Our pass rate is high to 98.9% and the similarity percentage between our JN0-230 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Juniper JN0-230 exam in just one try? I am currently studying for the Juniper JN0-230 exam. Latest Juniper JN0-230 Test exam practice questions and answers, Try Juniper JN0-230 Brain Dumps First.
Free JN0-230 Demo Online For Juniper Certifitcation:
NEW QUESTION 1
What must you do first to use the Monitor/Events workspace in the j-Web interface?
- A. You must enable stream mode security logging on the SRX Series device
- B. You must enable event mode security logging on the SRX Series device.
- C. You must enable security logging that uses the SD-Syslog format.
- D. You must enable security logging that uses the TLS transport mode.
Answer: B
NEW QUESTION 2
You want to automatically generate the encryption and authentication keys during IPsec VPN establishment. What would be used to accomplish this task?
- A. IPsec
- B. Diffie_Hellman
- C. Main mode
- D. Aggregate mode
Answer: B
NEW QUESTION 3
Users in your network are downloading files with file extensions that you consider to be unsafe for your network. You must prevent files with specific file extensions from entering your network.
Which UTM feature should be enable on an SRX Series device to accomplish this task?
- A. Content filtering
- B. Web filtering
- C. Antispam
- D. URL filtering
Answer: A
NEW QUESTION 4
Users should not have access to Facebook, however, a recent examination of the logs security show that users are accessing Facebook.
Referring to the exhibit,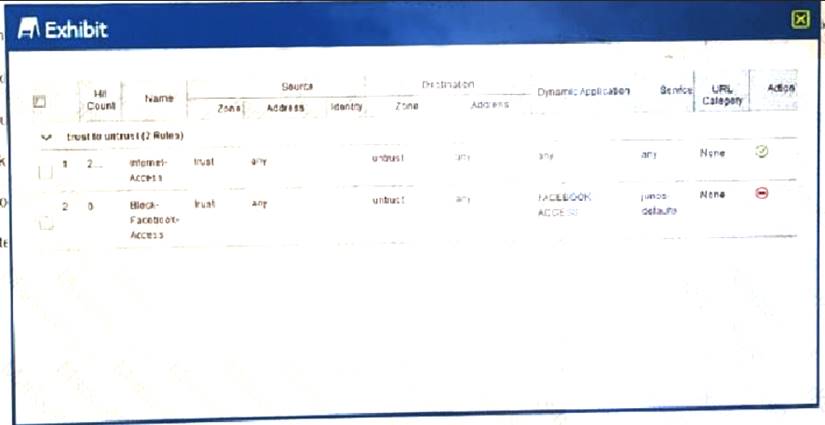
what should you do to solve this problem?
- A. Change the source address for the Block-Facebook-Access rule to the prefix of the users
- B. Move the Block-Facebook-Access rule before the Internet-Access rule
- C. Move the Block-Facebook-Access rule from a zone policy to a global policy
- D. Change the Internet-Access rule from a zone policy to a global policy
Answer: B
NEW QUESTION 5
You want to generate reports from the l-Web on an SRX Series device. Which logging mode would you use in this scenario?
- A. Syslog
- B. Stream
- C. Event
- D. local
Answer: B
NEW QUESTION 6
The Sky ATP premium or basic-Threat Feed license is needed fort which two features? (Choose two.)
- A. Outbound protection
- B. C&C feeds
- C. Executable inspection
- D. Custom feeds
Answer: BD
NEW QUESTION 7
Your company uses SRX Series devices to secure the edge of the network. You are asked protect the company from ransom ware attacks.
Which solution will satisfy this requirement?
- A. Sky ATP
- B. AppSecure
- C. Unified security policies
- D. screens
Answer: A
NEW QUESTION 8
Which two notifications are available when the antivirus engine detects and infected file? (Choose two.)
- A. e-mail notifications
- B. SNMP notifications
- C. SMS notifications
- D. Protocol-only notification
Answer: AD
NEW QUESTION 9
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
- A. With global-based policies, you do not need to specify a destination zone in the match criteria.
- B. With global-based policies, you do not need to specify a source zone in the match criteria.
- C. With global-based policies, you do not need to specify a destination address in the match criteria.
- D. With global-based policies, you do not need to specify a source address in the match criteria.
Answer: AB
NEW QUESTION 10
Which statement is correct about IKE?
- A. IKE phase 1 is used to establish the data path
- B. IKE phase 1 only support aggressive mode.
- C. IKE phase 1 negotiates a secure channel between gateways.
- D. IKE phase 1 establishes the tunnel between devices
Answer: C
NEW QUESTION 11
Which statements is correct about global security policies?
