It is more faster and easier to pass the Salesforce Identity-and-Access-Management-Architect exam by using Precise Salesforce Salesforce Certified Identity and Access Management Architect (SU23) questuins and answers. Immediate access to the Improved Identity-and-Access-Management-Architect Exam and find the same core area Identity-and-Access-Management-Architect questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Salesforce Identity-and-Access-Management-Architect Exam Dumps Below:
NEW QUESTION 1
Which three are features of federated Single sign-on solutions? Choose 3 Answers
- A. It establishes trust between Identity Store and Service Provider.
- B. It federates credentials control to authorized applications.
- C. It solves all identity and access management problems.
- D. It improves affiliated applications adoption rates.
- E. It enables quick and easy provisioning and deactivating of users.
Answer: ADE
Explanation:
The three features of federated single sign-on (SSO) solutions are: It establishes trust between identity store and service provider. Federated SSO is a process that allows users to access multiple applications or systems with one set of credentials by using a common identity provider (IdP) that authenticates the user and issues a security token to the service provider (SP) that grants access. This process requires a trust relationship between the IdP and the SP, which is established by exchanging metadata and certificates.
It establishes trust between identity store and service provider. Federated SSO is a process that allows users to access multiple applications or systems with one set of credentials by using a common identity provider (IdP) that authenticates the user and issues a security token to the service provider (SP) that grants access. This process requires a trust relationship between the IdP and the SP, which is established by exchanging metadata and certificates. It improves affiliated applications adoption rates. Federated SSO improves the user experience and satisfaction by reducing the number of login prompts, passwords, and authentication failures that users have to deal with when accessing multiple applications or systems. This can increase the usage and adoption rates of the affiliated applications or systems, as users can access them more easily and conveniently.
It improves affiliated applications adoption rates. Federated SSO improves the user experience and satisfaction by reducing the number of login prompts, passwords, and authentication failures that users have to deal with when accessing multiple applications or systems. This can increase the usage and adoption rates of the affiliated applications or systems, as users can access them more easily and conveniently. It enables quick and easy provisioning and deprovisioning of users. Federated SSO enables centralized management of user accounts and access rights by using the IdP as the source of truth for user identity and attributes. This can simplify and automate the provisioning and deprovisioning of users across multiple applications or systems, as changes made in the IdP can be reflected in the SPs without requiring manual intervention or synchronization.
It enables quick and easy provisioning and deprovisioning of users. Federated SSO enables centralized management of user accounts and access rights by using the IdP as the source of truth for user identity and attributes. This can simplify and automate the provisioning and deprovisioning of users across multiple applications or systems, as changes made in the IdP can be reflected in the SPs without requiring manual intervention or synchronization.
The other option is not a feature of federated SSO solutions. Federated SSO does not solve all identity and access management problems, as it still faces challenges such as security risks, compatibility issues, governance policies, and user education. References: [Federated Single Sign-On], [Set Up Federated Authentication Using SAML], [Benefits of Single Sign-On], [How Single Sign-On Improves Application Adoption Rates], [User Provisioning for Federated Single Sign-On], [Just-in-Time Provisioning for SAML], [Challenges of Single Sign-On]
NEW QUESTION 2
Northern Trail Outfitters (NTO) has an existing custom business-to-consumer (B2C) website that does NOT support single sign-on standards, such as Security Assertion Markup Language (SAMi) or OAuth. NTO wants to use Salesforce Identity to register and authenticate new customers on the website.
