored in the form of a log file in '%SystemRoot%System32LogFiles' folder. For each authentication attempt, the name of the remote access policy , that either accepted or rejected the connection attempt, is recorded. The logged information is useful to track remote access usage, and authentication attempts.
NEW QUESTION 4
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for
network exploration. The tool uses raw IP packets to determine the following: What ports are open on our network systems. What hosts are available on the network. Identify unauthorized wireless access points. What services (application name and version) those hosts are offering. What operating systems (and OS versions) they are running. What type of packet filters/firewalls are in use. Which of the following tools is Victor using?
- A. Nessus
- B. Sniffer
- C. Nmap
- D. Kismet
Answer: C
Explanation:
Nmap is a free open-source utility for network exploration and security auditing. It is used to discover computers and services on a computer network, thus creating a "map" of the network. Just like many simple port scanners, Nmap is capable of discovering passive services. In addition, Nmap may be able to determine various details about the remote computers. These include operating system, device type, uptime, software product used to run a service, exact version number of that product, presence of some firewall techniques and, on a local area network, even vendor of the remote network card. Nmap runs on Linux, Microsoft Windows etc. Answer D is incorrect. Kismet is a Linux-based 802.11 wireless network sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic Answer A is incorrect. Nessus is proprietary comprehensive vulnerability scanning software. It is free of charge for personal use in a non-enterprise environment. Its goal is to detect potential vulnerabilities on the tested systems. It is capable of checking various types of vulnerabilities, some of which are as follows: Vulnerabilities that allow a remote cracker to control or access sensitive data on a system. Misconfiguration (e.g. open mail relay, missing patches, etc). Default passwords, a few common passwords, and blank/absent passwords on some system accounts. Nessus can also call Hydra (an external tool) to launch a dictionary attack. Denials of service against the TCP/IP stack by using mangled packets. Answer B is incorrect. A sniffer is a software tool that is used to capture any network traffic. Since a sniffer changes the NIC of the LAN card into promiscuous mode, the NIC begins to record incoming and outgoing data traffic across the network. A sniffer attack is a passive attack because the attacker does not directly connect with the target host. This attack is most often used to grab logins and passwords from network traffic. Tools such as Ethereal, Snort, Windump, EtherPeek, Dsniff are some good examples of sniffers. These tools provide many facilities to users such as graphical user interface, traffic statistics graph, multiple sessions tracking, etc.
NEW QUESTION 5
Sarah works as a Web Developer for XYZ CORP. She develops a Web site for the company. She uses tables in the Web site. Sarah embeds three tables within a table. What is the technique of embedding tables within a table known as?
- A. Nesting tables
- B. Stacking tables
- C. CSS tables
- D. Horned tables
Answer: A
Explanation:
In general, nesting means embedding a construct inside another. Nesting tables is a technique in which one or more tables are embedded within a table. Answer B, C, D are incorrect. There are no techniques such as stacking tables, horned tables, or CSS tables.
NEW QUESTION 6
You want to change the number of characters displaying on the screen while reading a txt file. However, you do not want to change the format of the txt file. Which of the following commands can be used to view (but not modify) the contents of the text file on the terminal screen at a time?
- A. cat
- B. tail
- C. less
- D. more
Answer: D
Explanation:
The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,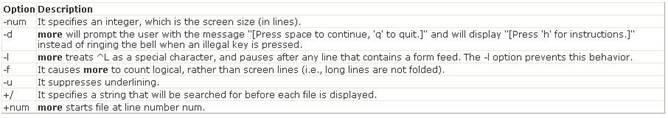
Answer A is incorrect. The concatenate (cat) command is used to display or print the contents of a file. Syntax: cat filename For example, the following command will display the contents of the /var/log/dmesg file: cat /var/log/dmesg Note: The more command is used in conjunction with the cat command to prevent scrolling of the screen while displaying the contents of a file. Answer C is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,
Answer B is incorrect. The tail command is used to display the last few lines of a text file or piped data.
NEW QUESTION 7
Data mining is a process of sorting through data to identify patterns and establish relationships. Which of the following data mining parameters looks for patterns where one event is connected to another event?
