we provide High value Paloalto-Networks PCNSA free question which are the best for clearing PCNSA test, and to get certified by Paloalto-Networks Palo Alto Networks Certified Network Security Administrator. The PCNSA Questions & Answers covers all the knowledge points of the real PCNSA exam. Crack your Paloalto-Networks PCNSA Exam with latest dumps, guaranteed!
Online Paloalto-Networks PCNSA free dumps demo Below:
NEW QUESTION 1
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?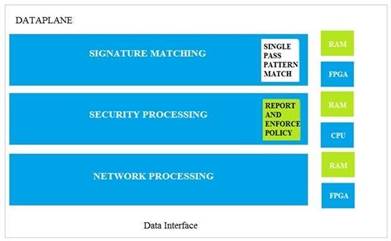
- A. Signature Matching
- B. Network Processing
- C. Security Processing
- D. Security Matching
Answer: A
NEW QUESTION 2
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
- A. 2-3-4-1
- B. 1-4-3-2
- C. 3-1-2-4
- D. 1-3-2-4
Answer: D
NEW QUESTION 3
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?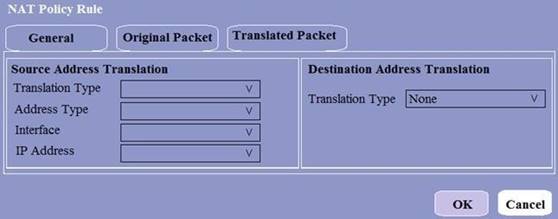
- A. Translation Type
- B. Interface
- C. Address Type
- D. IP Address
Answer: A
NEW QUESTION 4
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base. On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days. Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
- A. All traffic matching the SuperApp_chat, and SuperApp_download is denied because it no longer matches the SuperApp-base application
- B. No impact because the apps were automatically downloaded and installed
- C. No impact because the firewall automatically adds the rules to the App-ID interface
- D. All traffic matching the SuperApp_base, SuperApp_chat, and SuperApp_download is denied until the security administrator approves the applications
Answer: C
NEW QUESTION 5
Which administrator type utilizes predefined roles for a local administrator account?
- A. Superuser
- B. Role-based
- C. Dynamic
- D. Device administrator
Answer: C
NEW QUESTION 6
Which statement is true regarding a Prevention Posture Assessment?
- A. The Security Policy Adoption Heatmap component filters the information by device groups, serial numbers, zones, areas of architecture, and other categories
- B. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
- C. It provides a percentage of adoption for each assessment area
- D. It performs over 200 security checks on Panorama/firewall for the assessment
Answer: B
NEW QUESTION 7
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
- A. control
- B. network processing
- C. data
- D. security processing
Answer: A
NEW QUESTION 8
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
- A. Root
- B. Dynamic
- C. Role-based
- D. Superuser
Answer: C
NEW QUESTION 9
Based on the security policy rules shown, ssh will be allowed on which port?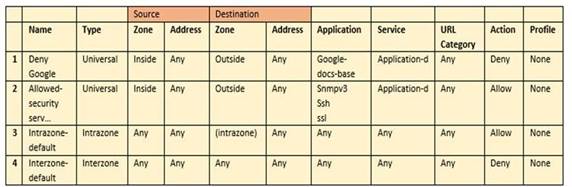
- A. 80
- B. 53
- C. 22
- D. 23
Answer: C
NEW QUESTION 10
Which file is used to save the running configuration with a Palo Alto Networks firewall?
- A. running-config.xml
- B. run-config.xml
- C. running-configuration.xml
- D. run-configuratin.xml
Answer: A
NEW QUESTION 11
In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email?
- A. Weaponization
- B. Reconnaissance
- C. Installation
- D. Command and Control
- E. Exploitation
Answer: A
NEW QUESTION 12
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.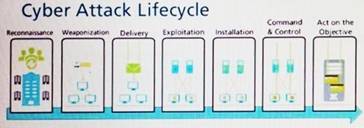
- A. Exploitation
- B. Installation
- C. Reconnaissance
- D. Act on Objective
Answer: A
NEW QUESTION 13
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?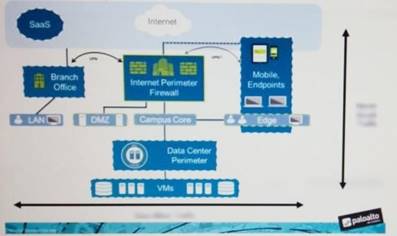
- A. branch office traffic
- B. north-south traffic
- C. perimeter traffic
- D. east-west traffic
Answer: D
NEW QUESTION 14
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
- A. Rule Usage Filter > No App Specified
- B. Rule Usage Filter >Hit Count > Unused in 30 days
- C. Rule Usage Filter > Unused Apps
- D. Rule Usage Filter > Hit Count > Unused in 90 days
Answer: D
NEW QUESTION 15
Which interface does not require a MAC or IP address?
- A. Virtual Wire
- B. Layer3
- C. Layer2
- D. Loopback
Answer: A
NEW QUESTION 16
Which two statements are correct about App-ID content updates? (Choose two.)
- A. Updated application content may change how security policy rules are enforced
- B. After an application content update, new applications must be manually classified prior to use
- C. Existing security policy rules are not affected by application content updates
- D. After an application content update, new applications are automatically identified and classified
Answer: CD
NEW QUESTION 17
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping. What is the quickest way to reset the hit counter to zero in all the security policy rules?
- A. At the CLI enter the command reset rules and press Enter
- B. Highlight a rule and use the Reset Rule Hit Counter > Selected Rules for each rule
- C. Reboot the firewall
- D. Use the Reset Rule Hit Counter > All Rules option
Answer: D
NEW QUESTION 18
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
- A. Layer 2
- B. Tap
- C. Layer 3
- D. Virtual Wire
Answer: B
NEW QUESTION 19
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
- A. Create an anti-spyware profile and enable DNS Sinkhole
- B. Create an antivirus profile and enable DNS Sinkhole
- C. Create a URL filtering profile and block the DNS Sinkhole category
- D. Create a security policy and enable DNS Sinkhole
Answer: A
NEW QUESTION 20
Which statement is true regarding a Best Practice Assessment?
- A. The BPA tool can be run only on firewalls
- B. It provides a percentage of adoption for each assessment data
- C. The assessment, guided by an experienced sales engineer, helps determine the areas of greatest risk where you should focus prevention activities
- D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full PCNSA dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/PCNSA-dumps/ (New 115 Q&As Version)