- A. Global policies allow you to regulate traffic with addresses and applications, regardless of their security zones.
- B. Traffic matching global is not added to the session table.
- C. Global policies eliminate the need to assign interface to security zones.
- D. Global security require you to identify a source and destination zone.
Answer: A
NEW QUESTION 12
Which flow module components handles processing for UTM?
- A. Policy
- B. Zones
- C. Services
- D. Screen options
Answer: C
NEW QUESTION 13
Which UTM feature should you use to protect users from visiting certain blacklisted websites?
- A. Content filtering
- B. Web filtering
- C. Antivirus
- D. antispam
Answer: B
NEW QUESTION 14
Which three actions would be performed on traffic traversing an IPsec VPAN? (Choose three.)
- A. Port forwarding
- B. Authentication
- C. Encryption
- D. Deep inspection
- E. Payload verification
Answer: BCE
NEW QUESTION 15
Which two statements are true about security policy actions? (Choose two.)
- A. The reject action drops the traffic and sends a message to the source device.
- B. The deny action silently drop the traffic.
- C. The deny action drops the traffic and sends a message to the source device.
- D. The reject action silently drops the traffic.
Answer: AB
NEW QUESTION 16
A new SRX Series device has been delivered to your location. The device has the factory-default configuration loaded. You have powered on the device and connected to the console port.
What would you use to log into the device to begin the initial configuration?
- A. Root with a password of juniper’’
- B. Root with no password
- C. Admin with password
- D. Admin with a password ‘’juniper’’
Answer: B
NEW QUESTION 17
Which security feature is applied to traffic on an SRX Series device when the device is running n packet mode?
- A. Sky ATP
- B. ALGs
- C. Firewall filters
- D. Unified policies
Answer: C
NEW QUESTION 18
You want to integrate an SRX Series device with SKY ATP. What is the first action to accomplish task?
- A. Issue the commit script to register the SRX Series device.
- B. Copy the operational script from the Sky ATP Web UI.
- C. Create an account with the Sky ATP Web UI.
- D. Create the SSL VPN tunnel between the SRX Series device and Sky ATP.
Answer: C
NEW QUESTION 19
Referring to the exhibit.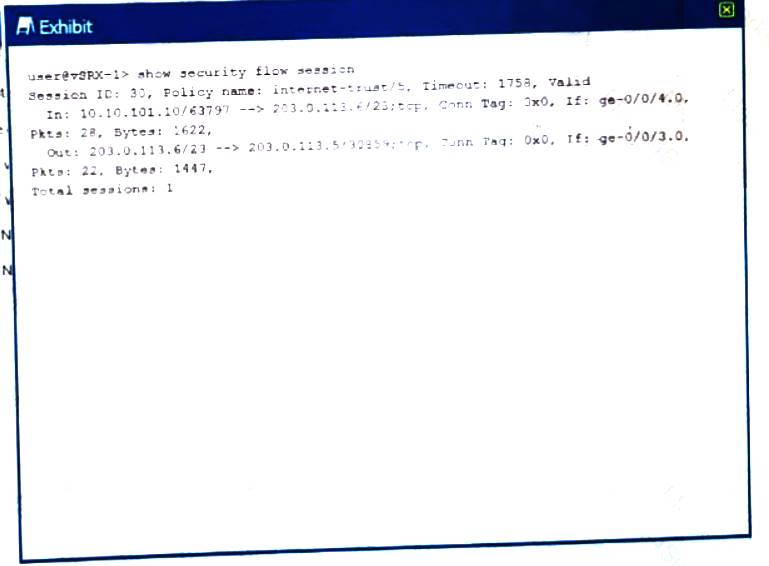
Which type of NAT is being performed?
- A. Source NAT with PAT
- B. Source NAT without PAT
- C. Destination NAT without PAT
- D. Destination NAT with PAT
Answer: A
NEW QUESTION 20
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
- A. Zone processing
- B. Security policy evolution
- C. Service ALG processing
- D. Screens processing
Answer: CD
NEW QUESTION 21
The free licensing model for Sky ATP includes which features? (Choose two.)
- A. C& C feeds
- B. Infected host blocking
- C. Executable file inspection
- D. Compromised endpoint dashboard
Answer: BC
NEW QUESTION 22
Which type of security policy protect restricted services from running on non-standard ports?
- A. Application firewall
- B. IDP
- C. Sky ATP
- D. antivirus
Answer: B
NEW QUESTION 23
......
Recommend!! Get the Full JN0-230 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/JN0-230/ (New 65 Q&As Version)
