We provide which are the best for clearing PCNSE7 test, and to get certified by Paloalto Networks Palo Alto Networks Certified Network Security Engineer. The covers all the knowledge points of the real PCNSE7 exam. Crack your Paloalto Networks PCNSE7 Exam with latest dumps, guaranteed!
Free demo questions for Paloalto Networks PCNSE7 Exam Dumps Below:
NEW QUESTION 1
A network security engineer has a requirement to allow an external server to access an internal web server. The internal web server must also initiate connections with the external server.
What can be done to simplify the NAT policy?
- A. Configure ECMP to handle matching NAT traffic
- B. Configure a NAT Policy rule with Dynamic IP and Port
- C. Create a new Source NAT Policy rule that matches the existing traffic and enable the Bi- directional option
- D. Create a new Destination NAT Policy rule that matches the existing traffic and enable the Bi-directional option
Answer: C
Explanation: https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/networking/nat-configuration-examples
NEW QUESTION 2
An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home and experiencing issues completing the connection. the following is the output from the command: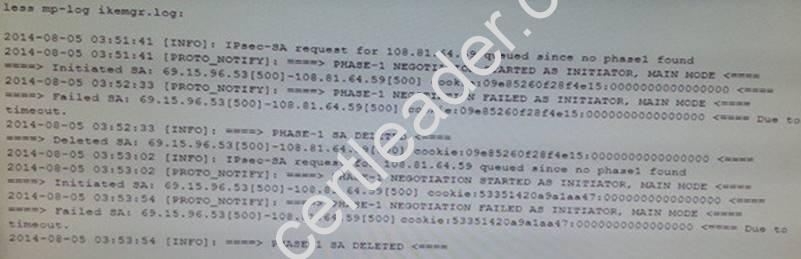
What could be the cause of this problem?
- A. The dead peer detection settings do not match between the Palo Alto Networks Firewall and the ASA.
- B. The Proxy IDs on the Palo Alto Networks Firewall do not match the setting on the ASA.
- C. The public IP addresses do not match for both the Palo Alto Networks Firewall and the ASA.
- D. The shared secrets do not match between the Palo Alto Networks Firewall and the ASA.
Answer: C
NEW QUESTION 3
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of reconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
- A. Preconfigured GlobalProtect satellite
- B. Preconfigured GlobalProtect client
- C. Preconfigured PIsec tunnels
- D. Preconfigured PPTP Tunnels
Answer: A
NEW QUESTION 4
A company hosts a publically accessible web server behind a Palo Alto Networks next generation firewall with the following configuration information.
✑ Users outside the company are in the "Untrust-L3" zone
✑ The web server physically resides in the "Trust-L3" zone.
✑ Web server public IP address: 23.54.6.10
✑ Web server private IP address: 192.168.1.10
Which two items must be NAT policy contain to allow users in the untrust-L3 zone to access the web server? (Choose two)
- A. Untrust-L3 for both Source and Destination zone
- B. Destination IP of 192.168.1.10
- C. Untrust-L3 for Source Zone and Trust-L3 for Destination Zone
- D. Destination IP of 23.54.6.10
Answer: CD
NEW QUESTION 5
Which CLI command displays the current management plane memory utilization?
- A. > debug management-server show
- B. > show running resource-monitor
- C. > show system info
- D. > show system resources
Answer: D
Explanation: https://live.paloaltonetworks.com/t5/Learning-Articles/How-to-Interpret-show-system-resources/ta-p/59364
"The command show system resources gives a snapshot of Management Plane (MP) resource utilization including memory and CPU. This is similar to the ‘top’ command in Linux."https://live.paloaltonetworks.com/t5/Learning-Articles/How-to-Interpret-show-system-resources/ta-p/59364
NEW QUESTION 6
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
- A. Red Hat Enterprise Virtualization (RHEV)
- B. Kernel Virtualization Module (KVM)
- C. Boot Strap Virtualization Module (BSVM)
- D. Microsoft Hyper-V
Answer: BD
NEW QUESTION 7
Which feature prevents the submission of corporate login information into website forms?
- A. Data filtering
- B. User-ID
- C. File blocking
- D. Credential phishing prevention
Answer: D
NEW QUESTION 8
A firewall administrator has completed most of the steps required to provision a standalone Palo Alto Networks Next-Generation Firewall. As a final step, the administrator wants to test one of the security policies.
Which CLI command syntax will display the rule that matches the test?
- A. test security -policy- match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number
- B. show security rule source <ip_address> destination <IP_address> destination port <portnumber> protocol <protocol number>
- C. test security rule source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>
- D. show security-policy-match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>test security-policy-match source
Answer: A
Explanation: test security-policy-match source <source IP> destination <destination IP> protocol <protocol number>
https://live.paloaltonetworks.com/t5/Management-Articles/How-to-Test-Which-Security- Policy-Applies-to-a-Traffic-Flow/ta-p/53693
NEW QUESTION 9
An administrator needs to upgrade a Palo Alto Networks NGFW to the most current version of PAN-OS® software. The firewall has internet connectivity through an Ethernet interface, but no internet connectivity from the management interface. The Security policy has the default security rules and a rule that allows all web-browsing traffic from any to any zone.