Which two Salesforce features should an identity architect use in order to provide username/password
authentication for the website? Choose 2 answers
- A. Identity Connect
- B. Delegated Authentication
- C. Connected Apps
- D. Embedded Login
Answer: BD
Explanation:
To register and authenticate new customers on the website using Salesforce Identity, the identity architect should use Delegated Authentication and Embedded Login. Delegated Authentication is a feature that allows Salesforce to delegate the authentication process to an external service, such as a custom website, instead of validating the username and password internally. Embedded Login is a feature that allows Salesforce to embed a login widget into any web page, such as a custom website, to enable users to log in with their Salesforce credentials. The other options are not relevant for this scenario. References: Delegated Authentication, Embedded Login
NEW QUESTION 3
Universal Containers (UC) has a mobile application for its employees that uses data from Salesforce as well as uses Salesforce for Authentication purposes. UC wants its mobile users to only enter their credentials the first time they run the app. The application has been live for a little over 6 months, and all of the users who were part of the initial launch are complaining that they have to re-authenticate. UC has also recently changed the URI Scheme associated with the mobile app. What should the Architect at UC first investigate?Universal Containers (UC) has a mobile application for its employees that uses data from Salesforce as well as uses Salesforce for Authentication purposes. UC wants its mobile users to only enter their credentials the first time they run the app. The application has been live for a little over 6 months, and all of the users who were part of the initial launch are complaining that they have to re-authenticate. UC has also recently changed the URI Scheme associated with the mobile app. What should the Architect at UC first investigate?
- A. Check the Refresh Token policy defined in the Salesforce Connected App.
- B. Validate that the users are checking the box to remember their passwords.
- C. Verify that the Callback URL is correctly pointing to the new URI Scheme.
- D. Confirm that the access Token's Time-To-Live policy has been set appropriately.
Answer: A
Explanation:
The first thing that the architect at UC should investigate is the refresh token policy defined in the Salesforce connected app. A refresh token is a credential that allows an application to obtain new access tokens without requiring the user to re-authenticate. The refresh token policy determines how long a refresh token is valid and under what conditions it can be revoked. If the refresh token policy is set to expire after a certain period of time or after a change in IP address or device ID, then the users may have to re-authenticate after using the app for a while or from a different location or device. Option B is not a good choice because validating that the users are checking the box to remember their passwords may not be relevant, as the app uses SSO with a third-party identity provider and does not rely on Salesforce credentials. Option C is not a good choice because verifying that the callback URL is correctly pointing to the new URI scheme may not be necessary, as the callback URL is used for redirecting the user back to the app after authentication, but it does not affect how long the user can stay authenticated. Option D is not a good choice because confirming that the access token’s time-to-live policy has been set appropriately may not be effective, as the access token’s time-to-live policy determines how long an access token is valid before it needs to be refreshed by a refresh token, but it does not affect how long a refresh token is valid or when it can be revoked. References: [Connected Apps Developer Guide], [Digging Deeper into OAuth 2.0 on Force.com]
NEW QUESTION 4
Universal Containers (UC) wants to build a mobile application that twill be making calls to the Salesforce REST API. UC's Salesforce implementation relies heavily on custom objects and custom Apex code. UC does not want its users to have to enter credentials every time they use the app. Which two scope values should an Architect recommend to UC? Choose 2 answers.
- A. Custom_permissions
- B. Api
- C. Refresh_token
- D. Full
Answer: BC
Explanation:
The two scope values that an architect should recommend to UC are api and refresh_token. The api scope allows the app to access the Salesforce REST API and use custom objects and custom Apex code. The refresh_token scope allows the app to obtain a refresh token that can be used to get new access tokens without requiring the user to re-enter credentials. Option A is not a good choice because the custom_permissions scope allows the app to access custom permissions in Salesforce, but it does not affect how the app can access the REST API or avoid user re-authentication. Option D is not a good choice because the full scope allows the app to access all data accessible by the user, including the web UI and the API, but it may be unnecessary or insecure for UC’s requirement. References: OAuth 2.0 Web Server Authentication Flow, Digging Deeper int OAuth 2.0 on Force.com
NEW QUESTION 5
Northern Trail Outfitters manages application functional permissions centrally as Active Directory groups. The CRM_Superllser and CRM_Reportmg_SuperUser groups should respectively give the user the SuperUser and Reportmg_SuperUser permission set in Salesforce. Salesforce is the service provider to a Security Assertion Markup Language (SAML) identity provider.
Mow should an identity architect ensure the Active Directory groups are reflected correctly when a user accesses Salesforce?
