Passleader PCNSE Questions are updated and all PCNSE answers are verified by experts. Once you have completely prepared with our PCNSE exam prep kits you will be ready for the real PCNSE exam without a problem. We have Leading Paloalto-Networks PCNSE dumps study guide. PASSED PCNSE First attempt! Here What I Did.
Free demo questions for Paloalto-Networks PCNSE Exam Dumps Below:
NEW QUESTION 1
Refer to the exhibit.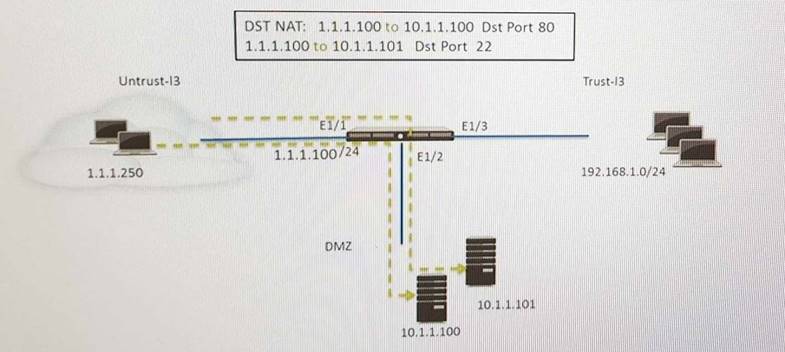
An administrator is using DNAT to map two servers to a single public IP address. Traffic will be
steered to the specific server based on the application, where Host A (10.1.1.100) received HTTP traffic and host B(10.1.1.101) receives SSH traffic.
Which two security policy rules will accomplish this configuration? (Choose two)
- A. Untrust (Any) to Untrust (10.1.1.1) Ssh-Allow
- B. Untrust (Any) to DMZ (1.1.1.100) Ssh-Allow
- C. Untrust (Any) to DMZ (1.1.1.100) Web-browsing -Allow
- D. Untrust (Any) to Untrust (10.1.1.1) Web-browsing -Allow
Answer: CD
NEW QUESTION 2
Which prerequisite must be satisfied before creating an SSH proxy Decryption policy?
- A. Both SSH keys and SSL certificates must be generated.
- B. No prerequisites are required.
- C. SSH keys must be manually generated.
- D. SSL certificates must be generated.
Answer: B
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/decryption/configure-ssh-proxy
NEW QUESTION 3
In a virtual router, which object contains all potential routes?
- A. MIB
- B. RIB
- C. SIP
- D. FIB
Answer: B
Explanation:
Reference: https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=10&ved=0ahUKEwiOkbfYzPzXAhVnEJoKHcwVCg4QFghiMAk&url=https%3A%2F%2Flive.paloaltonetworks.com%2Ftwzvq79624%2Fattachments%2Ftwzvq79624%2Fdocumentation_tkb%2F487%2F1%2FRoute%2520Redistribution%2520and%2520Filtering%2520TechNote%2520-%2520Rev% 2520B. pdf&usg=AOvVaw0H9qgaJK0oI2xjIJBNo1Km
NEW QUESTION 4
A distributed log collection deployment has dedicated log Collectors. A developer needs a device to send logs to Panorama instead of sending logs to the Collector Group.
What should be done first?
- A. Remove the cable from the management interface, reload the log Collector and then re-connect that cable
- B. Contact Palo Alto Networks Support team to enter kernel mode commands to allow adjustments
- C. remove the device from the Collector Group
- D. Revert to a previous configuration
Answer: C
NEW QUESTION 5
Which Zone Pair and Rule Type will allow a successful connection for a user on the internet zone to a web server hosted in the DMZ zone? The web server is reachable using a destination Nat policy in the Palo Alto Networks firewall.
- A. Zone Pair:Source Zone: Internet Destination Zone: DMZ Rule Type:“intrazone”
- B. Zone Pair:Source Zone: Internet Destination Zone: DMZ Rule Type:“intrazone” or “universal”
- C. Zone Pair:Source Zone: Internet Destination Zone: Internet Rule Type:“intrazone” or “universal”
- D. Zone Pair:Source Zone: Internet Destination Zone: Internet Rule Type:“intrazone”
Answer: B
NEW QUESTION 6
SAML SLO is supported for which two firewall features? (Choose two.)
- A. GlobalProtect Portal
- B. CaptivePortal
- C. WebUI
- D. CLI
Answer: AB
NEW QUESTION 7
To connect the Palo Alto Networks firewall to AutoFocus, which setting must be enabled?
