We provide real MD-100 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Microsoft MD-100 Exam quickly & easily. The MD-100 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Microsoft MD-100 dumps pdf and vce product and material, you can easily pass the MD-100 exam.
NEW QUESTION 1
You are a network administrator at your company.
A user attempts to start a computer and receives the following error message: “Bootmgr is missing.” You need to resolve the issue.
You start the computer in the recovery mode.
Which command should you run next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.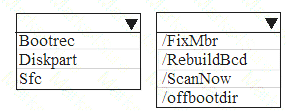
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References: https://neosmart.net/wiki/bootmgr-is-missing/
NEW QUESTION 2
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contain the users shown in the following table.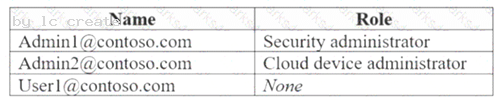
You have a computer named Computer1 that runs Windows 10.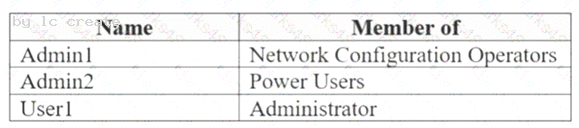
User1 joins Computer1 to Azure AD by using user1@contoso.com.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.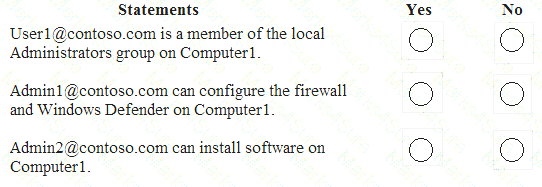
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 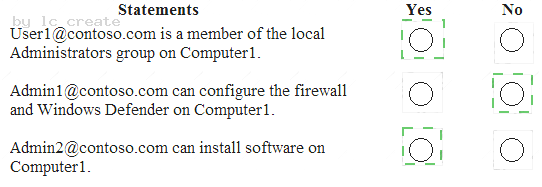
NEW QUESTION 3
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder. Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in
the local Group Policy, you configure Audit directory service access.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
NEW QUESTION 4
You have several computers that run Windows 10. The computers are in a workgroup and have BitLocker Drive Encryption (BitLocker) enabled.
You join the computers to Microsoft Azure Active Directory (Azure AD).
You need to ensure that you can recover the BitLocker recovery key for the computers from Azure AD. What should you do first?
- A. Disable BitLocker.
- B. Add a BitLocker key protector.
- C. Suspend BitLocker.
- D. Disable the TMP chip.
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/prepare-your-organization-f
NEW QUESTION 5
You have a computer named Computer1 that runs Windows 10 and contains the following files:  C:Folder1File1.bat
C:Folder1File1.bat C:Folder1File1.exe
C:Folder1File1.exe  C:Folder1File1.cmd
C:Folder1File1.cmd
A user named User1 is assigned Read & execute to all the files. Computer1 is configured as shown in the exhibit.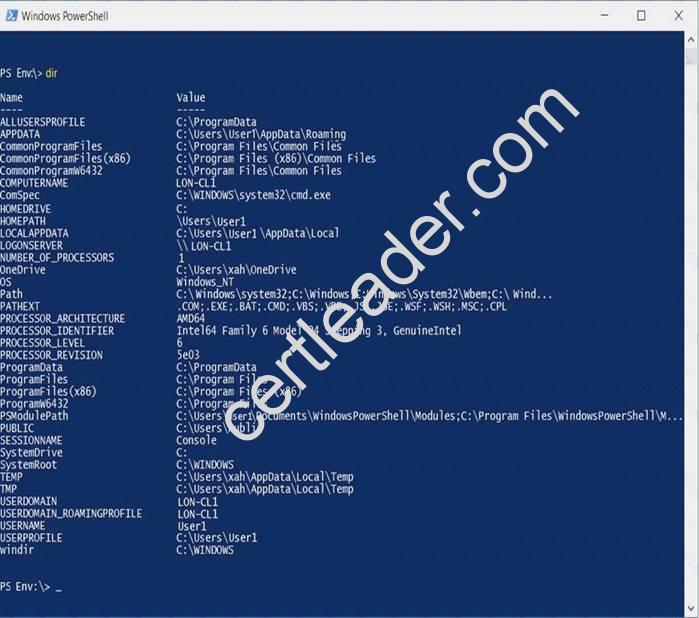
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.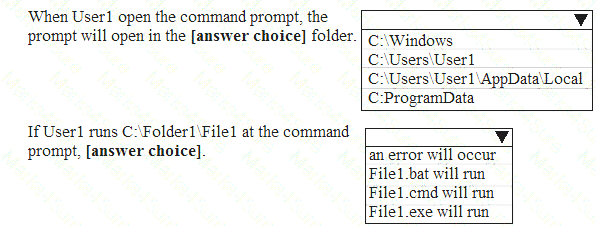
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://stackoverflow.com/questions/148968/windows-batch-files-bat-vs-cmd
NEW QUESTION 6
You need to recommend a solution to configure the employee VPN connections. What should you include in the recommendation?