- A. Sequence or path analysis
- B. Forecasting
- C. Clustering
- D. Association
Answer: D
Explanation:
Data mining is a process of sorting through data to identify patterns and establish relationships. Following are the data mining parameters: Association: Looking for patterns where one event is connected to another event. Sequence or path analysis: Looking for patterns where one event leads to another later event. Classification: Looking for new patterns (may result in a change in the way the data is organized but is acceptable). Clustering: Finding and visually documenting groups of facts not previously known. Forecasting: Discovering patterns in data that can lead to reasonable predictions about the future (This area of data mining is known as predictive analytics).
NEW QUESTION 8
You work as a Network Administrator for XYZ CORP. The company has a Windows-based network. You want to use multiple security countermeasures to protect the integrity of the information assets of the company. To accomplish the task, you need to create a complex and multi-layered defense system. Which of the following components can be used as a layer that constitutes 'Defense in depth'? (Choose three)
- A. Backdoor
- B. Firewall
- C. Antivirus software
- D. Intrusion detection
Answer: BCD
Explanation:
The components of Defense in depth include antivirus software, firewalls, anti-spyware programs, hierarchical passwords, intrusion detection, and biometric verification. In addition to electronic countermeasures, physical protection of business sites along with comprehensive and ongoing personnel training enhances the security of vital data against compromise, theft, or destruction. Answer A is incorrect. A backdoor is any program that allows a hacker to connect to a computer without going through the normal authentication process. The main advantage of this type of attack is that the network traffic moves from inside a network to the hacker's computer. The traffic moving from inside a network to the outside world is typically the least restrictive, as companies are more concerned about what comes into a network, rather than what leaves it. It, therefore, becomes hard to detect backdoors.
NEW QUESTION 9
Which of the following is a technique of using a modem to automatically scan a list of telephone numbers, usually dialing every number in a local area code to search for computers, Bulletin board systems, and fax machines?
- A. Warkitting
- B. War driving
- C. Wardialing
- D. Demon dialing
Answer: C
Explanation:
War dialing or wardialing is a technique of using a modem to automatically scan a list of telephone numbers, usually dialing every number in a local area code to search for computers, Bulletin board systems, and fax machines. Hackers use the resulting lists for various purposes, hobbyists for exploration, and crackers - hackers that specialize in computer security - for password guessing. Answer A is incorrect. Warkitting is a combination of wardriving and rootkitting. In a warkitting attack, a hacker replaces the firmware of an attacked router. This allows them to control all traffic for the victim, and could even permit them to disable SSL by replacing HTML content as it is being downloaded. Warkitting was identified by Tsow, Jakobsson, Yang, and Wetzel in 2006. Their discovery indicated that 10% of the wireless routers were susceptible to WAPjacking (malicious configuring of the firmware settings, but making no modification on the firmware itself) and 4.4% of wireless routers were vulnerable to WAPkitting (subverting the router firmware). Their analysis showed that the volume of credential theft possible through Warkitting exceeded the estimates of credential theft due to phishing. Answer D is incorrect. In the computer hacking scene of the 1980s, demon dialing was a technique by which a computer is used to repeatedly dial a number (usually to a crowded modem pool) in an attempt to gain access immediately after another user had hung up. The expansion of accessible Internet service provider connectivity since that time more or less rendered the practice obsolete. The term "demon dialing" derives from the Demon Dialer product from Zoom Telephonics, Inc., a telephone device produced in the 1980s which repeatedly dialed busy telephone numbers under control of an extension phone. Answer B is incorrect. War driving, also called access point mapping, is the act of locating and possibly exploiting connections to wireless local area networks while driving around a city or elsewhere. To do war driving, one needs a vehicle, a computer (which can be a laptop), a wireless Ethernet card set to work in promiscuous mode, and some kind of an antenna which can be mounted on top of or positioned inside the car. Because a wireless LAN may have a range that extends beyond an office building, an outside user may be able to intrude into the network, obtain a free Internet connection, and possibly gain access to company records and other resources.
NEW QUESTION 10
Which of the following statements are true about SSIDs?
- A. Configuring the same SSID as that of the other Wireless Access Points (WAPs) of other networks will create a conflict.
- B. SSIDs are case insensitive text strings and have a maximum length of 64 characters.
- C. All wireless devices on a wireless network must have the same SSID in order to communicate with each other.