- A. Device>Setup>Services>AutoFocus
- B. Device> Setup>Management >AutoFocus
- C. AutoFocus is enabled by default on the Palo Alto Networks NGFW
- D. Device>Setup>WildFire>AutoFocus
- E. Device>Setup> Management> Logging and Reporting Settings
Answer: B
Explanation:
Reference: https://www.paloaHYPERLINK
"https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/getting-started/enable-autofocus-threat-intelligence"ltonetworks.com/documentation/71/pan-os/pan-os/getting-started/enable-autofocus-threat-intelligence
NEW QUESTION 8
An administrator needs to upgrade an NGFW to the most current version of PAN-OS® software. The following is occurring:
•Firewall has Internet connectivity through e1/1.
•Default security rules and security rules allowing all SSL and web-browsing traffic to and from any zone.
•Service route is configured, sourcing update traffic from e1/1.
•A communication error appears in the System logs when updates are performed.
•Download does not complete.
What must be configured to enable the firewall to download the current version of PAN-OS software?
- A. DNS settings for the firewall to use for resolution
- B. scheduler for timed downloads of PAN-OS software
- C. static route pointing application PaloAlto-updates to the update servers
- D. Security policy rule allowing PaloAlto-updates as the application
Answer: D
NEW QUESTION 9
Which GlobalProtect Client connect method requires the distribution and use of machine certificates?
- A. User-logon (Always on)
- B. At-boot
- C. On-demand
- D. Pre-logon
Answer: D
NEW QUESTION 10
Which three authentication factors does PAN-OS® software support for MFA (Choose three.)
- A. Push
- B. Pull
- C. Okta Adaptive
- D. Voice E.SMS
Answer: ADE
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/authentication/configure-multi-factor-authentication
NEW QUESTION 11
Which feature can be configured on VM-Series firewalls?
- A. aggregate interfaces
- B. machine learning
- C. multiple virtual systems
- D. GlobalProtect
Answer: D
NEW QUESTION 12
A host attached to ethernet1/3 cannot access the internet. The default gateway is attached to ethernet1/4. After troubleshooting. It is determined that traffic cannot pass from the ethernet1/3 to ethernet1/4. What can be the cause of the problem?
- A. DHCP has been set to Auto.
- B. Interface ethernet1/3 is in Layer 2 mode and interface ethernet1/4 is in Layer 3 mode.
- C. Interface ethernet1/3 and ethernet1/4 are in Virtual Wire Mode.
- D. DNS has not been properly configured on the firewall
Answer: B
NEW QUESTION 13
After pushing a security policy from Panorama to a PA-3020 firwall, the firewall administrator notices that traffic logs from the PA-3020 are not appearing in Panorama’s traffic logs. What could be the problem?
- A. A Server Profile has not been configured for logging to this Panorama device.
- B. Panorama is not licensed to receive logs from this particular firewall.
- C. The firewall is not licensed for logging to this Panorama device.
- D. None of the firwwall's policies have been assigned a Log Forwarding profile
Answer: D
NEW QUESTION 14
An administrator logs in to the Palo Alto Networks NGFW and reports that the WebUI is missing the Policies tab. Which profile is the cause of the missing Policies tab?
- A. Admin Role
- B. WebUI
- C. Authentication
- D. Authorization
Answer: A
NEW QUESTION 15
If an administrator wants to decrypt SMTP traffic and possesses the server’s certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/decryption/configure-ssl-inbound-inspection
NEW QUESTION 16
What must be used in Security Policy Rule that contain addresses where NAT policy applies?
- A. Pre-NAT addresse and Pre-NAT zones
- B. Post-NAT addresse and Post-Nat zones
- C. Pre-NAT addresse and Post-Nat zones
- D. Post-Nat addresses and Pre-NAT zones
Answer: C
NEW QUESTION 17
An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on any port. Which log entry can the administrator use to verify that sessions are being decrypted?
- A. In the details of the Traffic log entries
- B. Decryption log
- C. Data Filtering log
- D. In the details of the Threat log entries
Answer: A
Explanation:
Reference: https://live.paloaltonetworks.com/t5/Configuration-Articles/How-to-Implement-and-Test-SSL-Decryption/ta-p/59719
NEW QUESTION 18
An administrator pushes a new configuration from Panorama to a pair of firewalls that are configured as an active/passive HA pair. Which NGFW receives the configuration from Panorama?