- A. Remote Access Management Console
- B. Group Policy Management Console (GPMC)
- C. Connection Manager Administration Kit (CMAK)
- D. Microsoft Intune
Answer: D
Explanation:
References:
https://docs.microsoft.com/en-us/windows-server/remote/remote-access/vpn/always-on-vpn/deploy/vpn-deploy-
NEW QUESTION 7
You have a computer that runs Windows 10.
From the Settings app, you view the connection properties shown in the following exhibit.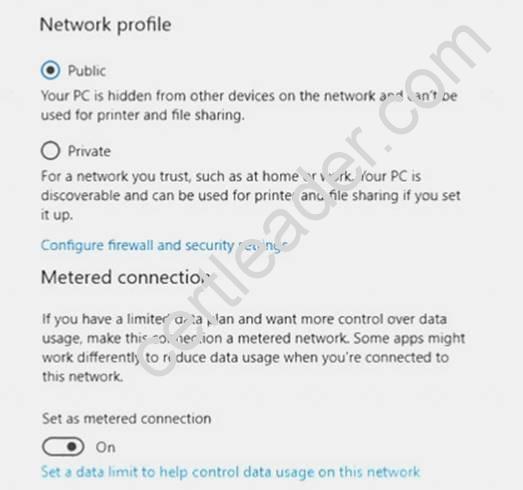
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.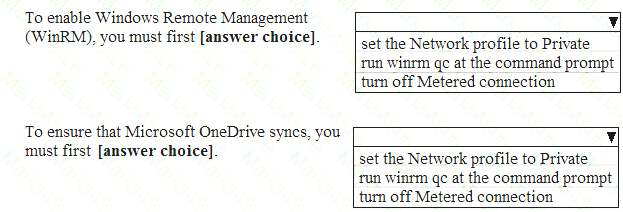
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 8
A user named User1 has a computer named Computer1 that runs Windows 10.
User1 connects to a Microsoft Azure virtual machine named VM1 by using Remote Desktop. User1 creates a VPN connection to a partner organization.
When the VPN connection is established, User1 cannot connect to VM1. When User1 disconnects from the VPN, the user can connect to VM1.
You need to ensure that User1 can connect to VM1 while connected to the VPN. What should you do?
- A. From the proxy settings, add the IP address of VM1 to the bypass list to bypass the proxy.
- B. From the properties of VPN1, clear the Use default gateway on remote network check box.
- C. From the properties of the Remote Desktop connection to VM1, specify a Remote Desktop Gateway (RDGateway).
- D. From the properties of VPN1, configure a static default gateway address.
Answer: B
Explanation:
References:
https://www.stevejenkins.com/blog/2010/01/using-the-local-default-gateway-with-a-windows-vpn-connection/
NEW QUESTION 9
You have several computers that run Windows 10. The computers are in a workgroup. You need to prevent users from using Microsoft Store apps on their computer.
What are two possible ways to achieve the goal? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. From Security Settings in the local Group Policy, configure Security Options.
- B. From Administrative Templates in the local Group Policy, configure the Store settings.
- C. From Security Settings in the local Group Policy, configure Software Restriction Policies.
- D. From Security Settings in the local Group Policy, configure Application Control Policies.
Answer: BD
Explanation:
References:
https://www.techrepublic.com/article/how-to-manage-your-organizations-microsoft-store-group-policy/
NEW QUESTION 10
You have a computer that runs Windows 10.
You discover that Windows updates are failing to install on the computer.
You need to generate a log file that contains detailed information about the failures. Which cmdlet should you run?
- A. Get–LogProperties
- B. Get–WindowsErrorReporting
- C. Get–WindowsUpdateLog
- D. Get–WinEvent
Answer: C
Explanation:
References:
https://docs.microsoft.com/en-us/powershell/module/windowsupdate/get-windowsupdatelog?view=win10-ps
NEW QUESTION 11
You need to ensure that User10 can activate Computer10. What should you do?
