Exam Code: NSE4_FGT-6.0 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Fortinet NSE 4 – FortiOS 6.0
Certification Provider: Fortinet
Free Today! Guaranteed Training- Pass NSE4_FGT-6.0 Exam.
Online Fortinet NSE4_FGT-6.0 free dumps demo Below:
NEW QUESTION 1
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A. Traffic to botnet servers
- B. Traffic to inappropriate web sites
- C. Server information disclosure attacks
- D. Credit card data leaks
- E. SQL injection attacks
Answer: ACE
NEW QUESTION 2
An administrator needs to strengthen the security for SSL VPN access. Which of the following statements are best practices to do so? (Choose three.)
- A. Configure split tunneling for content inspection.
- B. Configure host restrictions by IP or MAC address.
- C. Configure two-factor authentication using security certificates.
- D. Configure SSL offloading to a content processor (FortiASIC).
- E. Configure a client integrity check (host-check).
Answer: CDE
NEW QUESTION 3
An administrator has configured central DNAT and virtual IPs. Which of the following can be selected in the firewall policy Destination field?
- A. A VIP group
- B. The mapped IP address object of the VIP object
- C. A VIP object
- D. An IP pool
Answer: C
NEW QUESTION 4
Examine this FortiGate configuration: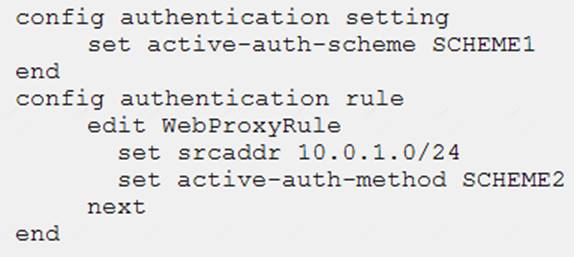
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- A. It always authorizes the traffic without requiring authentication.
- B. It drops the traffic.
- C. It authenticates the traffic using the authentication scheme SCHEME2.
- D. It authenticates the traffic using the authentication scheme SCHEME1.
Answer: C
NEW QUESTION 5
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not provide any data integrity or encryption.
- B. AH does not support perfect forward secrecy.
- C. AH provides data integrity but no encryption.
- D. AH provides strong data integrity but weak encryption.
Answer: C
NEW QUESTION 6
Which of the following services can be inspected by the DLP profile? (Choose three.)
- A. NFS
- B. FTP
- C. IMAP
- D. CIFS
- E. HTTP-POST
Answer: BCE
NEW QUESTION 7
An administrator wants to configure a FortiGate as a DNS server FortiGate must use us DNS database first, and then relay all irresolvable queries to an external DNS server. Which of the following DNS method must you UM?
- A. Recursive
- B. Non-recursive
- C. Forward to primary and secondary DNS
- D. Forward to system DNS
Answer: A
NEW QUESTION 8
An administrator is configuring an IPsec between site A and site B. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.16.1.0/24 and the remote quick mode selector is 192.16.2.0/24. How must the administrator configure the local quick mode selector for site B?
- A. 192.168.3.0.24
- B. 192.168.2.0.24
- C. 192.168.1.0.24
- D. 192.168.0.0.8
Answer: A
NEW QUESTION 9
When override is enabled, which of the following shows the process and selection criteria that are used to elect the primary FortiGate in an HA cluster?
- A. Connected monitored ports > HA uptime > priority > serial number
- B. Priority > Connected monitored ports > HA uptime > serial number
- C. Connected monitored ports > priority > HA uptime > serial number
- D. HA uptime > priority > Connected monitored ports > serial number
Answer: C
NEW QUESTION 10
Examine this output from a debug flow: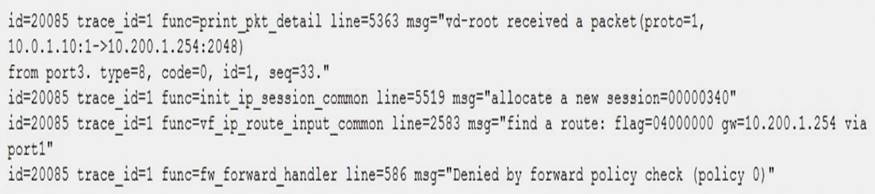
Why did the FortiGate drop the packet?
- A. The next-hop IP address is unreachable.
- B. It failed the RPF check.