- A. The Passive firewall, which then synchronizes to the active firewall
- B. The active firewall, which then synchronizes to the passive firewall
- C. Both the active and passive firewalls, which then synchronize with each other
- D. Both the active and passive firewalls independently, with no synchronization afterward
Answer: C
NEW QUESTION 19
An administrator sees several inbound sessions identified as unknown-tcp in the traffic logs. The administrator determines that these sessions are from external users accessing the company’s proprietary accounting application. The administrator wants to reliably identify this as their accounting application and to scan this traffic for threats. Which option would achieve this result?
- A. Create an Application Override policy and a custom threat signature for the application
- B. Create an Application Override policy
- C. Create a custom App-ID and use the "ordered conditions" check box
- D. Create a custom App ID and enable scanning on the advanced tab
Answer: A
NEW QUESTION 20
What are three possible verdicts that WildFire can provide for an analyzed sample? (Choose three)
- A. Clean
- B. Bengin
- C. Adware
- D. Suspicious
- E. Grayware
- F. Malware
Answer: BEF
Explanation:
https://www.paloaltonetworks.com/documentation/70/pan-HYPERLINK "https://www.paloaltonetworks.com/documentation/70/pan-os/newfeaturesguide/wildfire-features/wildfire-grayware-verdict"os/newfeaturesguide/wildfire-features/wildfire-grayware-verdict
NEW QUESTION 21
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against external hosts attempting to exploit a flaw in an operating system on an internal system. Which Security Profile type will prevent this attack?
- A. Vulnerability Protection
- B. Anti-Spyware
- C. URL Filtering
- D. Antivirus
Answer: A
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/objects/objects-security-profiles-vulnerability-protection
NEW QUESTION 22
Which logs enable a firewall administrator to determine whether a session was decrypted?
- A. Correlated Event
- B. Traffic
- C. Decryption
- D. Security Policy
Answer: B
NEW QUESTION 23
A network Administrator needs to view the default action for a specific spyware signature. The administrator follows the tabs and menus through Objects> Security Profiles> Anti-Spyware and select default profile.
What should be done next?
- A. Click the simple-critical rule and then click the Action drop-down list.
- B. Click the Exceptions tab and then click show all signatures.
- C. View the default actions displayed in the Action column.
- D. Click the Rules tab and then look for rules with "default" in the Action column.
Answer: B
NEW QUESTION 24
Which protection feature is available only in a Zone Protection Profile?
- A. SYN Flood Protection using SYN Flood Cookies
- B. ICMP Flood Protection
- C. Port Scan Protection
- D. UDP Flood Protections
Answer: A
NEW QUESTION 25
An administrator wants a new Palo Alto Networks NGFW to obtain automatic application updates daily, so it is configured to use a scheduler for the application database. Unfortunately, they required the management network to be isolated so that it cannot reach the internet. Which configuration will enable the firewall to download and install application updates automatically?
- A. Configure a Policy Based Forwarding policy rule for the update server IP address so that traffic sourced from themanagement interfaced destined for the update servers goes out of the interface acting as your internet connection.
- B. Configure a security policy rule to allow all traffic to and from the update servers.
- C. Download and install application updates cannot be done automatically if the MGT port cannot reach the internet.
- D. Configure a service route for Palo Alto networks services that uses a dataplane interface that can route traffic to the internet, and create a security policy rule to allow the traffic from that interface to the update servers if necessary.
Answer: B
NEW QUESTION 26
Which feature must you configure to prevent users form accidentally submitting their corporate
credentials to a phishing website?
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/threat-prevention/prevent-credential-phishing
NEW QUESTION 27
An administrator creates a custom application containing Layer 7 signatures. The latest application and threat dynamic update is downloaded to the same NGFW. The update contains an application that matches the same traffic signatures as the custom application. Which application should be used to identify traffic traversing the NGFW?
- A. Custom application
- B. System logs show an application error and neither signature is used.
- C. Downloaded application
- D. Custom and downloaded application signature files are merged and both are used
Answer: A
NEW QUESTION 28
Which three firewall states are valid? (Choose three)
- A. Suspended
- B. Passive
- C. Active
- D. Pending E.Functional
Answer: ABC
NEW QUESTION 29
In which two types of deployment is active/active HA configuration supported? (Choose two.)
- A. TAP mode
- B. Layer 2 mode
- C. Virtual Wire mode
- D. Layer 3 mode
Answer: CD
NEW QUESTION 30
......
P.S. Easily pass PCNSE Exam with 255 Q&As Dumpscollection Dumps & pdf Version, Welcome to Download the Newest Dumpscollection PCNSE Dumps: http://www.dumpscollection.net/dumps/PCNSE/ (255 New Questions)