- A. Request that a Windows 10 Enterprise license be assigned to User10, and then activate Computer10.
- B. From the Microsoft Deployment Toolkit (MDT), add a Volume License Key to a task sequence, and thenredeploy Computer10.
- C. From System Properties on Computer10, enter a Volume License Key, and then activate Computer10.
- D. Request that User10 perform a local AutoPilot Reset on Computer10, and then activate Computer10.
Answer: D
Explanation:
References:
https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/windows-autopilot-requirements-lice
NEW QUESTION 12
You have 100 computers that run Windows 10. The computers are in a workgroup. The computers have a low-bandwidth metered Internet connection.
You need to reduce the amount of Internet bandwidth consumed to download updates. What should you configure?
- A. BranchCache in hosted mode
- B. BranchCache in distributed cache mode
- C. Delivery Optimization
- D. Background intelligent Transfer Service (BITS)
Answer: C
Explanation:
References:
https://support.microsoft.com/en-us/help/4468254/windows-update-delivery-optimization-faq
NEW QUESTION 13
You have 200 computers that run Windows 10 and are joined to an Active Directory domain.
You need to enable Windows Remote Management (WinRM) on all the computers by using Group Policy. Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Set the Startup Type of the Windows Remote Management (WS-Management) service to Automatic.
- B. Enable the Windows Firewall: Allow inbound remote administration exception setting.
- C. Enable the Allow remote server management through WinRM setting.
- D. Enable the Windows Firewall: Allow inbound Remote Desktop exceptions setting.
- E. Enable the Allow Remote Shell access setting.
- F. Set the Startup Type of the Remote Registry service to Automatic.
Answer: ACD
Explanation:
References:
http://www.mustbegeek.com/how-to-enable-winrm-via-group-policy/
NEW QUESTION 14
Your network contains an Active Directory domain. The domain contains a user named Admin1. All computers run Windows 10.
You enable Windows PowerShell remoting on the computers.
You need to ensure that Admin1 can establish remote PowerShell connections to the computers. The solution must use the principle of least privilege.
To which group should you add Admin1?
- A. Access Control Assistance Operators
- B. Power Users
- C. Remote Desktop Users
- D. Remote Management Users
Answer: D
Explanation:
References:
https://4sysops.com/wiki/enable-powershell-remoting/
NEW QUESTION 15
You plan to deploy Windows 10 to 100 secure computers.
You need to select a version of Windows 10 that meets the following requirements:  Uses Microsoft Edge as the default browser
Uses Microsoft Edge as the default browser Minimizes the attack surface on the computer
Minimizes the attack surface on the computer Supports joining Microsoft Azure Active Directory (Azure AD)
Supports joining Microsoft Azure Active Directory (Azure AD) Only allows the installation of applications from the Microsoft Store
Only allows the installation of applications from the Microsoft Store
What is the best version to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- A. Windows 10 Pro in S mode
- B. Windows 10 Home in S mode
- C. Windows 10 Pro
- D. Windows 10 Enterprise
Answer: C
Explanation:
References:
https://www.microsoft.com/en-za/windows/compare
NEW QUESTION 16
ComputerA connects to a manufacturing system and is business critical. All the other computers are joined to the domain and run the Semi-Annual Channel version of Windows 10.
In the domain, you create four groups named Group1, Group2, Group3, and Group4. Computer2 has the local Group Policy settings shown in the following table.
The computers are updated by using Windows Update for Business. The domain has the users shown in the following table.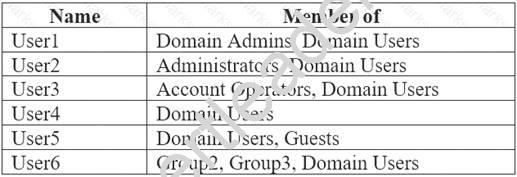
Computer1 has the local users shown in the following table.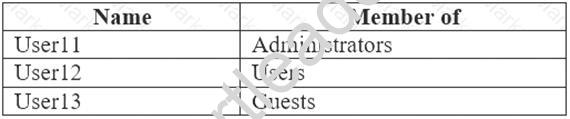
Requirements Planned Changes
Contoso plans to purchase computers preinstalled with Windows 10 Pro for all the San Diego office users.
Technical requirements
Contoso identifies the following technical requirements: The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA). Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers.
Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers. Users in the HR department must be able to view the list of files in a folder named D:Reports on Computer3.