- A. Use the Apex Just-in-Time handler to query standard SAML attributes and set permission sets.
- B. Use the Apex Just-in-Time handler to query custom SAML attributes and set permission sets.
- C. Use a login flow to query custom SAML attributes and set permission sets.
- D. Use a login flow to query standard SAML attributes and set permission sets.
Answer: B
Explanation:
Using the Apex Just-in-Time handler to query custom SAML attributes and set permission sets is the best way to ensure that the Active Directory groups are reflected correctly when a user accesses Salesforce. The Apex Just-in-Time handler is a custom class that can process the SAML response from the identity provider and assign permission sets based on the user’s AD groups. The other options are either not feasible or not effective for this use case. References: Just-in-Time Provisioning for SAML, Apex Just-in-Time Handler
NEW QUESTION 6
Refer to the exhibit.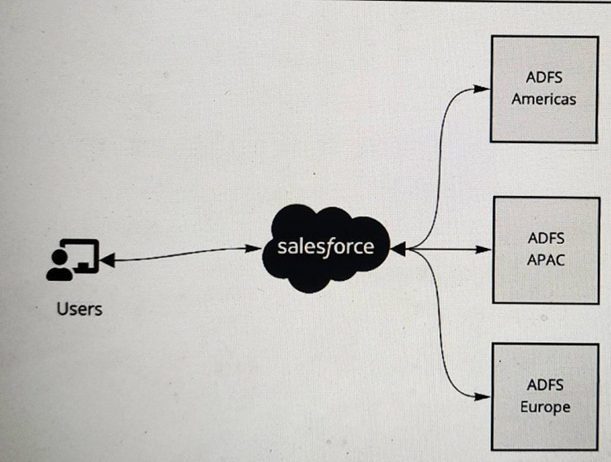
A multinational company is looking to rollout Salesforce globally. The company has a Microsoft Active Directory Federation Services (ADFS) implementation for the Americas, Europe and APAC. The company plans to have a single org and they would like to have all of its users access Salesforce using the ADFS . The company would like to limit its investments and prefer not to procure additional applications to satisfy the requirements.
What is recommended to ensure these requirements are met ?
- A. Use connected apps for each ADFS implementation and implement Salesforce site to authenticate users across the ADFS system applicable to their geo.
- B. Implement Identity Connect to provide single sign-on to Salesforce and federated across multiple ADFS systems.
- C. Add a central identity system that federates between the ADFS systems and integrate with Salesforce for single sign-on.
- D. Configure Each ADFS system under single sign-on settings and allow users to choose the system to authenticate during sign on to Salesforce
Answer: B
Explanation:
To have all of its user’s access Salesforce using the ADFS, the multinational company should implement Identity Connect to provide single sign-on to Salesforce and federate across multiple ADFS systems. Identity Connect is a tool that synchronizes user data between Microsoft Active Directory and Salesforce. It allows single sign-on and federation between multiple Active Directory domains and a single Salesforce org. Identity Connect can also handle user provisioning and deprovisioning based on the changes made in Active Directory. The other options are not recommended for this scenario, as they either require additional applications, do not support federation, or do not provide a seamless user experience. References: Identity Connect Implementation Guide, Identity Connect Overview
NEW QUESTION 7
Universal containers (UC) has implemented ansp-Initiated SAML flow between an external IDP and salesforce. A user at UC is attempting to login to salesforce1 for the first time and is being prompted for salesforce credentials instead of being shown the IDP login page. What is the likely cause of the issue?
- A. The "Redirect to Identity Provider" option has been selected in the my domain configuration.
- B. The user has not configured the salesforce1 mobile app to use my domain for login
- C. The "Redirect to identity provider" option has not been selected the SAML configuration.