- C. It matched an explicitly configured firewall policy with the action DENY.
- D. It matched the default implicit firewall policy.
Answer: D
NEW QUESTION 11
An administrator is running the following sniffer command:
diagnose sniffer packet any “host 10.0.2.10” 3
What information will be included in the sniffer output? (Choose three.)
- A. IP header
- B. Ethernet header
- C. Packet payload
- D. Application header
- E. Interface name
Answer: ABC
NEW QUESTION 12
What information is flushed when the chunk-size value is changed in the config dlp settings?
- A. The database for DLP document fingerprinting
- B. The supported file types in the DLP filters
- C. The archived files and messages
- D. The file name patterns in the DLP filters
Answer: A
NEW QUESTION 13
What settings must you configure to ensure FortiGate generates logs for web filter activity on a firewall policy called Full Access? (Choose two.)
- A. Enable Event Logging.
- B. Enable a web filter security profile on the Full Access firewall policy.
- C. Enable Log Allowed Traffic on the Full Access firewall policy.
- D. Enable disk logging.
Answer: BC
NEW QUESTION 14
If traffic matches a DLP filter with the action set to Quarantine IP Address, what action does FortiGate take?
- A. It notifies the administrator by sending an email.
- B. It provides a DLP block replacement page with a link to download the file.
- C. It blocks all future traffic for that IP address for a configured interval.
- D. It archives the data for that IP address.
Answer: C
NEW QUESTION 15
View the exhibit.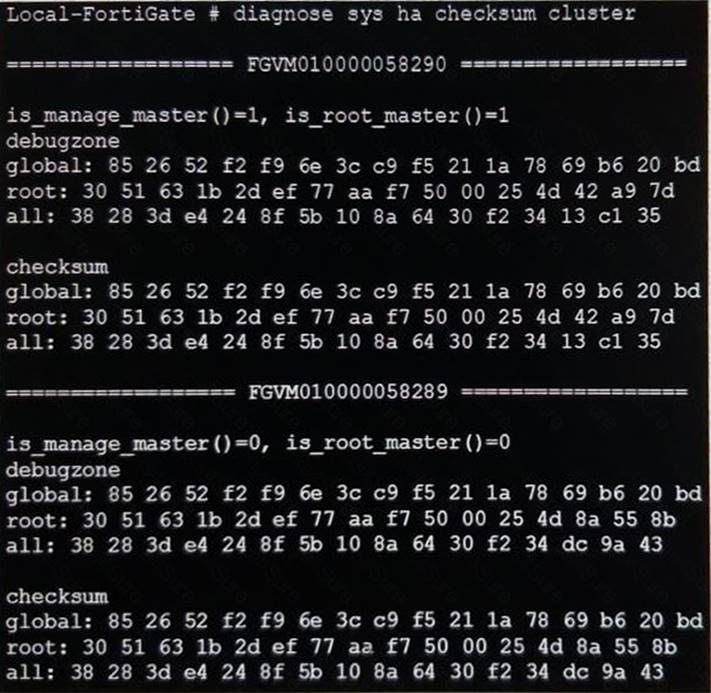
Based on this output, which statements are correct? (Choose two.)
- A. The all VDOM is not synchronized between the primary and secondary FortiGate devices.
- B. The root VDOM is not synchronized between the primary and secondary FortiGate devices.
- C. The global configuration is synchronized between the primary and secondary FortiGate devices.
- D. The FortiGate devices have three VDOMs.
Answer: CD
NEW QUESTION 16
The FSSO Collector Agent set to advanced access mode for the Windows Active Directory uses which of the following?
- A. LDAP convention
- B. NTLM convention
- C. Windows convention - NetBios: DomainUsemame
- D. RSSO convention
Answer: C
NEW QUESTION 17
View the exhibit.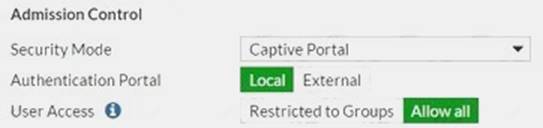
Which users and user groups are allowed access to the network through captive portal?
- A. Users and groups defined in the firewall policy.