- D. SSID is used to identify a wireless network.
Answer: ACD
Explanation:
SSID stands for Service Set Identifier. It is used to identify a wireless network. SSIDs are case sensitive text strings and have a maximum length of 32 characters. All wireless devices on a wireless network must have the same SSID in order to communicate with each other. The SSID on computers and the devices in WLAN can be set manually and automatically. Configuring the same SSID as that of the other Wireless Access Points (WAPs) of other networks will create a conflict. A network administrator often uses a public SSID that is set on the access point. The access point broadcasts SSID to all wireless devices within its range. Some newer wireless access points have the ability to disable the automatic SSID broadcast feature in order to improve network security.
NEW QUESTION 11
Samantha works as a Web Developer for XYZ CORP. She is designing a Web site for the company. In a Web page, she uses the HTTP-EQUIV attribute to control the page cache. Which of the following HTTP-EQUIV values controls the page cache in the browser folder?
- A. Window-target
- B. Status-code
- C. Content-type
- D. Pragma
Answer: D
Explanation:
HTTP-EQUIV is an attribute of the META tag. It sets or retrieves information used to bind the META tag's content to an HTTP response header. The pragma value of HTTP-EQUIV controls the page cache.
NEW QUESTION 12
Which of the following types of firewall ensures that the packets are part of the established session?
- A. Stateful inspection firewall
- B. Switch-level firewall
- C. Circuit-level firewall
- D. Application-level firewall
Answer: A
Explanation:
The stateful inspection firewall combines the circuit level and the application level firewall techniques. It assures the session or connection between the two parties is valid. It also inspects packets from the session to assure that the packets are part of the established session and not malicious. Answer C is incorrect. The circuit-level firewall regulates traffic based on whether or not a trusted connection has been established. Answer D is incorrect. The application level firewall inspects the contents of packets, rather than the source/destination or connection between the two devices. Answer B is incorrect. There is no firewall type such as switch-level firewall.
NEW QUESTION 13
This is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of these tools are as follows: It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc. It is commonly used for the following purposes: a.War driving b.Detecting unauthorized access pointsc.Detecting causes of interference on a WLAN d.WEP ICV error trackinge.Making Graphs and Alarms on 802.11 Data, including Signal Strength This tool is known as .
- A. THC-Scan
- B. NetStumbler
- C. Absinthe
- D. Kismet
Answer: B
Explanation:
NetStumbler is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of NetStumbler are as follows: It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc. It is commonly used for the following purposes: a.War driving b.Detecting unauthorized access points c.Detecting causes of interference on a WLAN d.WEP ICV error tracking e.Making Graphs and Alarms on 802.11 Data, including Signal Strength
Answer D is incorrect. Kismet is an IEEE 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Answer A is incorrect. THC-Scan is a war-dialing tool. Answer C is incorrect. Absinthe is an automated SQL injection tool.
NEW QUESTION 14
Which of the following can be the countermeasures to prevent NetBIOS NULL session enumeration in Windows 2000 operating systems?
- A. Denying all unauthorized inbound connections to TCP port 53
- B. Disabling SMB services entirely on individual hosts by unbinding WINS Client TCP/IP from the interface
- C. Editing the registry key HKLM\SYSTEM\CurrentControlSet\LSA and adding the value RestrictAnonymous
- D. Disabling TCP port 139/445
Answer: BCD
Explanation:
NetBIOS NULL session vulnerabilities are hard to prevent, especially if NetBIOS is needed as part of the infrastructure. One or more of the following steps can be taken to limit NetBIOS NULL session vulnerabilities: 1.Null sessions require access to the TCP 139 or TCP 445 port, which can be disabled by a Network Administrator. 2. A Network Administrator can also disable SMB services entirely on individual hosts by unbinding WINS Client TCP/IP from the interface. 3. A Network Administrator can also restrict the anonymous user by editing the registry values: a.Open regedit32, and go to HKLM\SYSTEM\CurrentControlSet\LSA. b.Choose edit > add value. Value name: RestrictAnonymous Data Type: REG_WORD Value: 2 Answer A is incorrect. TCP port 53 is the default port for DNS zone transfer. Although disabling it can help restrict DNS zone transfer enumeration, it is not useful as a countermeasure against the NetBIOS NULL session enumeration.