Users in the HR department must be able to view the list of files in a folder named D:Reports on Computer3. ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.
ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.  Quality update installations must be deferred as long as possible on ComputerA.
Quality update installations must be deferred as long as possible on ComputerA. Users in the IT department must use dynamic look on their primary device.
Users in the IT department must use dynamic look on their primary device.  User6 must be able to connect to Computer2 by using Remote Desktop.
User6 must be able to connect to Computer2 by using Remote Desktop. The principle of least privilege must be used whenever possible.
The principle of least privilege must be used whenever possible. Administrative effort must be minimized whenever possible.
Administrative effort must be minimized whenever possible.  Assigned access must be configured on Computer1.
Assigned access must be configured on Computer1.
6.
You need to meet the technical requirements for EFS on ComputerA. What should you do?
- A. Run certutil.exe, and then add a certificate to the local computer certificate store.
- B. Run cipher.exe, and then add a certificate to the local computer certificate store.
- C. Run cipher.exe, and then add a certificate to the local Group Policy.
- D. Run certutil.exe, and then add a certificate to the local Group Policy.
Answer: B
Explanation:
References:
https://www.online-tech-tips.com/computer-tips/set-file-folder-permissions-windows/
9. - (Exam Topic 2)
You need to meet the technical requirements for the helpdesk users.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.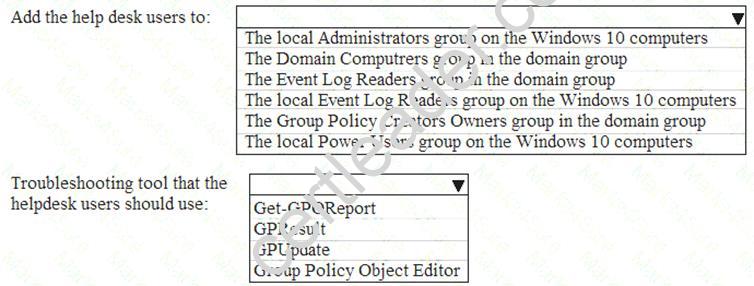
Answer: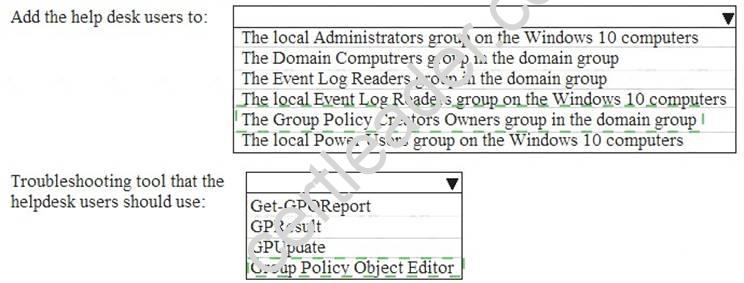
10. - (Exam Topic 2)
You need to meet the technical requirement for User6. What should you do?
A. Add User6 to the Remote Desktop Users group in the domain.
B. Remove User6 from Group2 in the domain.
C. Add User6 to the Remote Desktop Users group on Computer2.
D. And User6 to the Administrators group on Computer2.
Answer: B
NEW QUESTION 17
You have a computer named Computer1 that runs Windows 7. Computer1 has a local user named User1 who has a customized profile.
On Computer1, you perform a clean installation of Windows 10 without formatting the drives. You need to migrate the settings of User1 from Windows7 to Windows 10.
Which two actions should you perform? To answer, drag the appropriate actions to the correct targets. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.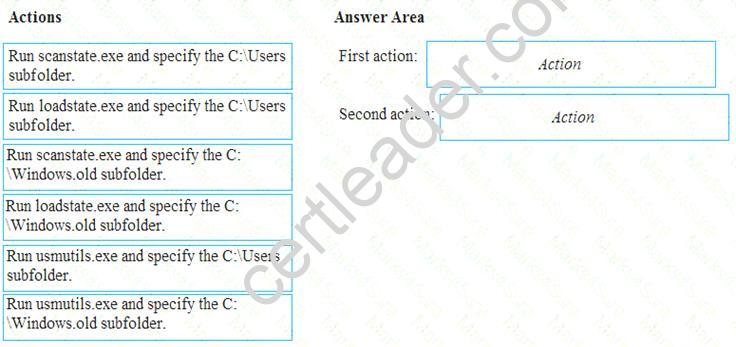
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/windows/deployment/usmt/usmt-how-it-works
NEW QUESTION 18
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from Audit Policy in the local Group Policy, you configure Audit object access.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation:
References:
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
NEW QUESTION 19
You have three computers that run Windows 10 as shown in the following table.