- B. Only individual users – not groups – defined in the captive portal configuration
- C. Groups defined in the captive portal configuration
- D. All users
Answer: C
NEW QUESTION 18
Examine the exhibit, which shows the partial output of an IKE real-time debug.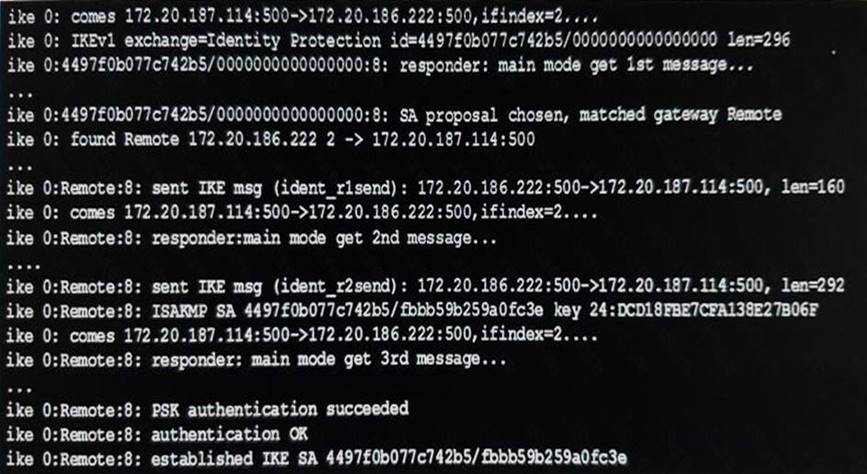
Which of the following statement about the output is true?
- A. The VPN is configured to use pre-shared key authentication.
- B. Extended authentication (XAuth) was successful.
- C. Remote is the host name of the remote IPsec peer.
- D. Phase 1 went down.
Answer: A
NEW QUESTION 19
View the exhibit: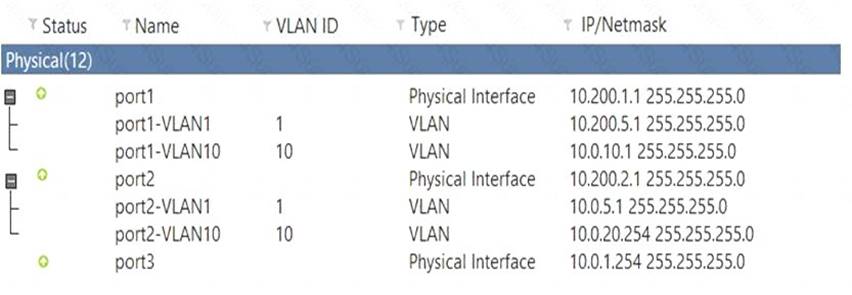
Which statement about the exhibit is true? (Choose two.)
- A. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- B. port-VLAN1 is the native VLAN for the port1 physical interface.
- C. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- D. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Answer: CD
NEW QUESTION 20
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
- A. The firmware image must be manually uploaded to each FortiGate.
- B. Only secondary FortiGate devices are rebooted.
- C. Uninterruptable upgrade is enabled by default.
- D. Traffic load balancing is temporally disabled while upgrading the firmware.
Answer: BD
NEW QUESTION 21
During the digital verification process, comparing the original and fresh hash results satisfies which security requirement?
- A. Authentication.
- B. Data integrity.
- C. Non-repudiation.
- D. Signature verification.
Answer: D
NEW QUESTION 22
Which of the following statements about central NAT are true? (Choose two.)
- A. IP tool references must be removed from existing firewall policies before enabling central NAT.
- B. Central NAT can be enabled or disabled from the CLI only.
- C. Source NAT, using central NAT, requires at least one central SNAT policy.
- D. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall policy.
Answer: AB
NEW QUESTION 23
Which is the correct description of a hash result as it relates to digital certificates?
- A. A unique value used to verify the input data
- B. An output value that is used to identify the person or deuce that authored the input data.
- C. An obfuscation used to mask the input data.
- D. An encrypted output value used to safe-guard die input data
Answer: A
NEW QUESTION 24
On a FortiGate with a hard disk, how can you upload logs to FortiAnalyzer or FortiManager? (Choose two.)
- A. hourly
- B. real tune
- C. on-demand
- D. store-and-upload
Answer: BD
NEW QUESTION 25
......
Thanks for reading the newest NSE4_FGT-6.0 exam dumps! We recommend you to try the PREMIUM Certstest NSE4_FGT-6.0 dumps in VCE and PDF here: https://www.certstest.com/dumps/NSE4_FGT-6.0/ (126 Q&As Dumps)