- D. The user has not been granted the "Enable single Sign-on" permission
Answer: B
Explanation:
B is correct because the user has not configured the Salesforce1 mobile app to use My Domain for login, which is the likely cause of the issue. The My Domain URL is used to redirect the user to the identity provider’s login page and initiate the SP-Initiated SAML flow. If the user does not configure the Salesforce1 mobile app to use My Domain for login, they will be prompted for Salesforce credentials instead of being shown the IDP login page. A is incorrect because the “Redirect to Identity Provider” option has been selected in the My Domain configuration, which is not the cause of the issue. The “Redirect to Identity Provider” option determines whether users are redirected to the identity provider’s login page automatically or after clicking a button. C is incorrect because the “Redirect to Identity Provider” option has not been selected in the SAML configuration, which is not the cause of the issue. The “Redirect to Identity Provider” option determines whether users are redirected to the identity provider’s login page automatically or after clicking a button. D is incorrect because the user has been granted the “Enable Single Sign-On” permission, which is not the cause of the issue. The “Enable Single Sign-On” permission allows users to use SSO with connected apps or external systems. Verified References: [My Domain URL], [SP-Initiated SAML Flow], [Redirect to Identity Provider Option], [Enable Single Sign-On Permission]
NEW QUESTION 8
which three are features of federated Single Sign-on solutions? Choose 3 answers
- A. It federates credentials control to authorized applications.
- B. It establishes trust between Identity store and service provider.
- C. It solves all identity and access management problems.
- D. It improves affiliated applications adoption rates.
- E. It enables quick and easy provisioning and deactivating of users.
Answer: ABD
Explanation:  It federates credentials control to authorized applications. This means that users can access multiple applications across different domains or organizations using one set of credentials, without having to share their passwords with each application1. The applications rely on a trusted identity provider (IdP) to authenticate the users and grant them access.
It federates credentials control to authorized applications. This means that users can access multiple applications across different domains or organizations using one set of credentials, without having to share their passwords with each application1. The applications rely on a trusted identity provider (IdP) to authenticate the users and grant them access. It establishes trust between Identity store and service provider. This means that the IdP and the service provider (SP) have a mutual agreement to exchange identity information using standard protocols, such as SAML, OpenID Connect, or OAuth2. The IdP and the SP also share metadata and certificates to ensure secure communication and verification.
It establishes trust between Identity store and service provider. This means that the IdP and the service provider (SP) have a mutual agreement to exchange identity information using standard protocols, such as SAML, OpenID Connect, or OAuth2. The IdP and the SP also share metadata and certificates to ensure secure communication and verification. It improves affiliated applications adoption rates. This means that users are more likely to use applications that are connected to their existing identity provider, as they do not have to create or remember multiple passwords3. This also reduces the friction and frustration of logging in to different applications, and enhances the user experience.
It improves affiliated applications adoption rates. This means that users are more likely to use applications that are connected to their existing identity provider, as they do not have to create or remember multiple passwords3. This also reduces the friction and frustration of logging in to different applications, and enhances the user experience.
The other options are not features of federated single sign-on solutions because: It solves all identity and access management problems. This is false, as federated single sign-on solutions only address the authentication aspect of identity and access management, not the authorization, provisioning, governance, or auditing aspects. Federated single sign-on solutions also have some challenges, such as complexity, interoperability, and security risks.
It solves all identity and access management problems. This is false, as federated single sign-on solutions only address the authentication aspect of identity and access management, not the authorization, provisioning, governance, or auditing aspects. Federated single sign-on solutions also have some challenges, such as complexity, interoperability, and security risks. It enables quick and easy provisioning and deactivating of users. This is not necessarily true, as
It enables quick and easy provisioning and deactivating of users. This is not necessarily true, as
federated single sign-on solutions do not automatically create or delete user accounts in the service provider applications. Users still need to be provisioned and deprovisioned manually or through other mechanisms, such as just-in-time provisioning or SCIM.
References: Federated Identity Management vs. Single Sign-On: What’s the Difference?, What is single sign-on?, Single Sign-On (SSO) Solution, [Identity Management vs. Access Management: What’s the Difference?], [Federated Identity Management Challenges], [Just-in-Time Provisioning for SAML], [SCIM User Provisioning]
NEW QUESTION 9
A university is planning to set up an identity solution for its alumni. A third-party identity provider will be used for single sign-on Salesforce will be the system of records. Users are getting error messages when logging in.
