Your success in Paloalto-Networks PCCSA is our sole target and we develop all our PCCSA braindumps in a way that facilitates the attainment of this target. Not only is our PCCSA study material the best you can find, it is also the most detailed and the most updated. PCCSA Practice Exams for Paloalto-Networks PCCSA are written to the highest standards of technical accuracy.
Free PCCSA Demo Online For Paloalto-Networks Certifitcation:
NEW QUESTION 1
Which security principle describes the practice of giving users the minimum rights to access the resources necessary to do their jobs?
- A. known privilege
- B. least privilege
- C. user privilege
- D. lowest privilege
Answer: B
NEW QUESTION 2
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
- A. deploy a firewall with content filtering capabilities on the corporate perimeter
- B. allow only encrypted HTTPS access to the internet
- C. configure digital certificates for all users to authenticate internet downloads
- D. permit web connections only to TCP port 443
Answer: A
NEW QUESTION 3
Which mobile device management feature prevents jailbreaking or rooting?
- A. software distribution
- B. malware protection
- C. policy enforcement
- D. data loss prevention
Answer: C
NEW QUESTION 4
When a company chooses to deploy a branch location with antivirus software, which risk model are they using to manage risk?
- A. limiting
- B. assuming
- C. trasnferring
- D. avoiding
Answer: A
NEW QUESTION 5
What is an example of a distance-vector routing protocol?
- A. OSPF
- B. BGP
- C. RIP
- D. IGRP
Answer: C
NEW QUESTION 6
Match each type of breach to its consequence.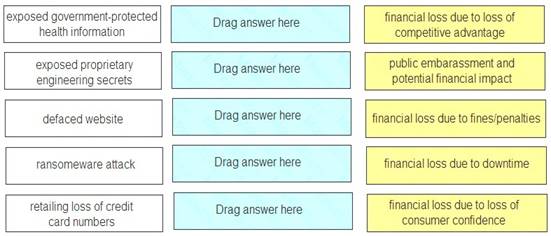
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Exposed government-protected health information – financial loss due to fines/penalties Exposed proprietary engineering secrets – financial loss due to loss of competitive advantage Defaced website – public embarrassment and potential financial impact
Ransomware attack – financial loss due to downtime
Retailing loss of credit card numbers – financial loss due to consumer confidence
NEW QUESTION 7
Which data security compliance standard is used to protect card holder data wherever it is processed, stored, or transmitted?
- A. Property Card Industry
- B. Payment Card Industry
- C. Personal Card Industry
- D. Payment Club Industry
Answer: B
NEW QUESTION 8
Match the tool to its capability.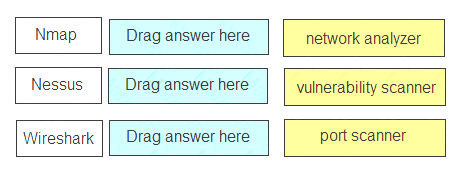
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Nmap – port scanner
Nessus – vulnerability scanner Wireshark – network analyzer
NEW QUESTION 9
Match the Palo Alto Networks Wild Fire analysis verdict with its definition.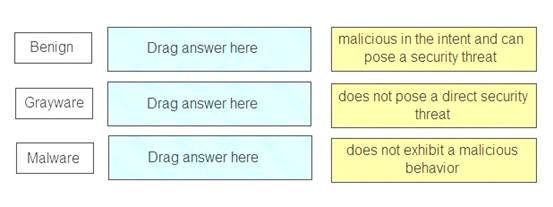
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Benign – does not exhibit a malicious behavior Grayware – does not pose a direct security threat
Malware – malicious in the intent and can pose a security threat References:
NEW QUESTION 10
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social networking application. This type of software code belongs to which type of malware category?
- A. social engineering
- B. virus
- C. pharming
- D. exploit
Answer: D
NEW QUESTION 11
What are two methods to securely transmit personally identifiable information? (Choose two.)
- A. data checksumming
- B. data fragmentation
- C. data encryption
- D. encrypted tunnels
Answer: CD
NEW QUESTION 12
From which resource can a Palo Alto Networks firewall get URL category information for URLs whose categories cannot be found on the firewall?
- A. App-ID database
- B. WildFire
- C. PDF file
- D. PAN-DB database
Answer: D
NEW QUESTION 13
Assume that it is your responsibility to secure the software functioning at all layers in the exhibit. Which cloud service model type is represented?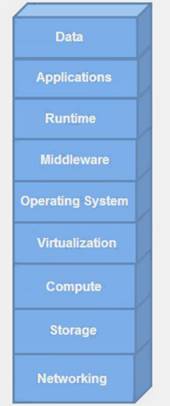
- A. software as a service
- B. platform as a service
- C. infrastructure as a service
- D. on-premises
Answer: D
NEW QUESTION 14
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
- A. state-sponsored
- B. hacktivist
- C. gray hat
- D. white hat
Answer: A
NEW QUESTION 15
What does a hypervisor enable?
- A. high-speed searching of already aggregated security log files
- B. high-speed aggregation and viewing of security log files
- C. multiple physical machines to be configured into a high-performance cluster
- D. multiple guest operating systems to run on a single physical machine
Answer: D
NEW QUESTION 16
Which type of attack floods a target with TCP SYN requests?
- A. route table poisoning
- B. reconaissance
- C. denial-of-service
- D. IP spoofing
Answer: C
NEW QUESTION 17
......
Thanks for reading the newest PCCSA exam dumps! We recommend you to try the PREMIUM Allfreedumps.com PCCSA dumps in VCE and PDF here: https://www.allfreedumps.com/PCCSA-dumps.html (50 Q&As Dumps)
