Master the SC-100 Microsoft Cybersecurity Architect content and be ready for exam day success quickly with this Certleader SC-100 download. We guarantee it!We make it a reality and give you real SC-100 questions in our Microsoft SC-100 braindumps.Latest 100% VALID Microsoft SC-100 Exam Questions Dumps at below page. You can use our Microsoft SC-100 braindumps and pass your exam.
Check SC-100 free dumps before getting the full version:
NEW QUESTION 1
Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend creating private endpoints for the web app and the database layer. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 2
Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app.
You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection. What should you include in the recommendation?
- A. interactive application security testing (IAST)
- B. static application security testing (SAST)
- C. runtime application se/f-protection (RASP)
- D. dynamic application security testing (DAST)
Answer: A
NEW QUESTION 3
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface.
What should you include in the recommendation?
- A. Azure Firewall Premium
- B. Azure Application Gateway Web Application Firewall (WAF)
- C. network security groups (NSGs)
- D. Azure Traffic Manager and application security groups
Answer: D
NEW QUESTION 4
Your company is developing a modern application that will run as an Azure App Service web app. You plan to perform threat modeling to identify potential security issues by using the Microsoft Threat Modeling Tool.
Which type of diagram should you create?
- A. dataflow
- B. system flow
- C. process flow
- D. network flow
Answer: C
NEW QUESTION 5
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD)
The customer plans to obtain an Azure subscription and provision several Azure resources. You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
- A. role-based authorization
- B. Azure AD Privileged Identity Management (PIM)
- C. resource-based authorization
- D. Azure AD Multi-Factor Authentication
Answer: A
NEW QUESTION 6
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each NOTE: Each correct selection is worth one point.
- A. Azure Firewall
- B. Azure Web Application Firewall (WAF)
- C. Microsoft Defender for Cloud alerts
- D. Azure Active Directory (Azure AD Privileged Identity Management (PIM)
- E. Microsoft Sentinel
Answer: BD
NEW QUESTION 7
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
- A. Azure Active Directory (Azure AD) Conditional Access App Control policies
- B. OAuth app policies in Microsoft Defender for Cloud Apps
- C. app protection policies in Microsoft Endpoint Manager
- D. application control policies in Microsoft Defender for Endpoint
Answer: A
NEW QUESTION 8
Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft B65 subscription, and an Azure subscription.
The company's on-premises network contains internal web apps that use Kerberos authentication. Currently, the web apps are accessible only from the network.
You have remote users who have personal devices that run Windows 11.
You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements:
• Prevent the remote users from accessing any other resources on the network.
• Support Azure Active Directory (Azure AD) Conditional Access.
• Simplify the end-user experience.
What should you include in the recommendation?
- A. Azure AD Application Proxy
- B. Azure Virtual WAN
- C. Microsoft Tunnel
- D. web content filtering in Microsoft Defender for Endpoint
Answer: B
NEW QUESTION 9
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
- A. From Defender for Cloud, review the Azure security baseline for audit report.
- B. From Defender for Cloud, add a regulatory compliance standard.
- C. From Defender for Cloud, enable Defender for Cloud plans.
- D. From Defender for Cloud, review the secure score recommendations.
Answer: D
NEW QUESTION 10
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.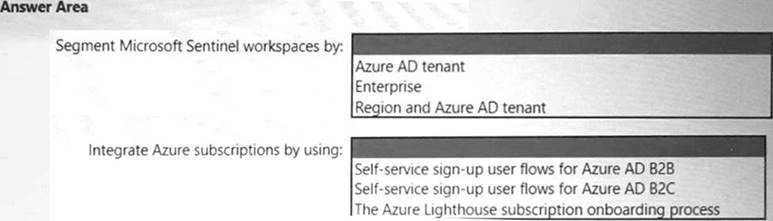
Solution:
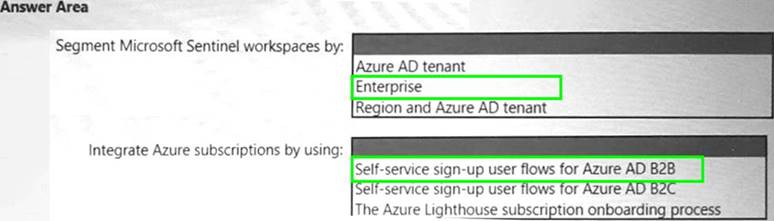
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
You have 50 Azure subscriptions.
You need to monitor resource in the subscriptions for compliance with the ISO 27001:2013 standards. The solution must minimize the effort required to modify the list of monitored policy definitions for the subscriptions.
NOTE: Each correct selection is worth one point.
- A. Assign an initiative to a management group.
- B. Assign a blueprint to each subscription.
- C. Assign a policy to each subscription.
- D. Assign a blueprint to a management group.
- E. Assign an initiative to each subscription.
- F. Assign a policy to a management group.
Answer: CD
NEW QUESTION 12
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.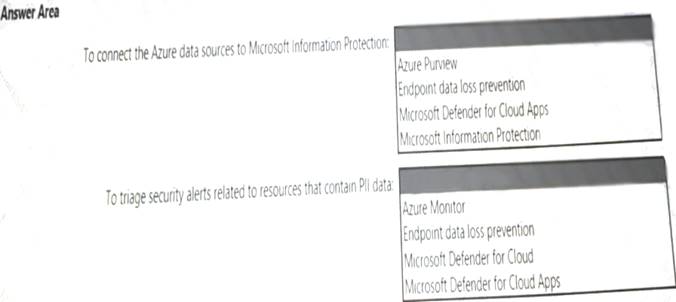
Solution:
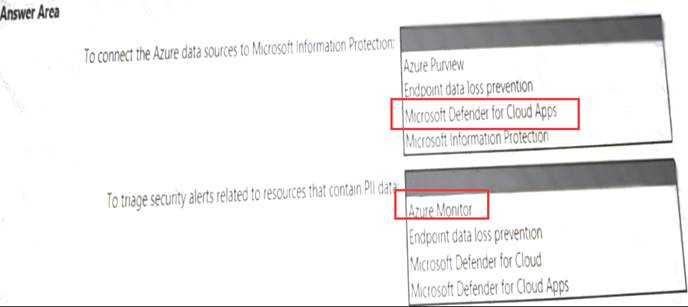
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
You have Microsoft Defender for Cloud assigned to Azure management groups. You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events, including suggestions for remediation. Which two components can you use to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. workload protections in Defender for Cloud
- B. threat intelligence reports in Defender for Cloud
- C. Microsoft Sentinel notebooks
- D. Microsoft Sentinel threat intelligence workbooks
Answer: A
NEW QUESTION 14
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 15
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatical
What should you use?
- A. the regulatory compliance dashboard in Defender for Cloud
- B. Azure Policy
- C. Azure Blueprints
- D. Azure role-based access control (Azure RBAC)
Answer: D
NEW QUESTION 16
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 17
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF). Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 18
You have a Microsoft 365 E5 subscription.
You need to recommend a solution to add a watermark to email attachments that contain sensitive data. What should you include in the recommendation?
- A. Microsoft Defender for Cloud Apps
- B. insider risk management
- C. Microsoft Information Protection
- D. Azure Purview
Answer: A
NEW QUESTION 19
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
- A. Azure Storage Analytics
- B. Azure Network Watcher
- C. Microsoft Sentinel
- D. Azure Policy
Answer: A
NEW QUESTION 20
......
Recommend!! Get the Full SC-100 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/SC-100-dumps.html (New 105 Q&As Version)