Which Salesforce feature should be used to debug the issue?
- A. Apex Exception Email
- B. View Setup Audit Trail
- C. Debug Logs
- D. Login History
Answer: D
NEW QUESTION 10
What information does the 'Relaystate' parameter contain in sp-Initiated Single Sign-on?
- A. Reference to a URL redirect parameter at the identity provider.
- B. Reference to a URL redirect parameter at the service provider.
- C. Reference to the login address URL of the service provider.
- D. Reference to the login address URL of the identity Provider.
Answer: B
Explanation:
The ‘Relaystate’ parameter is an HTTP parameter that can be included as part of the SAML request and SAML response. In an SP-initiated sign-in flow, the SP can set the RelayState parameter in the SAML request with additional information about the request, such as the URL of the resource that the user is trying to access.
The IDP should just relay it back in the SAML response without any modification or inspection. Therefore, the ‘Relaystate’ parameter contains a reference to a URL redirect parameter at the service provider123.
References: 1: single sign on - What is exactly RelayState parameter used in SSO (Ex. SAML)? - Stack
Overflow 2: java - How to send current URL as relay state while sending authentication request to IDP - Stack Overflow 3: Understanding SAML | Okta Developer
NEW QUESTION 11
Sales users at Universal containers use salesforce for Opportunity management. Marketing uses a third-party application called Nest for Lead nurturing that is accessed using username/password. The VP of sales wants to open up access to nest for all sales uses to provide them access to lead history and would like SSO for better adoption. Salesforce is already setup for SSO and uses Delegated Authentication. Nest can accept username/Password or SAML-based Authentication. IT teams have received multiple password-related issues for nest and have decided to set up SSO access for Nest for Marketing users as well. The CIO does not want to invest in a new IDP solution and is considering using Salesforce for this purpose. Which are appropriate license type choices for sales and marketing users, giving salesforce is using Delegated Authentication? Choose 2 answers
- A. Salesforce license for sales users and Identity license for Marketing users
- B. Salesforce license for sales users and External Identity license for Marketing users
- C. Identity license for sales users and Identity connect license for Marketing users
- D. Salesforce license for sales users and platform license for Marketing users.
Answer: AD
Explanation:
The appropriate license type choices for sales and marketing users, given that Salesforce is using delegated authentication, are: Salesforce license for sales users. This license type allows internal users, such as employees, to access standard and custom Salesforce objects and features, such as opportunities and reports. This license type also supports delegated authentication, which is a feature that allows Salesforce to delegate the authentication process to an external service by making a SOAP callout to a web service that verifies the user’s credentials. This license type is suitable for sales users who use Salesforce for opportunity management and need to log in with delegated authentication.
Salesforce license for sales users. This license type allows internal users, such as employees, to access standard and custom Salesforce objects and features, such as opportunities and reports. This license type also supports delegated authentication, which is a feature that allows Salesforce to delegate the authentication process to an external service by making a SOAP callout to a web service that verifies the user’s credentials. This license type is suitable for sales users who use Salesforce for opportunity management and need to log in with delegated authentication. Platform license for marketing users. This license type allows internal users to access custom Salesforce objects and features, such as custom apps and tabs. This license type also supports delegated authentication and single sign-on (SSO), which are features that allow users to log in with an external identity provider (IdP) or service provider (SP). This license type is suitable for marketing users who use a third-party application called Nest for lead nurturing and need to log in with SSO using Salesforce as the IdP or SP.
Platform license for marketing users. This license type allows internal users to access custom Salesforce objects and features, such as custom apps and tabs. This license type also supports delegated authentication and single sign-on (SSO), which are features that allow users to log in with an external identity provider (IdP) or service provider (SP). This license type is suitable for marketing users who use a third-party application called Nest for lead nurturing and need to log in with SSO using Salesforce as the IdP or SP.