NEW QUESTION 15
You run the wc -c file1.txt command. If this command displays any error message, you want to store the error message in the error.txt file. Which of the following commands will you use to accomplish the task?
- A. wc -c file1.txt >>error.txt
- B. wc -c file1.txt 1>error.txt
- C. wc -c file1.txt 2>error.txt
- D. wc -c file1.txt >error.txt
Answer: C
Explanation:
According to the scenario, you will use the wc -c file1.txt 2>error.txt command to accomplish the task. The 2> operator is an error redirector, which, while running a command, redirects the error (if it exists) on the specified file. Answer B, D are incorrect. The > or 1> redirector can be used to redirect the output of the wc -c file1.txt file to the error.txt file; however, you want to write the errors in the error.txt file, not the whole output. Answer A is incorrect. The >> operator will redirect the output of the command in the same manner as the > or 1> operator. Although the >> operator will not overwrite the error.txt file, it will append the error.txt file.
NEW QUESTION 16
Which of the following are the disadvantages of Dual-Homed Host Firewall Architecture?
- A. It can provide services by proxying them.
- B. It can provide a very low level of control.
- C. User accounts may unexpectedly enable services a user may not consider secure.
- D. It provides services when users log on to the dual-homed host directly.
Answer: ACD
Explanation:
A dual-homed host is one of the firewall architectures for implementing preventive security. It provides the first-line defense and protection technology for keeping untrusted bodies from compromising information security by violating trusted network space as shown in the image below: A dual-homed host (or bastion host) is a system fortified with two network interfaces (NICs) that sits between an un-trusted network (like the Internet) and trusted network (such as a corporate network) to provide secure access. Dual-homed, or bastion, is a general term for proxies, gateways, firewalls, or any server that provides secured applications or services directly to an untrusted network.
A dual-homed host also has some disadvantages, which are as follows:
* 1. It can provide services by proxying them.
* 2. User accounts may unexpectedly enable services a user may not consider secure.
* 3. It provides services when users log on to the dual-homed host directly.
Answer B is incorrect. Dual-Homed Host Firewall Architecture can provide a very high level of control.
NEW QUESTION 17
Which of the following is the default port for Hypertext Transfer Protocol (HTTP)?
- A. 20
- B. 443
- C. 80
- D. 21
Answer: C
Explanation:
Hypertext Transfer Protocol (HTTP) is a client/server TCP/IP protocol used on the World Wide Web (WWW) to display Hypertext Markup Language (HTML) pages. HTTP defines how messages are formatted and transmitted, and what actions Web servers and browsers should take in response to various commands. For example, when a client application or browser sends a request to the server using HTTP commands, the server responds with a message containing the protocol version, success or failure code, server information, and body content, depending on the request. HTTP uses TCP port 80 as the default port. Answer B is incorrect. Port 443 is the default port for Hypertext Transfer Protocol Secure (HTTPS) and Secure Socket Layer (SSL). Answer A, D are incorrect. By default, FTP server uses TCP port 20 for data transfer and TCP port 21 for session control.
NEW QUESTION 18
You have just taken over as the Network Administrator for a medium sized company. You want to check to see what services are exposed to the outside world. What tool would you use to accomplish this?
- A. Network mapper
- B. Protocol analyzer
- C. A port scanner
- D. Packet sniffer
Answer: C
Explanation:
A port scanner is often used on the periphery of a network by either administrators or hackers. It will tell you what ports are open. By determining what ports are open, you know what services are exposed to the outside world. For example, if port 80 is open, then HTTP traffic is allowed, meaning there should be a Web server on the network. Answer: A is incorrect. Network mappers give a topography of the network, letting you know what is on your network and where it is connected. Answer: B is incorrect. A protocol analyzer does detect if a given protocol is moving over a particular network segment, thus would detect services working on that segment. However, a port scanner is a better tool for detecting all the ports that are open. Answer: D is incorrect. Packet sniffers are used to intercept traffic and to detect the contents of that traffic.
NEW QUESTION 19
......
Thanks for reading the newest GSNA exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net GSNA dumps in VCE and PDF here: https://www.downloadfreepdf.net/GSNA-pdf-download.html (368 Q&As Dumps)