What must the administrator configure so that the PAN-OS® software can be upgraded?
- A. Security policy rule
- B. CRL
- C. Service route
- D. Scheduler
Answer: A
NEW QUESTION 10
Which feature must you configure to prevent users form accidentally submitting their corporate credentials to a phishing website?
- A. URL Filtering profile
- B. Zone Protection profile
- C. Anti-Spyware profile
- D. Vulnerability Protection profile
Answer: A
NEW QUESTION 11
What are three valid actions in a File Blocking Profile? (Choose three)
- A. Forward
- B. Block
- C. Alret
- D. Upload
- E. Reset-both
- F. Continue
Answer: ABC
Explanation: https://live.paloaltonetworks.com/t5/Configuration-Articles/File-Blocking-Rulebase-and-Action-Precedence/ta-p/53623
NEW QUESTION 12
Which Security policy rule will allow an admin to block facebook chat but allow Facebook in general?
- A. Deny application facebook-chat before allowing application facebook
- B. Deny application facebook on top
- C. Allow application facebook on top
- D. Allow application facebook before denying application facebook-chat
Answer: A
NEW QUESTION 13
An administrator creates an SSL decryption rule decrypting traffic on all ports. The administrator also creates a Security policy rule allowing only the applications DNS, SSL, and web-browsing.
The administrator generates three encrypted BitTorrent connections and checks the Traffic logs. There are three entries. The first entry shows traffic dropped as application Unknown. The next two entries show traffic allowed as application SSL.
Which action will stop the second and subsequent encrypted BitTorrent connections from being allowed as SSL?
- A. Create a decryption rule matching the encrypted BitTorrent traffic with action “No- Decrypt,” and place the rule at the top of the Decryption policy.
- B. Create a Security policy rule that matches application “encrypted BitTorrent” and place the rule at the top of the Security policy.
- C. Disable the exclude cache option for the firewall.
- D. Create a Decryption Profile to block traffic using unsupported cyphers, and attach theprofile to the decryption rule.
Answer: D
NEW QUESTION 14
Which three rule types are available when defining policies in Panorama? (Choose three.)
- A. Pre Rules
- B. Post Rules
- C. Default Rules
- D. Stealth Rules
- E. Clean Up Rules
Answer: ABC
Explanation: https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/panorama-web-interface/defining-policies-on-panorama
NEW QUESTION 15
Which two mechanisms help prevent a spilt brain scenario an Active/Passive High Availability (HA) pair? (Choose two)
- A. Configure the management interface as HA3 Backup
- B. Configure Ethernet 1/1 as HA1 Backup CConfigure Ethernet 1/1 as HA2 Backup
- C. Configure the management interface as HA2 Backup
- D. Configure the management interface as HA1 Backup
- E. Configure ethernet1/1 as HA3 Backup
Answer: BE
NEW QUESTION 16
Which setting allow a DOS protection profile to limit the maximum concurrent sessions from a source IP address?
- A. Set the type to Aggregate, clear the session’s box and set the Maximum concurrent Sessions to 4000.
- B. Set the type to Classified, clear the session’s box and set the Maximum concurrent Sessions to 4000.
- C. Set the type Classified, check the Sessions box and set the Maximum concurrent Sessions to 4000.
- D. Set the type to aggregate, check the Sessions box and set the Maximum concurrent Sessions to 4000.
Answer: C
NEW QUESTION 17
A distributed log collection deployment has dedicated log Collectors. A developer needs a
device to send logs to Panorama instead of sending logs to the Collector Group. What should be done first?
- A. Remove the cable from the management interface, reload the log Collector and then re- connect that cable
- B. Contact Palo Alto Networks Support team to enter kernel mode commands to allow adjustments
- C. remove the device from the Collector Group
- D. Revert to a previous configuration
Answer: C
NEW QUESTION 18
An administrator sees several inbound sessions identified as unknown-tcp in the Traffic logs. The administrator determines that these sessions are form external users accessing the company’s proprietary accounting application. The administrator wants to reliably identify this traffic as their accounting application and to scan this traffic for threats.
Which option would achieve this result?
- A. Create a custom App-ID and enable scanning on the advanced tab.
- B. Create an Application Override policy.
- C. Create a custom App-ID and use the “ordered conditions” check box.
- D. Create an Application Override policy and custom threat signature for the application.
Answer: A
P.S. Easily pass PCNSE7 Exam with 176 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam PCNSE7 Dumps: https://www.surepassexam.com/PCNSE7-exam-dumps.html (176 New Questions)