The other options are not appropriate license types for this scenario. Identity license for sales or marketing users would not allow them to access standard or custom Salesforce objects and features, as this license type only supports identity features, such as SSO and social sign-on. External Identity license for marketing users would not allow them to access custom Salesforce objects and features, as this license type is designed for external users, such as customers or partners, who access a limited set of standard and custom objects in a community. Identity Connect license for marketing users is not a valid license type, as Identity Connect is a desktop application that integrates Salesforce with Microsoft Active Directory (AD) and enables SSO between the two systems. References: [Salesforce Licenses], [Delegated Authentication], [Platform Licenses], [Single Sign-On], [External Identity Licenses], [Identity Connect]
NEW QUESTION 12
Northern Trail Outfitters (NTO) wants to improve its engagement with existing customers to boost customer loyalty. To get a better understanding of its customers, NTO establishes a single customer view including their buying behaviors, channel preferences and purchasing history. All of this information exists but is spread across different systems and formats.
NTO has decided to use Salesforce as the platform to build a 360 degree view. The company already uses Microsoft Active Directory (AD) to manage its users and company assets.
What should an Identity Architect do to provision, deprovision and authenticate users?
- A. Salesforce Identity is not needed since NTO uses Microsoft AD.
- B. Salesforce Identity can be included but NTO will be required to build a custom integration with Microsoft AD.
- C. Salesforce Identity is included in the Salesforce licenses so it does not need to be considered separately.
- D. A Salesforce Identity can be included but NTO will require Identity Connect.
Answer: D
Explanation:
Identity Connect is a Salesforce product that integrates Microsoft Active Directory with Salesforce user records. It allows provisioning, deprovisioning, and authentication of users based on AD data. The other options are either incorrect or irrelevant for this use case. References: Get to Know Identity Connect, Identit
Connect
NEW QUESTION 13
Universal Containers (UC) would like its community users to be able to register and log in with Linkedin or Facebook Credentials. UC wants users to clearly see Facebook &Linkedin Icons when they register and login. What are the two recommended actions UC can take to achieve this Functionality? Choose 2 answers
- A. Enable Facebook and Linkedin as Login options in the login section of the Community configuration.
- B. Create custom Registration Handlers to link Linkedin and facebook accounts to user records.
- C. Store the Linkedin or Facebook user IDs in the Federation ID field on the Salesforce User record.
- D. Create custom buttons for Facebook and inkedin using JAVAscript/CSS on a custom Visualforce page.
Answer: AB
Explanation:
The two recommended actions UC can take to achieve the functionality of allowing community users to register and log in with LinkedIn or Facebook credentials are: Enable Facebook and LinkedIn as login options in the login section of the community configuration.
Enable Facebook and LinkedIn as login options in the login section of the community configuration.
This action allows UC to configure Facebook and LinkedIn as authorization providers in Salesforce, which are external services that authenticate users and provide information about their identity and
attributes. By enabling these login options in the community configuration, UC can display Facebook and LinkedIn icons on the community login page and allow users to log in with their existing credentials from these services. Create custom registration handlers to link LinkedIn and Facebook accounts to user records. This action allows UC to create Apex classes that implement the Auth.RegistrationHandler interface and define the logic for creating or updating user accounts in Salesforce when users log in with LinkedIn or Facebook. By creating custom registration handlers, UC can map the information from the authorization providers to the user fields in Salesforce, such as name, email, profile, or contact.
Create custom registration handlers to link LinkedIn and Facebook accounts to user records. This action allows UC to create Apex classes that implement the Auth.RegistrationHandler interface and define the logic for creating or updating user accounts in Salesforce when users log in with LinkedIn or Facebook. By creating custom registration handlers, UC can map the information from the authorization providers to the user fields in Salesforce, such as name, email, profile, or contact.