All the computers have C and D volumes. The Require additional authentication at startup Group Policy settings is disabled on all the computers.
Which volumes can you encrypt by using BitLocker Drive Encryption (BitLocker)? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.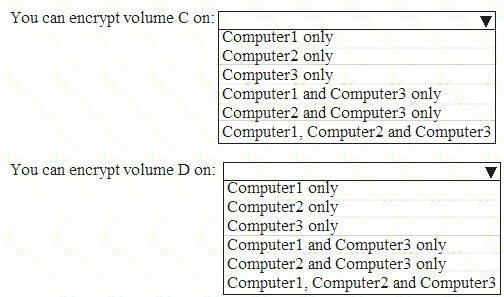
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://www.windowscentral.com/how-use-bitlocker-encryption-windows-10
NEW QUESTION 20
You need to meet the technical requirement for the IT department users. What should you do first?
- A. Issue computer certificates
- B. Distribute USB keys to the IT department users.
- C. Enable screen saver and configure a timeout.
- D. Turn on Bluetooth.
Answer: D
Explanation:
References:
https://support.microsoft.com/en-za/help/4028111/windows-lock-your-windows-10-pc-automatically-when-you-
NEW QUESTION 21
Your company has an isolated network used for testing. The network contains 20 computers that run Windows 10. The computers are in a workgroup. During testing, the computers must remain in the workgroup.
You discover that none of the computers are activated.
You need to recommend a solution to activate the computers without connecting the network to the Internet. What should you include in the recommendation?
- A. Volume Activation Management Tool (VAMT)
- B. Key Management Service (KMS)
- C. Active Directory-based activation
- D. the Get-WindowsDeveloperLicense cmdlet
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/windows/deployment/volume-activation/activate-using-key-management-servi
NEW QUESTION 22
You have a computer that runs Windows 10. The computer is in a workgroup. The computer is used to provide visitors with access to the Internet.
You need to configure the computer to meet the following requirements:  Always sign in automatically as User1.
Always sign in automatically as User1. Start an application named App1.exe at sign-in.
Start an application named App1.exe at sign-in.
What should you use to meet each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.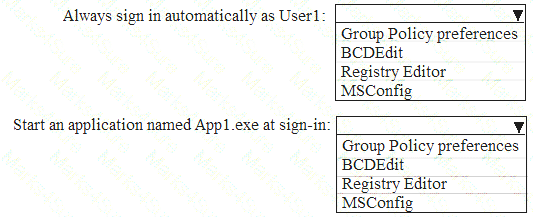
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
http://www.itexpertmag.com/server/complete-manageability-at-no-extra-cost
NEW QUESTION 23
Your company has a wireless access point that uses WPA2-Enterprise. You need to configure a computer to connect to the wireless access point. What should you do first?
- A. Create a provisioning package in Windows Configuration Designer.
- B. Request a passphrase.
- C. Request and install a certificate.
- D. Create a Connection Manager Administration Kit (CMAK) package.
Answer: B
Explanation:
References:
https://support.microsoft.com/en-za/help/17137/windows-setting-up-wireless-network
NEW QUESTION 24
You have 15 computers that run Windows 10. Each computer has two network interfaces named Interface1 and Interface2.
You need to ensure that network traffic uses Interface1, unless Interface1 is unavailable. What should you do?
- A. Run the Set-NetIPInterface –InterfaceAlias Interface1 –InterfaceMetric 1 command.
- B. Run the Set-NetAdapterBinding –Name Interface2 –Enabled $true –ComponentID ms_tcpip – ThrottleLimit 0 command.
- C. Set a static IP address on Interface 1.
- D. From Network Connections in Control Pane, modify the Provider Order.
Answer: A
Explanation:
References:
https://tradingtechnologies.atlassian.net/wiki/spaces/KB/pages/27439127/How+to+Change+Network+Adapter+ https://docs.microsoft.com/en-us/powershell/module/nettcpip/set-netipinterface?view=win10-ps
NEW QUESTION 25
......
P.S. Easily pass MD-100 Exam with 83 Q&As DumpSolutions Dumps & pdf Version, Welcome to Download the Newest DumpSolutions MD-100 Dumps: https://www.dumpsolutions.com/MD-100-dumps/ (83 New Questions)