The other options are not recommended actions for this scenario. Storing the LinkedIn or Facebook user IDs in the Federation ID field on the Salesforce user record is not necessary or sufficient for enabling SSO with these services, as the Federation ID is used for SAML-based SSO, not OAuth-based SSO. Creating custom buttons for Facebook and LinkedIn using JavaScript/CSS on a custom Visualforce page is not advisable, as it would require custom code and UI development, which could increase complexity and maintenance efforts. Moreover, it would not leverage the built-in functionality of authorization providers and registration handlers that Salesforce provides. References: [Authorization Providers], [Enable Social Sign-On for Your Community], [Create a Registration Handler Class], [Auth.RegistrationHandler Interface], [Federation ID]
NEW QUESTION 14
Universal Containers (UC) is using a custom application that will act as the Identity Provider and will generate SAML assertions used to log in to Salesforce. UC is considering including custom parameters in the SAML assertion. These attributes contain sensitive data and are needed to authenticate the users. The assertions are submitted to salesforce via a browser form post. The majority of the users will only be able to access Salesforce via UC's corporate network, but a subset of admins and executives would be allowed access from outside the corporate network on their mobile devices. Which two methods should an Architect consider to ensure that the sensitive data cannot be tampered with, nor accessible to anyone while in transit?
- A. Use the Identity Provider's certificate to digitally sign and Salesforce's Certificate to encrypt the payload.
- B. Use Salesforce's Certificate to digitally sign the SAML Assertion and a Mobile Device Management client on the users' mobile devices.
- C. Use the Identity provider's certificate to digitally Sign and the Identity provider's certificate to encrypt the payload.
- D. Use a custom login flow to retrieve sensitive data using an Apex callout without including the attributes in the assertion.
Answer: CD
Explanation:
Using the identity provider’s certificate to digitally sign and encrypt the payload, and using a custom login flow to retrieve sensitive data using an Apex callout without including the attributes in the assertion are two methods that can ensure that the sensitive data cannot be tampered with, nor accessible to anyone while in transit. Option A is not a good choice because using Salesforce’s certificate to encrypt the payload may not work, as Salesforce does not support encrypted SAML assertions. Option B is not a good choice because using Salesforce’s certificate to digitally sign the SAML assertion may not be necessary, as Salesforce does not validate digital signatures on SAML assertions. Also, using a mobile device management client on the users’ mobile devices may not be relevant, as it does not affect how the sensitive data is transmitted between the identity provider and Salesforce.
References: [Single Sign-On Implementation Guide], [Customizing User Authentication with Login Flows]
NEW QUESTION 15
Universal Containers (UC) is building a custom Innovation platform on their Salesforce instance. The Innovation platform will be written completely in Apex and Visualforce and will use custom objects to store the Data. UC would like all users to be able to access the system without having to log in with Salesforce credentials. UC will utilize a third-party idp using SAML SSO. What is the optimal Salesforce licence type for all of the UC employees?
- A. Identity Licence.
- B. Salesforce Licence.
- C. External Identity Licence.
- D. Salesforce Platform Licence.
Answer: D
Explanation:
The optimal Salesforce license type for all of the UC employees who will access the custom Innovation platform without logging in with Salesforce credentials is the Salesforce Platform license. The Salesforce Platform license allows users to access custom applications built on the Lightning Platform, such as Apex and Visualforce, and use standard objects such as accounts, contacts, reports, dashboards, and custom tabs. It also supports SSO with a third-party identity provider using SAML. Option A is not a good choice because the Identity license is designed for users who need to access Salesforce Identity features, such as identity provider, social sign-on, and user provisioning, but not for users who need to access custom applications. Option B is not a good choice because the Salesforce license is designed for users who need full access to standard CRM and Lightning Platform features, such as leads, opportunities, campaigns, forecasts, and contracts, but it may be unnecessary or expensive for users who only need to access custom applications. Option C is not a good choice because the External Identity license is designed for users who are external to the organization, such as customers or partners, but not for users who are internal employees.
References: Salesforce Help: User License Types, [Salesforce Help: Single Sign-On for Desktop and Mobile Applications using SAML and OAuth]
NEW QUESTION 16
After a recent audit, universal containers was advised to implement Two-factor Authentication for all of their critical systems, including salesforce. Which two actions should UC consider to meet this requirement? Choose 2 answers
- A. Require users to provide their RSA token along with their credentials.
- B. Require users to supply their email and phone number, which gets validated.
- C. Require users to enter a second password after the first Authentication
- D. Require users to use a biometric reader as well as their password
Answer: AD
Explanation:
A is correct because requiring users to provide their RSA token along with their credentials is a form of
two-factor authentication. An RSA token is a hardware device that generates a one-time password (OTP) that changes every few seconds. The user needs to enter both their password and the OTP to log in to Salesforce.
D is correct because requiring users to use a biometric reader as well as their password is another form of two-factor authentication. A biometric reader is a device that scans a user’s fingerprint, face, iris, or other physical characteristics to verify their identity. The user needs to provide both their password and their biometric data to log in to Salesforce.
B is incorrect because requiring users to supply their email and phone number, which gets validated, is not a form of two-factor authentication. This is a form of identity verification, which is used to confirm that the user owns the email and phone number they provided. However, this does not add an extra layer of protection beyond their password when they log in to Salesforce.
C is incorrect because requiring users to enter a second password after the first authentication is not a form of two-factor authentication. This is a form of single-factor authentication, which only relies on something the user knows (their passwords). This does not increase security against unauthorized account access.
References: 4: Multi-Factor Authentication - Salesforce 5: Salesforce Multi-Factor Authentication 6: Factor Authentication - Salesforce India 7: Customer 360 | Increase Productivity - Salesforce UK 8: Secu Salesforce Login Using Two-Factor Authentication and Salesforce …
NEW QUESTION 17
Universal Containers (UC) plans to use a SAML-based third-party IdP serving both of the Salesforce Partner Community and the corporate portal. UC partners will log in 65* to the corporate portal to access protected resources, including links to Salesforce resources. What would be the recommended way to configure the IdP so that seamless access can be achieved in this scenario?
- A. Set up the corporate portal as a Connected App in Salesforce and use the Web server OAuth flow.
- B. Configure SP-initiated SSO that passes the SAML token upon Salesforce resource access request.
- C. Set up the corporate portal as a Connected App in Salesforce and use the User Agent OAuth flow.
- D. Configure IdP-initiated SSO that passes the SAML token upon Salesforce resource access request.
Answer: D
Explanation:
The recommended way to configure the IdP for seamless access is to use IdP-initiated SSO that passes the SAML token upon Salesforce resource access request. This means that the user logs in to the corporate portal first, and then clicks a link to access a Salesforce resource. The IdP sends a SAML response to Salesforce with the user’s identity and other attributes. Salesforce verifies the SAML response and logs in the user to the appropriate Salesforce org and community12. This way, the user does not have to log in again to Salesforce or enter any credentials3. References: 1: SAML SSO with Salesforce as the Service Provider 2: Set Up Single Sign-On for Your Internal Users Unit | Salesforce - Trailhead 3: What is IdP-Initiated Single Sign-On? – OneLogin
NEW QUESTION 18
Universal Containers wants to allow its customers to log in to its Experience Cloud via a third-party authentication provider that supports only the OAuth protocol.
What should an identity architect do to fulfill this requirement?
- A. Contact Salesforce Support and enable delegate single sign-on.
- B. Create a custom external authentication provider.
- C. Use certificate-based authentication.
- D. Configure OpenID Connect authentication provider.
Answer: B
Explanation:
If the third-party authentication provider supports only the OAuth protocol and not OpenID Connect, then an identity architect needs to create a custom external authentication provider for it. A custom external authentication provider is a configuration that allows users to log in to Salesforce using an external identity provider that is not predefined by Salesforce. It requires implementing the Auth.AuthProviderPlugin interface and defining the OAuth endpoints and parameters.
References: Custom External Authentication Providers, Create a Custom Authentication Provider
NEW QUESTION 19
......
Thanks for reading the newest Identity-and-Access-Management-Architect exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com Identity-and-Access-Management-Architect dumps in VCE and PDF here: https://www.thedumpscentre.com/Identity-and-Access-Management-Architect-dumps/ (246 Q&As Dumps)
